Tip: All changes are tracked in the Gateway documentation, see the information in the last row of the documentation agreement.
This release is the last release in the 13.0 branch and enables the update to version 13.1 (all changes are also included in 13.1).
Release Date: June 02th, 2024
SEPPmail version: 13.0.17
Author: Birgit Grossmann
This ticket solves a bug that prevented the deletion of non-admin groups.
The bug prevented the assignment of GINA accounts, which were assigned to the default customer, to another customer. This is now possible again.
There was an error in the display of users when a filter string was specified as a filter. Under certain circumstances an empty list was displayed. This is now fixed.
The problem here was that the DNS search for the public DKIM key did not return a TXT but a CNAME entry. The resolver actually follows this up to the TXT entry. However, we only ever evaluated the first response and therefore only used the CNAME entry, which then led to the incorrect behavior. This is now fixed.
SORBS.net has discontinued its service. To prevent possible erroneous detections we have added code that completely ignores the SORBS lists.
This bug/maintenance ticket improves the CertCentral MPKI Connector through better error output and the preselection of the default product as well as the possibility to select the product used.
In the RuleEngine, SEPPmail Gateway has an automatism to extract the CA certificates for signed mails and, if configured, to automatically set them to "trusted". The bug here was that we did not include the new trusted certificates in the CA certificate file which is used by the software for the further run. The fix now ensures that the file is written and used correctly.
Previously, even if you set "ignore failure" for the query on an external keyserver, three attempts were made to connect to the server and the timeout was 30 seconds. So if a server was not available, delivery was delayed by at least 90 seconds. As a result, mail delivery came to a standstill for some customers. In the case of "Ignore failure", only a single connection is now established and the timeout is generally set to 5 seconds. This leads to massively reduced delays.
Release Date: May 28th, 2024
SEPPmail version: 13.0.16
Author: Birgit Grossmann
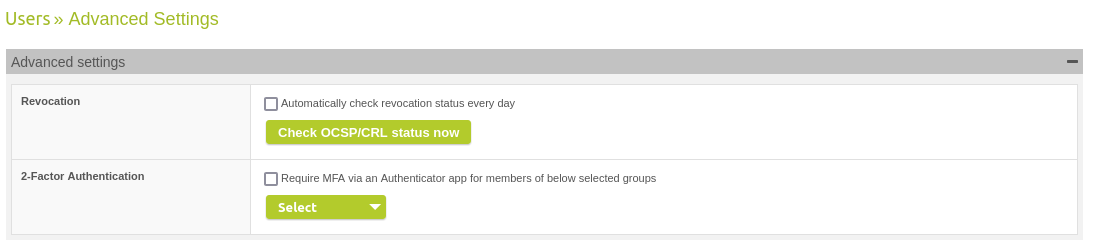
With 13.0.16 you can configure MFA / 2-factor authentication for the login to the SEPPmail Gateway Admin GUI. The feature has to be activated under "Users" > "Advanced Settings", and the local groups have to be specified for which MFA should be used. The next time the user logs in, they will be prompted to complete the 2FA setup. Afterwards, the 2FA code must be added to the password when logging in. Users can also be excluded from MFA by the setting "Disable MFA requirement".
Since "Internal authentication" is now available in the managed domains, these users can also log in to the GINA GUI with the second factor, provided that MFA is fully configured for these users.

New setting "2-Factor Authentication"
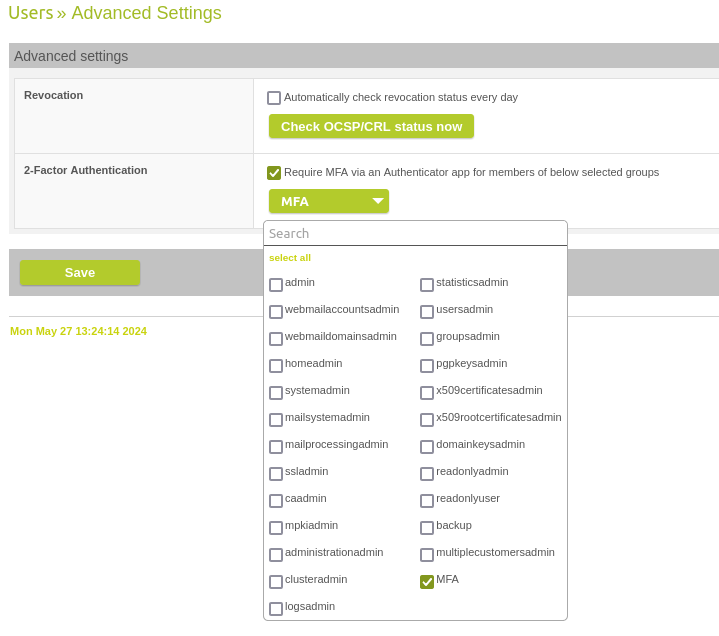
Group multi-select
There was recently a security vulnerability in various mail transport agents with regard to incorrect line endings, which resulted in mails generated by SEPPmail being rejected. SEPPmail now sets the correct line endings.
In multi-tenant environments, the users list was limited to 500 users but the users were pulled before checking if the currently logged-in user is allowed to see these users. This could result in an empty list. Now the search is always performed according to the authorised customer entries, so that all returned entries can also be displayed to the currently logged-in user.
Previously, if a PGP signature was verified but was not valid, SEPPmail did not output the full result of the verification. This is done now.
For each password mail generated by the webmail system, SEPPmail now sets the header "X-ESWmail-Password" with the value "Yes".
There was an error in the code when searching for the Authentication-Results header of ExO if a master ACR key was used in the system or for the managed domain. As a result, values from the actual managed domain were no longer available and the "parallel connected" setting could not be analysed. As a result, the Authentication-Results header from ExO was not even searched for and the ARC signature remained defective. This is fixed now.
In the partoftype() function, SEPPmail used to support a "List of file types" and "List of file groups". See also https://docs.seppmail.com/en/08_cr_06_mh_12_cm_03_pot__partoftype.html.
In the support ticket in question, someone entered "app" as the term to be searched for. This is neither in one of the lists nor a valid MIME type. However, since the match internally hits the beginning, all types of the MIME type "application/*" were found.
Before the final test, the fix now evaluates whether the type to be searched for is also a valid MIME type, i.e. begins with application|audio|chemical|example|font|image|message|model|multipart|text|video|x-content|x-epoc, followed by a '/'.
There is now an new entry "Send to last sender" in the GINA domain settings > "Admin settings" > "Password recipients" > "For registered GINA account reset:".
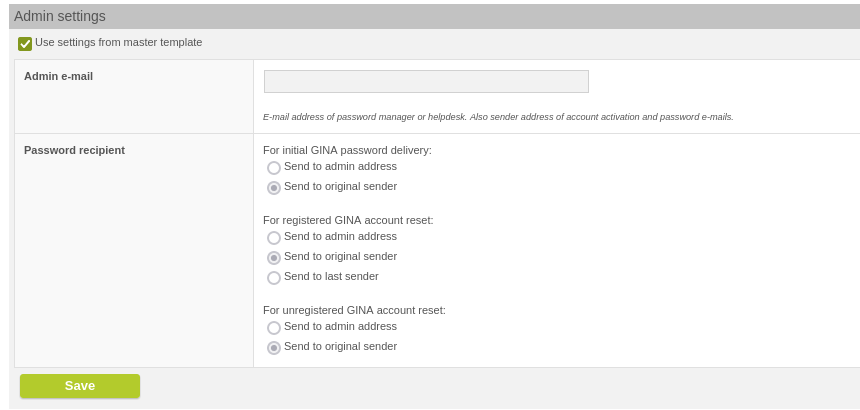
New option "Send to last sender"
In the GINA mail, the reference to the SEPPmail Viewer APP is now emphasized.
Release Date: May 13th, 2024
SEPPmail version: 13.0.15
Author: Birgit Grossmann
Due to a bug, the import of certificates with keys failed. This is fixed now.
An error in a daemon process meant that commands sent by one cluster member to another cluster member were not executed. This also prevented new cluster members from being added. This is fixed now.
Several problems have been fixed with this bugfix, e.g. not all data was synchronised in cache mode.
With 13.0.14 SEPPmail has included the result of the SPF check in the ARC seal. However, if Exchange Online is connected in parallel, there is the problem that the mail no longer comes from the original sender but from Microsoft and therefore the SPF check will fail. In this case (an incoming mail coming from Exchange Online) SEPPmail now uses the result, i.e. the Authentication-Results header from Exchange Online, to generate the ARC seal. This should also solve the problems with invalid or missing SPF results in the ARC seal in the case of a parallel connection.
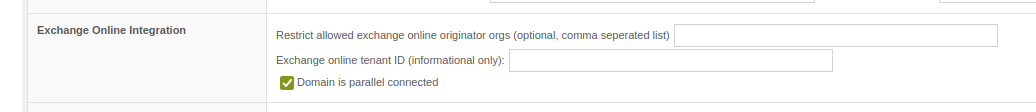
Checkbox "Domain is parallel connected"
Previously, when the RuleEngine received a new ruleset, it was completely restarted. This led to mails being rejected due to the unavailability of the RuleEngine, especially under high load. With the new uninterruptible reload, there are no more interruptions in mail processing.
In the past, PGP keys were attached to a mail as content type "text/plain". From now on, "application/pgp-keys" is used.
The problem was that under very specific circumstances the two recognition features that were used during the password reset to recognise whether a user was already fully registered were not set, but the user was already registered. As a result, the user was processed as unregistered. The query as to whether the user is registered has been improved.
With this issue, Clickatell has been added to the list of supported SMS services.
There was an error where the phone number for a user was not saved. This has now been corrected.
When downloading all attachment of a GINA mail at once, an incorrect encoding was used during ZIP file creation, so file names with e.g. umlauts were displayed incorrectly in the archive. This is fixed now.
Release Date: April 17th, 2024
SEPPmail version: 13.0.14
Author: Birgit Grossmann
When importing a ZIP file with X.509 certificates in the Admin GUI, it was not possible to select ZIP files in the browser selection dialogue. In most browsers you can override this by specifying that all files should be displayed, but not on Apple. This is why ZIP is now also in the list of formats for the import.
Detailed Description:
Until now, the SEPPmail Gateway has not paid attention to the fact that if the CfgServer log file rotates and a new log file is opened, an asynchronous task, i.e. one that is executed in the background, would also have to reopen the log file. This is done now.
Detailed Description:
It is now possible to allow local users, that is those who belong to a managed domain, to log in to the Webmail GUI. To do this, you must activate "Internal authentication" in the managed domain. If you use the mail processing groups, only users who belong to one of the selected mail processing groups are allowed to do so. If no mail processing group is selected, all users of the managed domain may authenticate themselves.
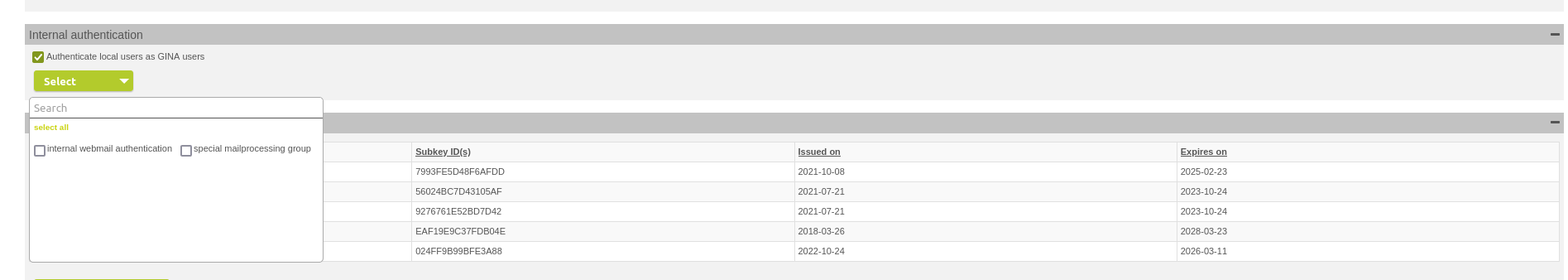
Allow internal authentication
In the GINA accounts, you can now see which type of authentication was used to create the account.
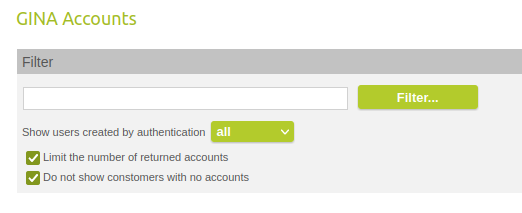
Show users created by authentication
Available values:
This information is not yet available for existing accounts, so they are displayed as unknown.
Both the cache mode and LFT have expiry dates. To prevent confusion regarding these dates, the link for the cache mode in an LFT message now expires at the same time as the LFT message itself.
Detailed Description:
The problem here was that there were at least 3 cluster members in a cluster and our load balancer was switched on at the same time. As the entries in the queries to the DB were not always in the same order (unless requested, which we only do if necessary), the command we generated for the load balancer changed from time to time. As we used this command to find out whether something had changed on the load balancer and the command was always different, the load balancer was restarted again and again. However, as the mails are transferred to the RuleEngine via the load balancer and the RuleEngine therefore also communicates the successful processing of the sending page via the balancer, problems arose when the balancer was restarted and the RuleEngine was currently processing a mail. The result were always so-called "queue file write error" messages. Now SEPPmail Gateway sorts the response of the DB and the load balancer command only changes if something has really been changed.
Detailed Description:
This bugfix is a correction in the SCEP MPKI Connector. The certificates are now always converted to PEM so that the SCEP MPKI Connector can process them.
Detailed Description:
The SCEP MPKI connection did not work because the wrong data was used in the code. Now the correct configuration data is used.
Detailed Description:
In the past, SEPPmail only correctly decoded the status messages in the response from SwissSign if the HTTP response had a 200 code. However, in the event of an error when issuing a new certificate, SwissSign issues a 400 code, which was not decoded. This is now fixed and the status messages are correctly decoded.
Detailed Description:
DigiCert and CertCentral actually allow you to use the name of the user for the CN of a certificate to be issued. Unfortunately, this always leads to problems because it is not entirely clear in which encoding the other party wants to have the name. To avoid the whole problem, SEPPmail Gateway now always sets the CN to the e-mail address.
Detailed Description:
You can now select the certificate type or contract in the CertCentral MPKI connector. The API key and Org-ID are also verified.
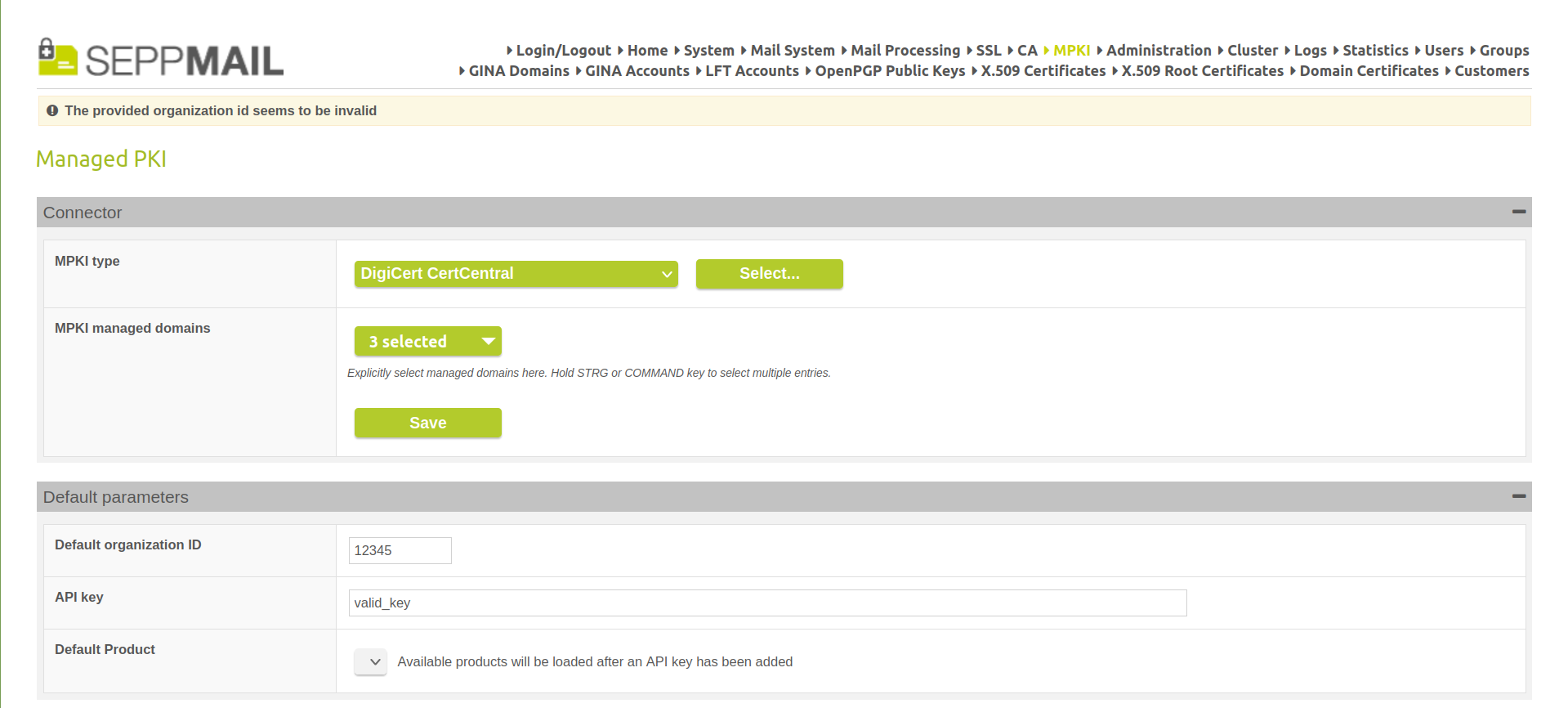
Select DigiCert CertCentral type/contract
Detailed Description:
During installation, a partition is now assigned to /tmp.
Detailed Description:
A bug in the RestAPI prevented the -NONE- disclaimer from being saved in a managed domain. This is possible now.
Detailed Description:
An error in the RestAPI caused data to be ignored and the information for "initial password recipient" not to be saved. This is fixed now.
Detailed Description:
An error in the RestAPI prevented the saving of language settings. This is possible now.
Detailed Description:
Before SEPPmail adds the ARC seal to the mail, it now performs an SPF check and adds the result to the Authentication-Results header so that the ARC seal contains the result of the SPF check.
Detailed Description:
Postfix has its own job ID for each mail with a queue ID and SEPPmail has a different, consecutive number. Normally a log line is output containing the Postfix queue ID and the SEPPmail job ID so that a connection can be established later. The error so far was that SEPPmail assumed a 6-digit job ID, i.e. the log line was only added from mail 100000 due to a faulty regex. Now the log line is available from mail 1.
Detailed Description:
The LDAP filter to determine the licence limit for Customer was faulty and as a result, the limit was not calculated correctly. This has now been fixed.
Detailed Description:
Previously, a user who authenticated himself to SMTP via user/password was still prevented from relaying if the "originator orgs" setting was configured for his managed domain. When a user now has authenticated himself via SMTP, this is recognised as a sufficient characteristic for relaying.
Detailed Description:
A 3rd party module used by SEPPmail Gateway compares a lower-case domain name with a passed domain name. This led to problems if the passed domain name contained capital letters. SEPPmail now also passes lower-case, so that the comparison can be performed correctly.
Detailed Description:
Processing in the RuleEngine using a regular expression caused a problem if the mail address contained a special character that is relevant for regular expressions. In this case the '+', which corresponds to the quantifier "one or more times". Now the mail address is correctly escaped so that these special characters are no longer interpreted by the regex.
Detailed Description:
Until now, the RuleEngine prevented the automatic creation of users from containing an '&' in a mail address. From now on, we support all characters that may appear in a mail address, including '&'.
Detailed Description:
In order to use SMIME 4, a different cipher is required for the encryption, which also takes the integrity of the data into account. This way, the data is not only encrypted but any manipulation of this data is also noticeable. This is supported with the newly supported GCM ciphers.
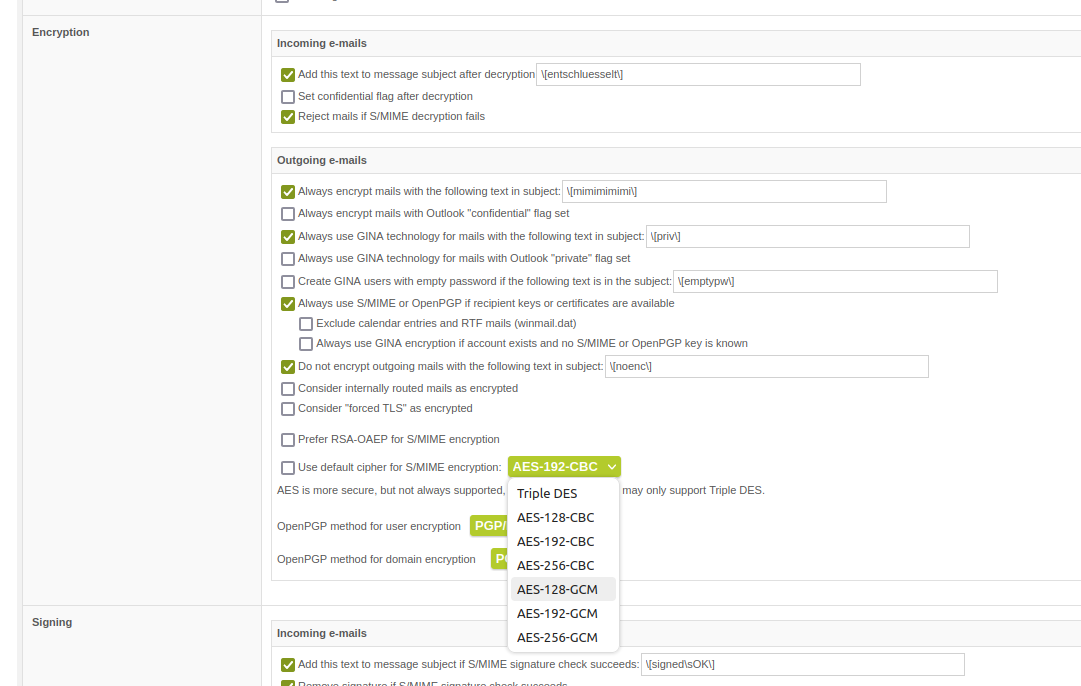
List of supported ciphers
Detailed Description:
After the configuration of DKIM in the Admin GUI, a DNS lookup and comparison with the public DKIM key takes place. In the past, accidentially included line breaks in the entered DKIM key broke this comparison. The DNS lookup can now handle line breaks.
Detailed Description:
It was previously not possible to configure the texts for the cache mode for the carrier mail. This is now possible. The text is handled in the same way as normal GINA texts.
Detailed Description:
The subtitle was missing in the carrier mail in cache mode. This is fixed again now.
Detailed Description:
This fixes a bug where a reply with a GINA message attachment was not possible in the GINA GUI.
Detailed Description:
Previously, when a domain certificate was downloaded via the GINA GUI and this certificate was issued by the local CA, SEPPmail first wrote the local CA certificate to the resulting PEM file and then the domain certificate. This leads to problems with some systems, as they first (or sometimes only) regard the first certificate in the file as the relevant one and therefore use the CA certificate instead of the domain certificate. Now the order is reversed so that the domain certificate is written first.
Detailed Description:
In the GINA GUI it is now possible to download all attachments at once as a ZIP.
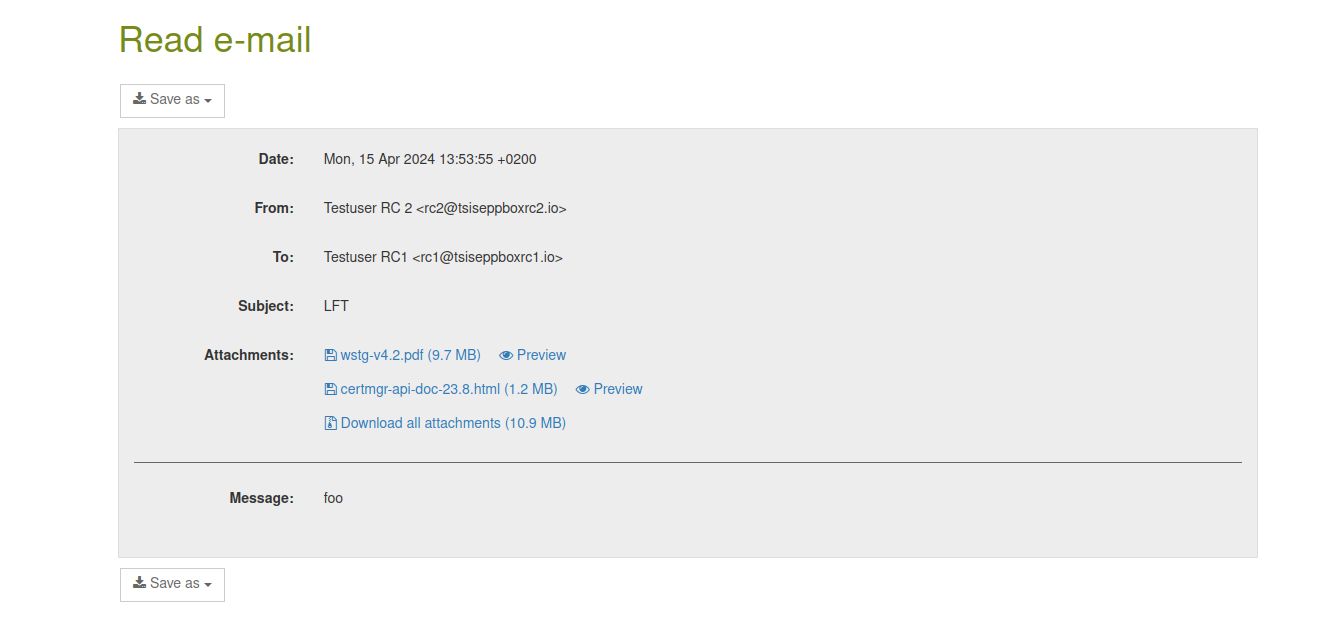
Download all attachments as ZIP via "Save as"
Detailed Description:
The Cache-Control HTTP header was added for GINA.
Detailed Description:
In cache mode, it can be specified for each GINA domain how long the mails should be cached. Unfortunately, the mails in the cache lacked information about which GINA domain they belonged to and so the cached entries were deleted from GINA domains that were not actually allowed to do so, as these entries did not belong to them. The domain affiliation is now taken into consideration.
Release Date: February 21th, 2024
SEPPmail version: 13.0.13
Author: Birgit Grossmann
Detailed Description:
There was a display issue, mainly for the detail view of certificates. The problem was that SEPPmail never handled UTF8 encoded DirectoryStrings properly after parsing the ASN1 structure of an X.509 certificate. This is fixed now.
Detailed Description:
Due to a bug, it was temporarily not possible to delete attachments and inlines in configured disclaimers. This is now possible again.
Detailed Description:
In the log lines that list which mechanisms were used for encryption or signing, only the issuer and the serial number of the certificate used were output in the past. Now SEPPmail also searches for the certificate in the database and outputs the SHA256 fingerprint if available. This is done because the SHA256 fingerprint is used everywhere in the Admin GUI as an identification feature, making it easier and standardised to search for the certificates used.
Detailed Description:
If no CA has been configured on the SEPPmail Gateway and a domain certificate is created for a managed domain, the certificate is signed/created by an internal fallback CA. As this is not trustworthy, we prevent the download of a domain certificate created with this CA via the GINA GUI.
Detailed Description:
A slash '/' was probably erroneously appended to the end of the proxy URL for the OCSP proxy. This led to problems. Therefore the '/' has now been removed.
Detailed Description:
In the "deliver" function in the RuleEngine there was an error when
If all these conditions were met, the mail was previously split into several mails (per domain) but only handled correctly for one domain. The others were simply processed further in the RuleEngine. With the correction, all mails are now processed.
Detailed Description:
The vulnerability SMTP smuggling was fixed in one of the previous versions by an update and patch of Postfix, so that SEPPmail rejects corresponding mails. In the case of a "reprocessed" mail, however, SEPPmail itself didn't behave correctly and so Postfix rejected our own mails. With the fix, the "reprocess" works again because the line endings are correctly set to CRLF.
Detailed Description:
With 13.0.12 SEPPmail has introduced a new module for parsing mail addresses. However, this had problems with mail address details with display names and resulted in no mail address being recognised. This is fixed now and mail addresses are detected correctly again.
Release Date: January 30th, 2024
SEPPmail version: 13.0.12
Author: Birgit Grossmann
Detailed Description:
If the setting "Create S/MIME domain keys for managed domain encryption and send public key to vendor pool: Use Domain Settings" (for new oder existing domains) was selected, the setting "Autopublish switched off" remained checked, although the function was actually active. This was a display error and is fixed now.
Detailed Description:
With 13.0.11, we have changed the behaviour of LDAP to make a checkpoint every minute. This causes, especially on some hardware appliances, a hiccup of up to 15-20 seconds which will influence the system's accessibility, its hardware clock (sometimes) and therefore the whole performance. This has to do with the maximum size of LDAP database or at least correlates with it. Some customers have only 200MB data in their DB but we allocated a 100GB database. Syncing this 100GB takes much longer than just a 2GB database. Therefore, SEPPmail Gateway now creates the maximum size value in a more differentiated way instead of allocating the entire partition.
Detailed Description:
There was an error in SEPPmail Gateway so subdomains were not handled. Because of this is was not possible to issue new certificates for subdomains of validated domains. This is fixed now.
Detailed Description:
The error was that some incoming E-mails with unusual but valid mail addresses were falsely categorized and processed as outgoing. The reason was that the E-mail addresses could not be parsed and therefore SEPPmail Gateway did not get the domain name and could not look up the managed domain. The E-mail address parsing has been improved now.
Release Date: January 17th, 2024
SEPPmail version: 13.0.11
Author: Birgit Grossmann
Detailed Description:
There was an error in the restart behavior of the RuleEngine after a RuleSet change. This is fixed now.
Detailed Description:
If a new certificate was obtained via the MPKI, it usually arrives in PKCS7 format. The parser which processed the certificates contained in the PKCS7 had an error and ignored the new certificate, so it was not imported. This is fixed now.
Release Date: January 16th, 2024
SEPPmail version: 13.0.10
Author: Birgit Grossmann
xyzabc.dkfz.org: no smarthost specifiedDetailed Description:
Due to an error in version 13.0.9, entering a smarthost was mandatory when creating a managed domain. Now the smarthost can be left empty as usual.
Detailed Description:
In the Logs screen, there was a wrong link to "Delete mail log archive cache". The link is now corrected to "Delete mail log archive index".
Detailed Description:
There was a display error in the SEPPmail Gateway Admin GUI with German Umlauts in the user's full name. This is fixed now.
Detailed Description:
As of 13.0.9, the IP addresses in "Mail System" > "Relaying allowed" unexpectedly asked for a different formatting pattern. This is fixed now back to the original behavior as in 13.0.7.
Detailed Description:
When connecting the SEPPmail Gateway to Microsoft 365/Exchange Online, signatures that have already been checked should always be truncated, because when Microsoft checks the content of the email, it may be changed and the signature would be destroyed. Furthermore, a possibly existing ARC seal could be damaged if an S/MIME signature is present. This in turn would result in an email being mistakenly placed in the Office 365 quarantine.
Detailed Description:
There was an update for OpenSSH in December fixing a security issue. Since there were no patches for the OpenSSH version used in the old releases, SEPPmail had to update to version 9.5 and use the patches for this version.
Detailed Description:
To stay in sync with the default implementation, SEPPmail Gateway now will only use the following headers for the ARC signature: "
content-transfer-encoding:subject:from:to:content-language:user-agent:mime-version:date:message-id". Even if the header does not exist in the mail, SEPPmail Gateway will add the header to the signature to detect if someone added it afterwards.
Detailed Description:
In the past, the SEPPmail Gateway used a random value to generate new Message ID header values from the old Message ID header, by appending the random value to the end of the old value. In the case of retransmissions/double deliveries, this caused the receiving mail server to process the retransmission as a separate new mail instead of ignoring it because there was already a message with this Message ID. As of 13.0.10, reproducible Message IDs are created when a new message is generated.
Detailed Description:
There was a bug with the usage of the master ARC key. Now, when using the master ARC key, the configured domain of the master ARC key is used.
Detailed Description:
The bug "Display error with German Umlauts in the full name" described in the Admin section above also had effects on the automatic certificate creation in the RuleEngine. This is also fixed now.
Detailed Description:
Despite enforced reading confirmation in GINA, the confirmation was not always sent. This is fixed now.
Release Date: November 23rd, 2023
SEPPmail version: 13.0.9
Author: Roland Muehlbauer
Detailed Description:
When removing users, statistic data is also deleted from now on. This prevents the behavior that if you delete and recreate a user, the statistics data of the original user is shown. Now the statistics are reset and a new user has under no circumstances statistics of a deleted user.
Detailed Description:
Under certain conditions, the configured outgoing server was not used anymore after an upgrade to 13.0.8.
Detailed Description:
DKIM checks require DNS lookups. As we have no control over the duration of the query, we adapted the Log message to understand this was a DNS query timeout.
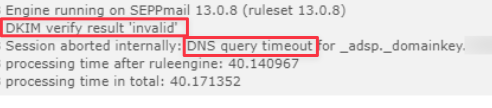
A log entry showing the issue we fixed
Detailed Description:
In situations when the delivery and the reading of a GINA mail has a broader time span, the information about the initial password may have been lost between sender and recipient. This can be avoided when the initial password email is sent in the moment when the GINA recipient opens the mail for the first time. This is when the password is needed and this is the moment it is generated.
Release Date: November 15th, 2023
SEPPmail version: 13.0.8
Author: Birgit Grossmann
Detailed Description:
It is now possible to enter the network 0.0.0.0/0 as the relaying network in the managed domain settings to enable the sending of e-mails from an external web server, for example. Please use with care.
Detailed Description:
SHA256 fingerprint is now used everywhere as an identifier for S/MIME certificates, both in the Admin GUI lists and in the RuleEngine logs.
Detailed Description:
You can now display only the active or inactive users in the user list. Three options are available: "all", "active", or "inactive". The default is "all".
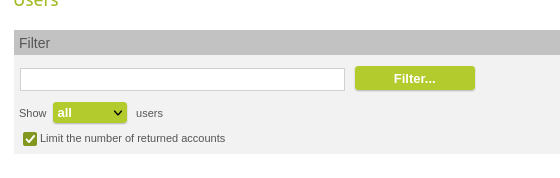
filter by user status
Detailed description:
Optionally, a separate certificate can now be specified for each managed domain for encrypting SMTP traffic via TLS. This enables the use of Certificate Based Connectors (CBC), especially in MSP installations. This is a workaround for incorrect routing on the part of Microsoft, which causes emails to end up with the wrong client if the tenant of the sender and the tenant of the recipient are hosted in the same forest.
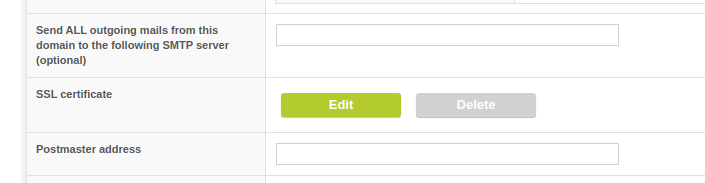
add SSL per managed domain
When using CBCs, the CN of the certificate entered here must be manually transferred to the "[SEPPmail] Appliance -> Exchange Online" connector.
Detailed description:
When trying to activate the option "Automatically renew expiring certificates if validity days left less than", it appeared disabled in the GUI after saving, although the value was saved. This is fixed now.
Detailed description:
CertCentral could not cope with UTF-8 encoded names or common names. This is fixed now, they are no encoded correctly.
Detailed description:
Under certain circumstances it is necessary to set the validation status to HIGH in the Sectigo MPKI Connector when a certificate is issued for the user for whom the certificate is stored in Sectigo. This is actually a setting in the Sectigo profile for the certificates to be issued.
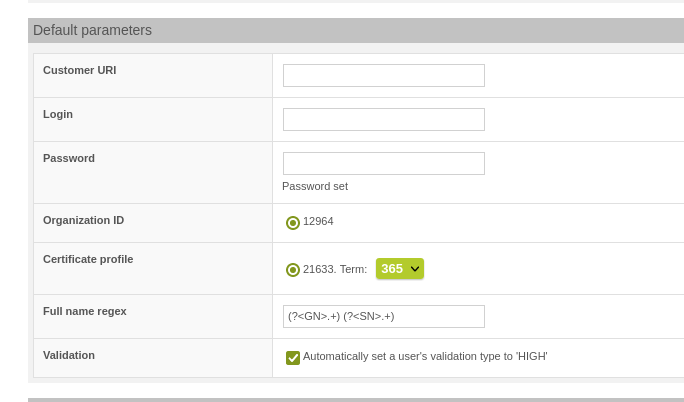
Validation "high" for Sectigo user
Detailed description:
Since DigiCert and CertCentral do not use the static subject part, the inputs are no longer used.
Detailed description:
The RestAPI endpoint for uploading custom commands works with a different character encoding than was necessary for saving in LDAP. The old way of saving such values has been revised internally so that these coding errors can no longer occur.
Detailed description:
It is now possible again to make any user the admin of a customer, even if this user is not a member of the customer.
Detailed description:
The RuleEngine function logsubject() now also outputs the list of attached attachments, their content type and their size. Example:
Message Subject is [confidential] test HTML mail with Attachment
Message Size is 161KB
Message has 1 attachment(s)
1. attachment: name=autohack-768x768.jpg, mime-type=image/jpeg, size=136478
Message has 1 inline(s)
1. inline: name=anker.png, mime-type=image/png, size=26740
Detailed description:
Compatibility with LDAP queries has been refined and extended to cover special cases. One example is certain users in a group that need to be queried. Here, the new ldap_compare user can be filtered more specifically. No customer action is necessary.
Detailed description:
ARC sealing/signing of emails is now possible. Especially in conjunction with Exchange Online connections, this can reduce/eliminate false positives in spam detection by Microsoft.
Special note for ExO tenants: In a MIME-structured mail, there might be some additional lines for non-MIME clients like "This is an S/MIME signed message" or "This is a multi-part message in MIME format." These lines are included in the ARC-Message-Signature. For reasons as yet unknown, ExO removes these lines which results in an invalid ARC-Message-Signature. The mail then consequently fails the Microsoft DMARC check. We are currently in contact with Microsoft to solve this issue.
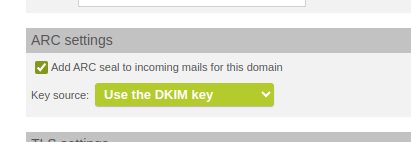
activate ARC seal
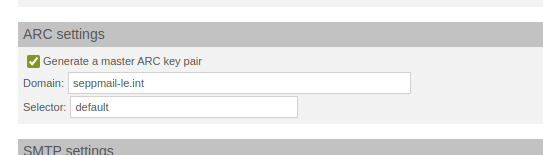
configure master ARC key
Detailed description:
Incoming emails from the sender with a spoof tag, e.g. [HIN secured], are checked by the appliance and this tag is removed. This function had an error that also deleted all subject text after the tag. This is fixed now.
Detailed description:
TLS-secured DNS queries (DNSSEC) have been implemented. Possible values for the validation are yes, no, or auto.
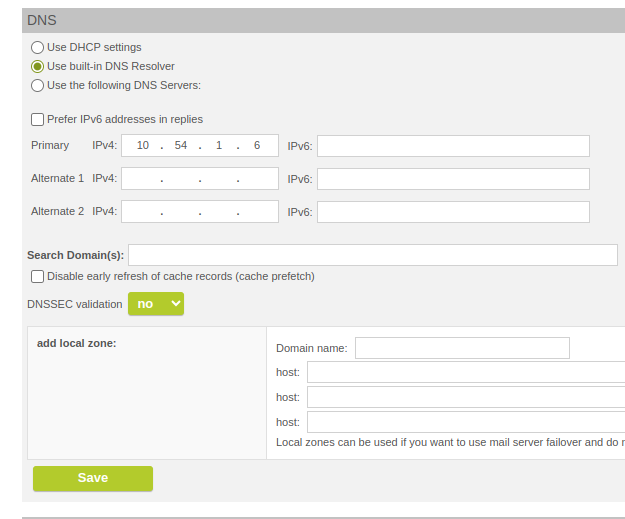
Option "DNSSEC validation"
Detailed description:
In the past, a placeholder text appeared in the GINA mails if the header and footer logos were not customised. This has been removed.
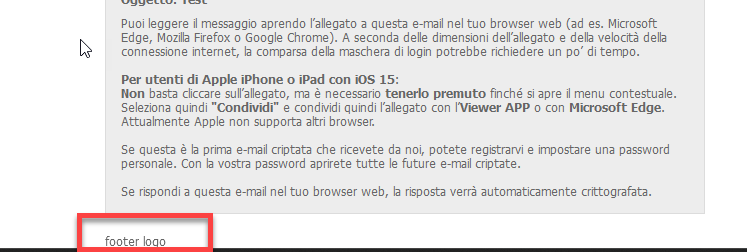
former "footer.logo" text display
Detailed description:
The SEPPMail Gateway was adapted to the OAuth 2.0 changes implemented by LinkedIn.
Detailed description:
If, for example, SAML/OAuth authentication is to be used for the LFT bypass login in the Outlook add-in, but the button for the SAML login is not to be displayed in the GINA login of the web interface, this display can now be suppressed. The setting is available in the GINA settings per domain.
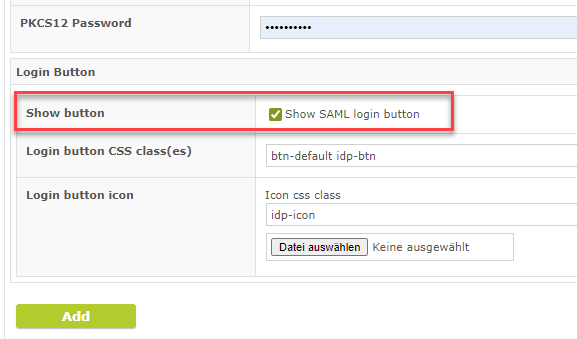
Checkbox "Show SAML login button"
Detailed description:
The link to the GINA explanatory video was removed from the GINA carrier email Position was msgid "webmailtext_text" in GINA Translation File, msgstr paragraph:
Please also consider watching our Youtube Explanation Video (German only).
This only affects the standard e-mail template. Already customized templates are unaffected. Furthermore, a new video is available under https://vimeo.com/847984884 and can be implemented optionally.
Release Date: September 25th, 2023
SEPPmail version: 13.0.7
Author: Birgit Grossmann
Detailed Description:
The problem was that whatever the user configured for the TLS level, when they switched to the Managed Domain configuration screen, the TLS level was shown as "Encrypt: Only send mail if TLS encryption is possible". This is fixed now.
Detailed description:
SHA1 is no longer defined as secure, so beginning with 13.0.7, we store new passwords with SHA512 in the backend.
Detailed description:
The way Amazon Web Services handles network connectivity, required a special configuration to receive a DHCP IP address. This is fixes now, so 13.0.7+ works on AWS (again).
Detailed description:
When using Syslog Server, the field-length for the syslog-settings was limited to 63 characters. This limitation has been dropped.
Detailed Description:
Due to the new requirements of the Browser CA Forum, the DigiCert certificate issuing API was changed. The SEPPmail Gateway now has a new DigiCert CertCentral MPKI connector to continue to allow automatic issuing via the DigiCert infrastructure. The configuration is identical to the previous DigiCert configuration.
Detailed Description:
This change reflects the updates of Quovadis Trustlinks to Digicert CertCentral. The new UI on SEPPmail appliance can be found below:
The settings at the CA looks like the screenshot below:
Detailed Description:
In the past, all PGP keys were fetched and the last one was taken into the array. However, this array was not sorted, so that just any key was used for the PGP signature. Now the result is sorted according to the expire date and the longest running key is used.
Detailed Description:
Due to a wrong search pattern, GINA cache mode did not work in the cluster. This is now fixed.
Detailed Description:
Fix for CVE-2020-11022 CVE-2020-11023 CVE-2020-23064 CVE-2019-11358.
Release Date: August 24th, 2023
SEPPmail version: 13.0.6
Author: Roman Stadlmair
Make sure to update to the newest Hypervisor drivers before updating to 13.0.6.
Detailed Description:
Bug fixed with release 13.0.6
Release Date: August 8th, 2023
SEPPmail version: 13.0.5
Author: Roman Stadlmair
Detailed Description:
Bug fixed with release 13.0.5
Detailed Description:
Typo fixed.
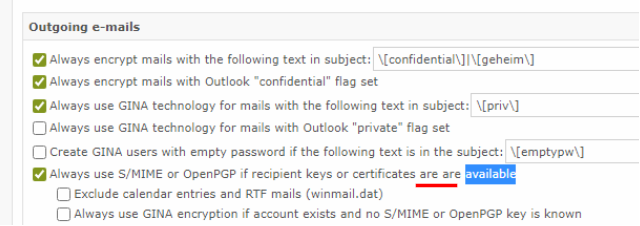
duplicate "are" removed
Detailed Description:
In rare cases, it was not possible to change backup passwords in customers settings.
Detailed Description:
With the change to a different format for the JobID, we had to adapt the script which reads current logfiles.
Detailed Description:
When you create a new managed domain in "Mail System" -> "Add managed domain" and do not change the TLS settings, the SEPPmail Gateway didn't use the setting "May" as default. This is fixed now (see screenshot).
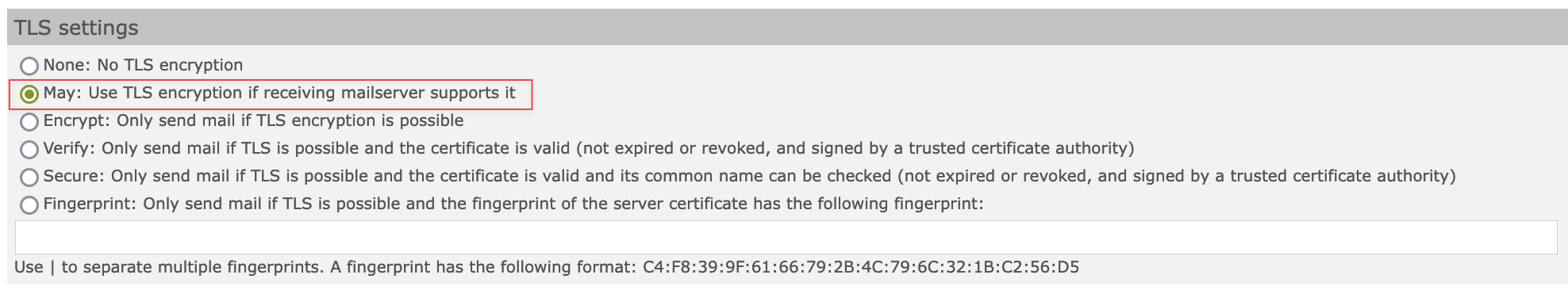
setting "May" is applied as default
Detailed Description:
Due to a bug in the config-server, some SEPPmail Gateways created thousands of certificates for a single managed domain. This was caused by a unclear response for certain domain names.
Detailed Description:
The error resulted in certain process IDs not being found and thus it was always assumed that the process being searched for was not running.
Detailed Description:
So far, only cluster members with a running LDAP (not frontends) had the ability to inject a mail on another cluster member (not frontend). This has been changed now. With the new setting "Cluster" > "Allow mail injection", you can allow this cluster member to inject mails on the selected cluster members (frontend or backend). This is mainly important for bypass LFT systems and for the "System" > "SMTP Loadbalancer". The synchronisation of stored LFT attachments will only be done to the selected members.
Detailed Description:
file.app had problems with several uploads finishing in parallel and thus lost a few. There was a problem with the way the DB environment of the session was handled.
Detailed Description:
LFM attachments and the GINA cache are now only synchronised to the "inject cluster members" configured under "Cluster". LFM only if LFM is licensed and activated for at least one GINA domain, and the cache only if at least one GINA domain has activated it.
Detailed Description:
With release 13 we changed the way to read credentials from the database, which caused SMTP-Authentication to fail.
Detailed Description:
With the broader acceptance of special characters in e-mail addresses, customers complained about bounced e-mails from the SEPPmail Gateway caused by missing UTF8 support. This fix adds UTF8 for postfix, which can be configured in "Extended MTA Settings".
enhanced UTF8 support
Detailed Description:
Sectigo changed its handling of GN, CN and SN for special characters, which required a change in our Sectigo MPKI interface.
Detailed Description:
On SEPPmail Gateways with a SCEP MKPI interface (i.e. for DTRUST), issuing a certificate failed after the upgrade to 13.x. The reason was a wrong key format for the LDAP import.
Detailed Description:
There was a small bug in the display of the SwissSign MPKI Settings page when no domain-specific data was previously saved. This is fixed now.
Detailed Description:
When importing customer/tenant data, it is now first analysed and then you can select which managed domains and GINA domains you want to import based on the analysis. However, this also means that only users belonging to one of the selected managed domains are imported. Also, only the GINA domains are imported which are assigned to one of the selected managed domains.

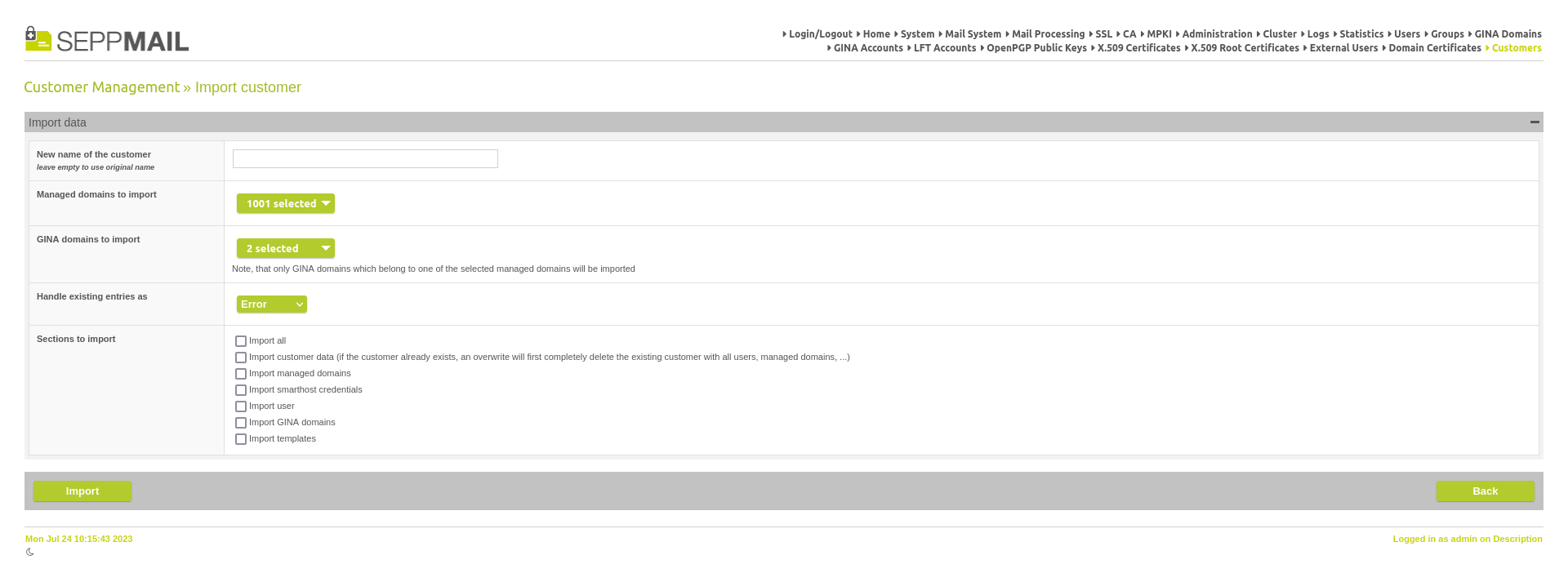
sections to import
Detailed Description:
Signing of PGP E-Mails failed due to a bug (typo) in 13.0.4. This is fixed with 13.0.5.
Detailed Description:
The update to release 13 caused an issue in sending SMS passwords to GINA users, due to a wrong search method for the users key, which was fixed with this release.
Detailed Description:
During a security audit we fixed a possible hole for LDAP injection. This injection would have only been possible from the internal network, still in larger environments it is a risk.
Release Date: June 19th, 2023
SEPPmail version: 13.0.4
Author: Roman Stadlmair
With the release of version 13.0.0, we introduced a change in e-mail routing behavior for internal mails, mainly due to requests from MSP partners (Managed Service Provider, customers consuming SEPPmail from a partner running SEPPmail for multiple tenants).
With the change in 13.0.0, e-mails between Exchange Online (ExO) connected Managed Domains have been delivered back to the configured forwarding server and no longer directly to the recipients MX domain, as it was up to 12.1.19.
This change caused some inconvenient e-mail routing behavior and unwanted effects for some other customers, mainly running their own appliance (not MSP). We found situations, that e-mails have been domain-encrypted and directly delivered and thus could not be read by the user.
This bugfix release 13.0.4 introduces a configuration option, which allows it to define this internal mail routing behavior according to customers needs.
By default, after update to 13.0.4, the formerly known routing behavior, up to version 12.1.19 is back in place. Internal mails will be routed directly to the recipients MX domain.
Performing the update to 13.0.4 directly from version 12.1.19, there is no impact or change on routing behavior. Updating from 13.0.0/1/2/3 will change the e-mail routing as described above.
MSP customers with ExO connected Managed Domains can enable the new routing globally or per managed domain. Read the documentation below for details.
The default value after update to 13.0.4 is „off for all domains“

Customers can change this according to the desired routing behavior.

For a specific Managed Domain you can change the setting, if the global setting from above is set to „Use domain setting“

Workarounds provided by SEPPmail support so far, using custom commands or introducing further IPs in allowed sending server setting, can be removed by then.
If you still have open questions and and you are unsure, please do not hesitate to contact support@seppmail.ch, mentioning „update 13.0.4 question“ as subject.
Detailed Description:
none
Detailed Description:
This is especially for Azure-VM´s. On system startup, SEPPmail Gateways now retreive a DHCP address and can be administered immediately.
Detailed Description:
Customers trying to backup a SEPPmail Gateway received the error: "Backup failed: Could not encrypt backup: Internal error: E05"
Detailed Description:
Customers reported that after the upgrade to 13.0.1, e-mail arrived encrypted at target mailboxes. This was due to an issue with changed routing mode in 13.0.x, see header-message of the 13.0.4 extended release notes.
Detailed Description:
Customers expected that a GINA user, which logs in with an external identity provider (Microsoft, Google, ...) needs no registration process and can directly access the e-mail
Detailed Description:
SEPPmail released a new APP for Apple iOS and iPadOS, the Viewer-APP. Any reference to the old "Reader" APP have been removed.
Release Date: June 1st, 2023
SEPPmail version: 13.0.3
Author: Roman Stadlmair
Detailed Description:
Disabling the "May not Sign" settings of users wasnt correctly shown in the users property, but was correct in the overview.
Detailed Description:
When changing DNS settings in the system configuration, an error occured in the UI.
Detailed Description:
Setting IP via console forces the user to enter DNS settings, but settings have not been saved correctly.
Detailed Description:
The error appeared if users from tenants in multi-customer-environments wanted to login.
Detailed Description:
The filter in the Admin-UI didnt work anymore.
Detailed Description:
When trying to edit the admin-user, saving changes failed.
Detailed Description:
ClamAV did not start in version 13.0.2. Error message in MaillLog was: WARNING: ClamAV is not enabled in Mail System, AV scan skipped
Detailed Description:
With upgrading to 13.0.0/1/2, the initial GINA-password-send didnt work anymore.
Detailed Description:
Additional to smtp and HTTPS unavailability, larger clusters showed instable behavior in syncing.
Detailed Description:
In version 13.0.2 - when creating a managed domain, 2 domain keys have been created wrongly by default. This fix changes the behaviour to one domain keys.
Detailed Description:
After upgrading from 12.1.x to 13.0.x SMTP authentication data was lost on some appliances
Detailed Description:
Gateway-admins with multi-tenancy enabled SEPPmail Gateway could create users manually. Those users have not been included in the license count limit of the tenant(customer).
Detailed Description:
Routing between Exo tenants did depend on the tenant-id before. This has been changed to use the X-Originator-Org from microsoft now, as this is a supported header.
Detailed Description:
There was an issue getting data from the Sectigo MPKI connector
Detailed Description:
After the update from 12.1.18 to 13.0.2, the Digicert MPKI connector could not get new certificates. Error message was MPKI: error issuing 'DigiCert' certificate for xxx.com': error while posting OrganizationID-JSON: Can't connect to www.digicert.com:443http://www.digicert.com:443 (certificate verify failed) (500)
Detailed Description:
Users could not reply to emails (neither to external recipients nor to themself)
Detailed Description:
Users could not search for public keys in the GINA interface
Release Date: May 12th, 2023
SEPPmail version: 13.0.2
Author: Roman Stadlmair
Detailed Description:
Customers requested that non-clustered appliances shall also show the cluster-information as single-node cluster.
Detailed Description:
When saving ruleset settings the settings for external keyservers have been removed.
Detailed Description:
Old text: "Always use S/MIME or OpenPGP if user keys are available" New text: "Always use S/MIME or OpenPGP if recipient keys or certificates are available"
Detailed Description:
A background job for cluster did not run with the new cluster-setup. It now runs also for single node-instances and Backend/FrontEnd Systems.
Detailed Description:
Due to the new cluster-config, a fix was required in certain for frontend/backend situations.
Detailed Description:
A cronjob was called in the wrong context and failed to refresh the maillog cache.
Detailed Description:
A backup, which was created and immediately reimported raised an error, but showed up as correctly restored.
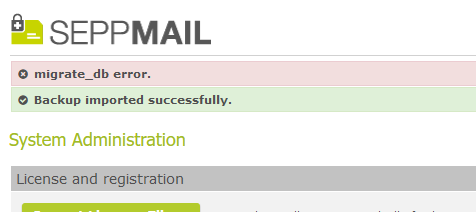
error message after restore
Detailed Description:
In some customer situations, the admin console on port 8443 was not available anymore, mailtraffic partly worked. This was caused by wrong parsing of the pid file.
Detailed Description:
PGP upload in the GINA web interface failed due to an error with the key information.
Release Date: May 9th, 2023
SEPPmail version: 13.0.1
Author: Roman Stadlmair
After upgrading from 12.x to 13.0 the SNMP daemon stopped working. This happened due to an update in the default configuration in the underlying OS.
A newline was missing at the end of the crontab file, which prevented the jobs from working.
Fix of the Microsoft module in the SEPPmail Gateway.
This feature-release contains updates around requirements from the market and from the SEPPmail.cloud.
!IMPORTANT: 13.0 works only with a new backend (MDB) for the LDAP database. The change improves opertions and backup performance, requires a reboot and a backup in advance. Consult your SEPPmail partner for help if you are unsure about the change.
Major changes are in networking, clustering, multitenancy with extended fields, GINA updates, and massive enhancements in the REST API to manage the appliance remotely. We furthermore allow now Microsoft (Personal and M365) and Google Accounts to authenticate in GINA without a user registration process.
This document is intended to support SEPPmail customers and partners to understand the new functionality quick, without reading the documentation in the first hand. For deeper understanding, please go to the documentation and read the details.
The ERN are separated into sections, (Admin, Backup, WebMail (GINA), ...) for categorizations. In the sections we sort the issues chronologically as they appeared inside SEPPmail the first time.
Each issue has an internal reference which points to our internal ticket number, an issue type, and some issues also have a more detailed description, if the issue header does not provide sufficient information.
The issue types are:
This document is written in markdown, so formattig is not perfect but markdown is cool ;-)
The "Admin" section contains everything which belongs to system administration, key and certificate management.
Detailed Description:
When revoking a X509 Root certificates, the revokation was applied to all certificates of the same name downwards (e.g. a demo and a production certificate). The revocation now also checks the fingerprint.
Detailed Description:
The option "Server requires authentication" could not be deactivated as long as the option "Use the following SMTP server" was set. This is now fixed.
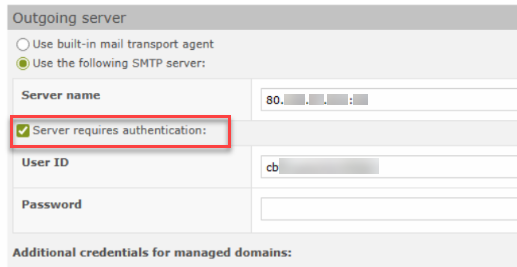
"Server requires authentication" option in settings
Detailed Description:
The size of the network adapter (maximum transmission unit (MTU), see also https://en.wikipedia.org/wiki/Maximum_transmission_unit) can now be defined under "Systems" > "Advanced view" > "IP Addresses".
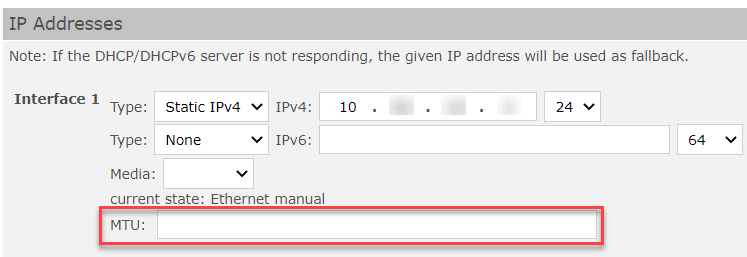
MTU setting
Detailed Description:
It is now possible to specify a default gateway outside the own networks under "Systems" > "Advanced view" > "Routing".
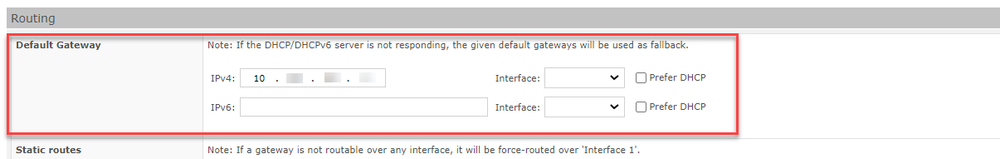
Default gateway outside the own networks
Detailed Description:
It is now possible to specify active routes networks under "Systems" > "Advanced view" > "Routing". This is e.g. necessary for special network environments like Hetzner and others.
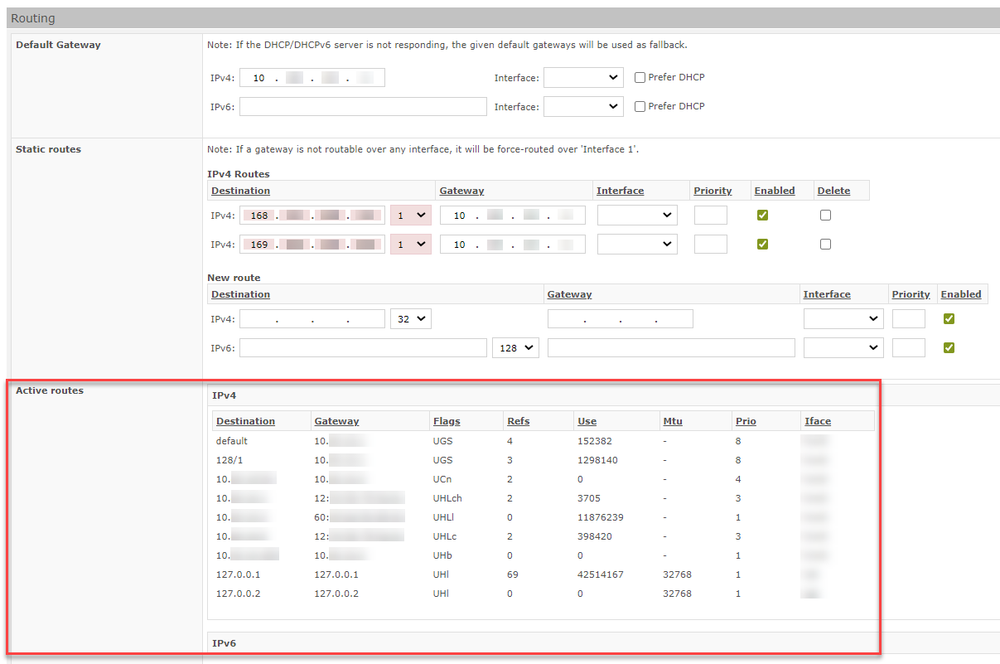
Active routes
Detailed Description:
Under "System" > "Advanced view" > "Virtualization Tools", the existing environment is now auto-detected and the corresponding options are set.
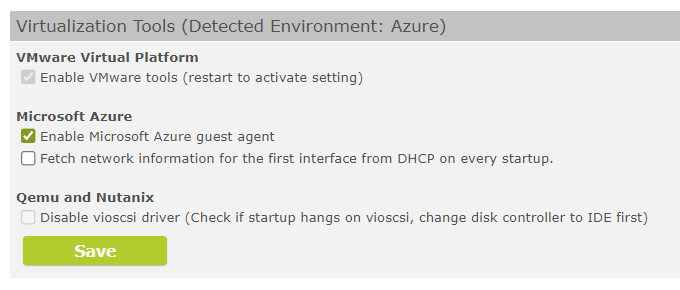
Virtualization Tools with detected environment
Detailed Description:
Under "Mail System" > "Dovecot Settings", it is now possible to configure the allowed ciphers, out of a list of currently 30 available ones.
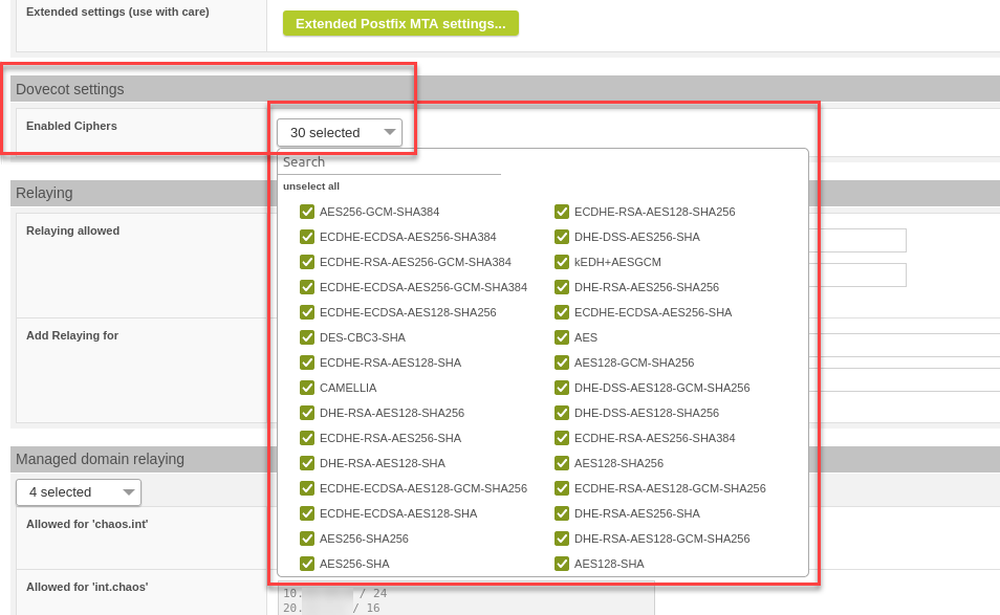
Dovecot ciphers configuration
Detailed Description:
In the past, only PEM format was supported. Now, PKCS#12 keys are expected.
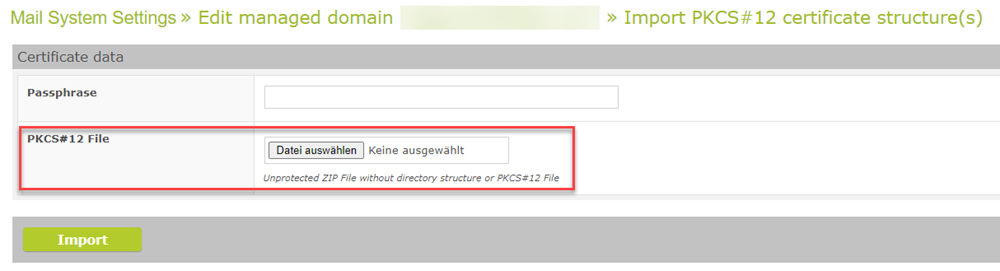
Import keys in PKCS#12 format
Detailed Description:
A backup is usually the only way key material can leave the SEPPmail Gateway. Therefore the backup password now has to meet certain password criteria (16 characters, lowercase, uppercase, number, specials).
Detailed Description:
If administrators make changes to a managed domain, these must be activated with "applyMailconfig=True". In the past, this happened synchronously, which could lead to waiting times in the user interface. Now, the REST API gives a return value (if possible) and then executes the restarts of services asynchronously in the background.
Detailed Description:
A bug was fixed that could lead to Postfix processing mails based on the wrong main.cf file.
Detailed Description:
Instead of the formerly used Device ID which was based on hardware information and could e.g. result in duplicate MAC addresses in virtualised environments, a Device UUID is created upon a first image start or the update of a device after an update to 13.x from 12.x. The Device UUID is currently only visible in the cluster configuration under "Cluster" as it is for now only used for cluster functionality. (Clustering, cloning and licensing processes do not create a UUID.)
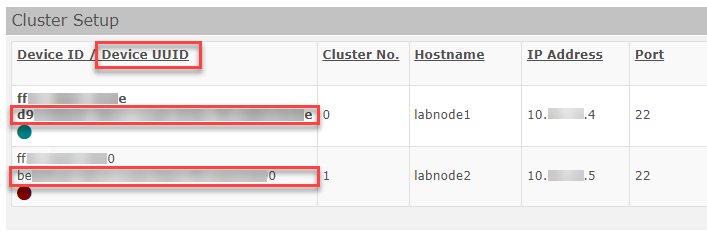
Display of Device UUID
Detailed Description:
By design, a cluster identifier can be used to access any cluster member from any system with network access to one cluster member. To mitigate this security risk, the cluster identifier(s) to be protected can be entered manually under "Cluster" > "Protect cluster identifier".
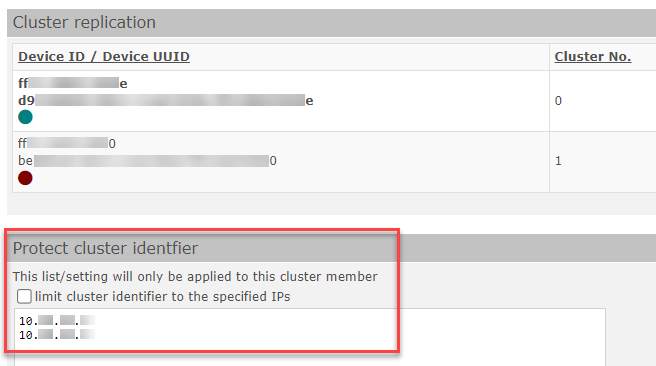
Protect cluster identifier
Detailed Description:
The database backend changed from BDB to MDB, which improves the performance of many processes. MDB is mandatory for the upgrade to 13.x. You will get prompted to create a backup before the change to MDB !
Detailed Description:
LFM attachments are now symmetrically encrypted with aes-256-cbc with SHA512.
Detailed Description:
The PID of the SMTPd.pl is now logged in the mail log, written in brackets.
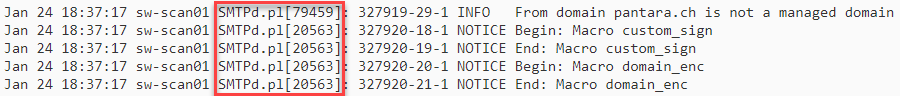
Mail log excerpt with SMTPd.pl[PID]
Detailed Description:
The Postfix configuration file "mynetworks" now uses the CIDR map as input for the relaying IPs.
Detailed Description:
It is now possible to have a user-defined DKIM key pair per managed domain. The standard name (selector) is "default".
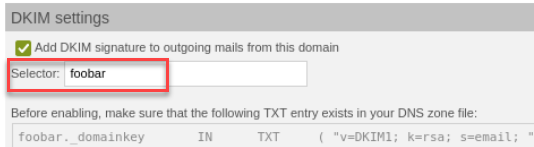
User-defined DKIM selector
Detailed Description:
Misconfigured M365 customers may overload the rule engine and cause large numbers of "too many hops" rejects (mail loop). To prevent this, the maximum number of hops is limited to 50. Higher numbers are reduced in /etc/postfix/master.cf before the mail is passed to the rule engine.
Detailed Description:
With the new option "Mail System" > "Managed domain relaying", it is now possible to activate all IPs of a managed domain (as given under "Allowed sending servers for this domain") as relaying IPs. This saves having to enter the IPs twice. Also, when a managed domain is deleted, the relaying is now automatically removed.
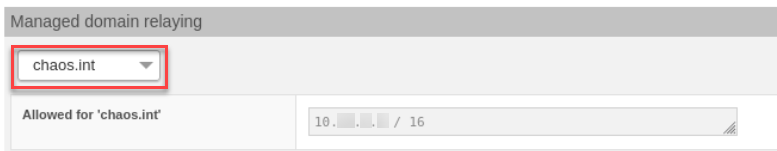
Globally activate all IPs of a managed domain as relaying IPs
Detailed Description:
In the past, tenants (customers) were identified by name. This could lead to conflicts, as typos may happen. Now, every tenant receives a Tenant UUID which is visible in the "Customer Management". The Tenant UUID can also be adressed via the REST API.
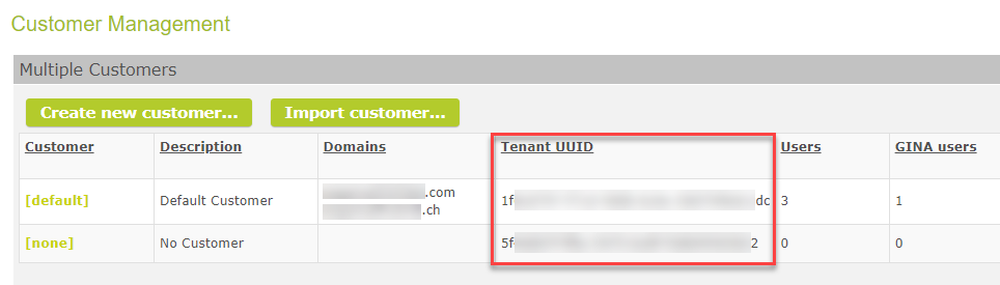
Tenant UUID in the list of customers
Detailed Description:
The "Extended fields" can be used to easily configure tenant, managed domain or user-specific settings by means of custom commands, especially in client-separated systems. They can be defined under "Mail Processing" > "Edit extended fields". Extended fields add a powerful tool for complex customer environments and MSPs that have to deal with different mail-routing requirements on different hierarchy levels.
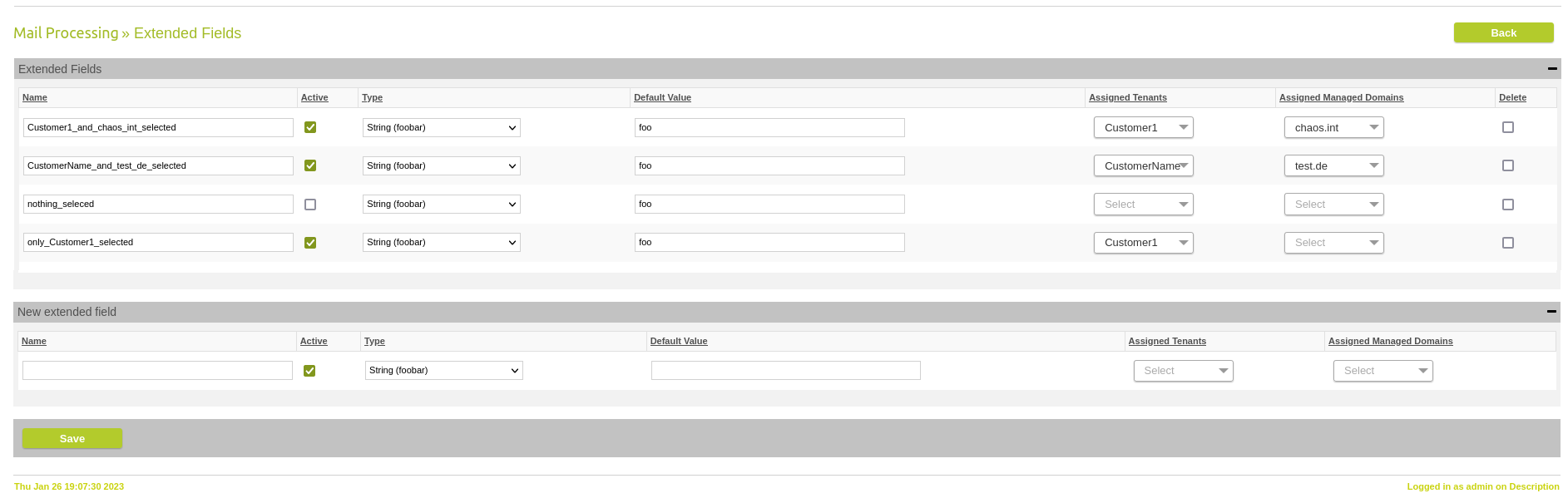
Extended fields for more granular mail processing
Detailed Description:
For the REST API tokens you can now not only specify for which module the access is allowed but also which operation is allowed: GET, ADD, MODIFY, DELETE.
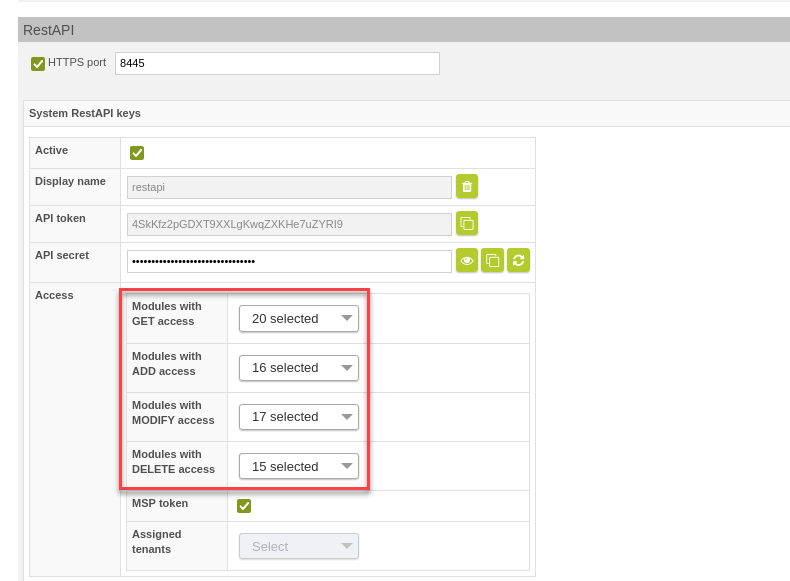
Granular allowed operations per module
Detailed Description:
The TLS domains under "Mail System" can now be displayed, added, edited and deleted via the REST API.
Detailed Description:
Certificate information can now be retrieved via REST API.
Detailed Description:
The MPKI can now be managed via REST API. This corresponds to the manual settings under "MPKI".
Detailed Description:
The general settings under "Gina Domains" can now be set via REST API.
Detailed Description:
The Mail system settings can now be managed via REST API. This corresponds to the manual settings under "Mail System".
Detailed Description:
If domain settings were changed via endpoint /mailsystem/manageddomain, it was possible to enter invalid CIDR range definitions, e.g. "195.48.84.97/27" (which has host bits set instead of specifying the network address). This is now fixed.
Detailed Description:
The cleanup of token information now takes place before dispatch (not after).
Detailed Description:
In the past, the REST API occasionally did not start directly after a logrotate but ten minutes later. To improve this, the kill_timeout signal has been changed from 1 second to a 10 seconds delay between re-starts.
Detailed Description:
The managed domain groups, called mailprocessing groups in the GUI, are a new feature. Their (currently only) purpose is to hold extended fields for a group of users. Only users which belong to the managed domain can be members of such a group. The feature can be accessed via "Mail System" > "Edit managed domain" > "Edit mailprocessing groups".
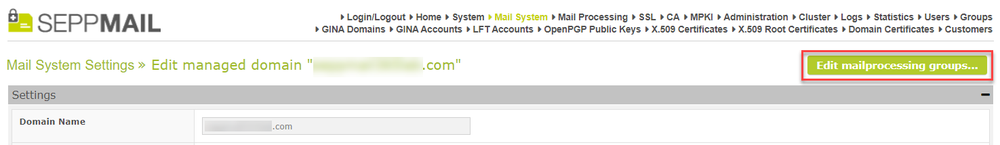
New button "Edit mailprocessing groups"
Detailed Description:
Firmware updates are signed with a code-signing certificate. The public key must be available on the SEPPmail Gateway.
Detailed Description:
Recipients of GINA mails sent to mailboxes linked to a publicly accessible Identity Provider / IDPs are able to authenticate themselves to GINA using this IDP. Currently available IDPs are "Google", "Facebook", "LinkedIn", "Microsoft" and "Fideas IAM". The allowed IPD must be defined per GINA domain under "GINA Domain" > "IDP settings".
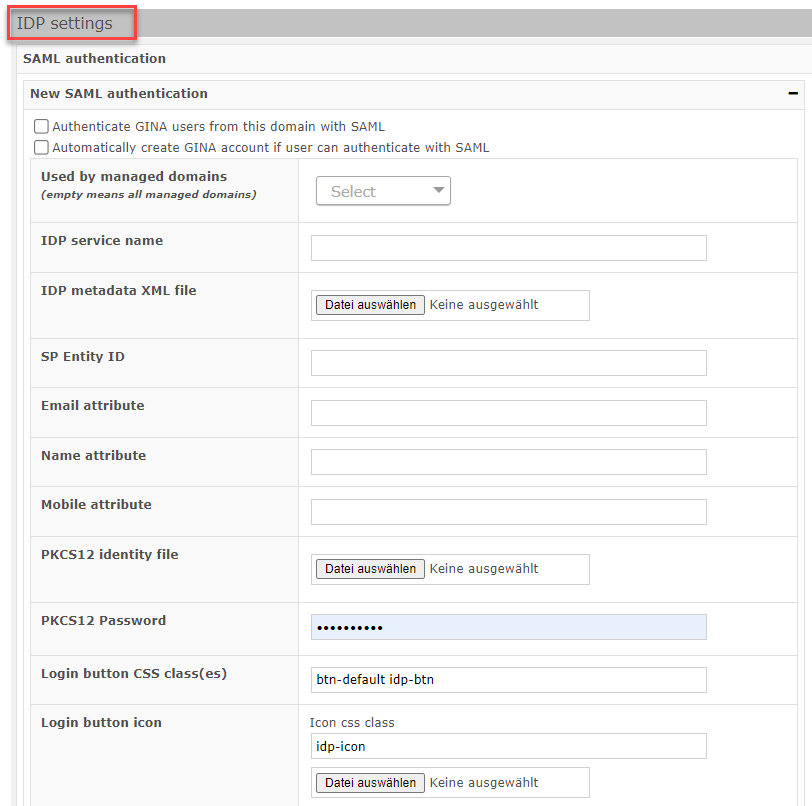
IDP settings
Detailed Description:
The new GINA cache mode allows for caching the encrypted secure attachment "secure-email.html" on the server. (It is still always attached to the GINA email.) The feature is configured under "Gina Domain" > "Change GINA settings for [domain] > "Server side caching". It is only available if an LFT device exists.
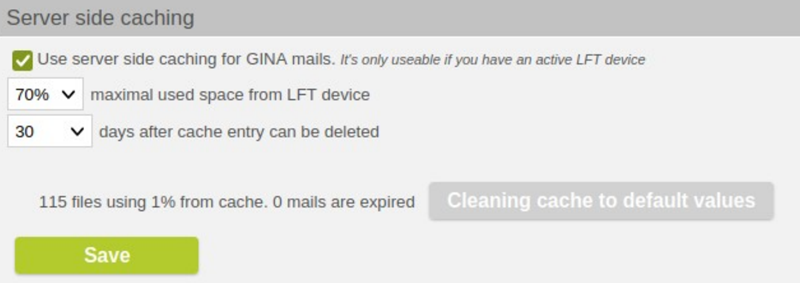
Server side caching for GINA
Detailed Description:
The Password settings are now embedded in the web-code to be read by HTML browsers or apps.
Detailed Description:
Internal GINA users, that is GINA users that are authenticated via LDAP/SAML/oAuth, no longer have to register themselves upon first login / start email.
Detailed Description:
In the past, only gif images were possible as logos. This list has been vastly extended. It is now possible to upload GIF, PNG, JPG, SVG images, and for the favicon also ICO.
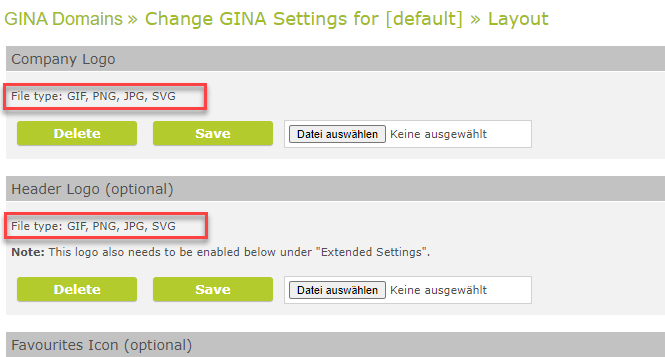
Available image types for upload in the Layout
Detailed Description:
So far, a GINA sender could provide their key to a recipient in the GINA portal only via search. Now, a direct download button for keys is available.
Detailed Description:
The maximum GINA password length is set to 2048.
Detailed Description:
A password is only on the level of "excellent security" if all set password requirements are met.
Detailed Description:
Syntax errors in the custom CSS file under "GINA Domains" > [GINA domain] > "Edit GINA Layout" > "GINA CSS" could cause errors when sending the GINA carrier mail. Now the internal check "CSS::Minifier::minify" is run before the CSS is saved.
Detailed Description:
The error message is now "420 An encryption key for your account '$senderemail' will be available shortly".
--- end of document ---