Tip: All changes are tracked in the Gateway documentation, see the information in the last row of the documentation agreement.
For the new 14.1 release, see https://downloads.seppmail.com/extrelnotes/141/ERN14.1.html
For the latest 13.1 releases, see https://downloads.seppmail.com/extrelnotes/131/ERN13.1.html
IMPORTANT - With version 14, the memory requirement has increased. This depends, among other things, on the additional features that are active, in particular the Protection Pack.
The minimum requirement from the sizing table therefore may not be sufficient for additional features (see also footnote 3). If the system resources are too low, machines may crash, but more unspecific, sporadic or permanent errors may also occur.
IMPORTANT - Since version 14 we highly recommend to add an LFT disk to ensure that a database snapshot is done every day (see also new feature "database backup").
This is the last release in the 14.0 branch and enables the update to version 14.1.
Release Date: May 27th, 2025
SEPPmail version: 14.0.7
Author: Birgit Grossmann
An error in the code meant that the password policy was not saved in the Admin GUI. This has been fixed.
(Note: this issue was formerly published as having been fixed with 14.0.6.)
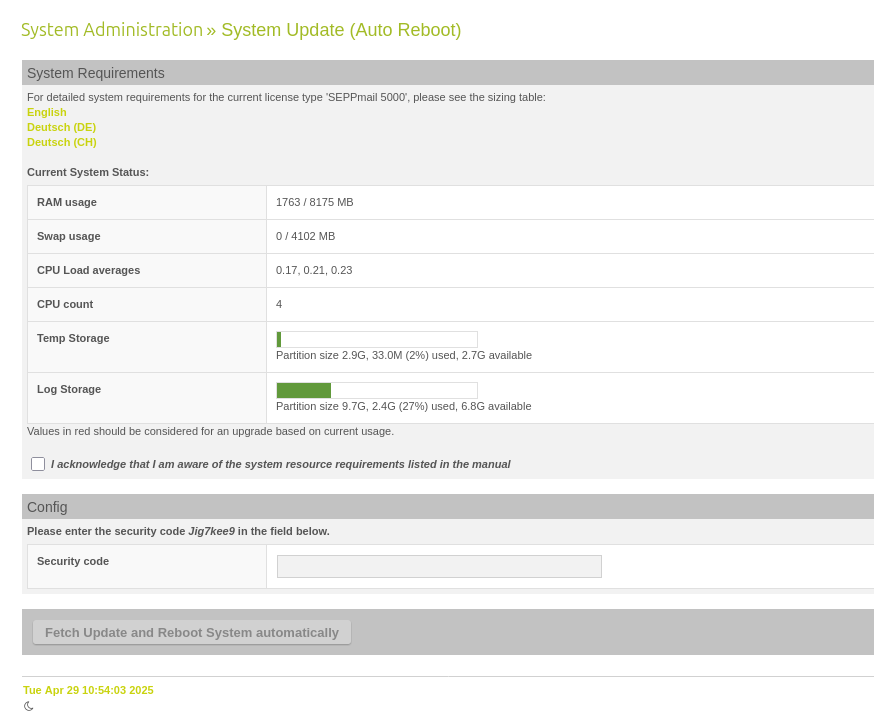
With version 14.0.7, some additional information about the resource consumption of the SEPPmail Gateway is displayed in the update page of the Gateway and a note was added referring to the minimum resource requirements in the manual so that an update does not overload the Gateway. Furthermore, if possible, the /tmp partition is automatically transferred from a RAM disk to a real hard disk partition.

Current system status / resources check
In version 14.0.6 we had implemented a mechanism that did not generate the GINA relevant directories and files if GINA was not activated for the system under System. Unfortunately, this led to problems with the generation of GINA mails, as it accesses some of these files. If these files are not created, the RuleEngine cannot read them either. We have therefore reversed the behavior introduced in 14.0.6 until we have a better plan and can separate the data cleanly.
The problem was that the generation of the “To” addresses for the daily digest did not check whether one of the addresses in the generated list was empty. Such an empty address then led to an invalid format of the To header of the mail and thus the mail was rejected and not sent. This has been fixed.
When using DSN (Delivery Status Notification), "Notify=..." is used in the SMTP protocol after the address of a recipient to specify the mail status about which the sender should be informed. However, we had a long-dormant error in the code that prevented the correct parsing of this "Notify=..." information correctly. This has been fixed and therefore, if the customer configures SEPPmail correctly, DSN should now work correctly.
There was a bug that prevented the file.app required for the bypass upload from being accessible via the web server. The background was that the corresponding function accessed the outdated LDAP attribute and not the currently used one. As a result, there was no data and it was always assumed that LFT was not being used, which deactivated the file.app. This has been fixed.
Release Date: April 30th, 2025
SEPPmail version: 14.0.6
Author: Birgit Grossmann
A typo in the CfgServer prevented a cluster-wide application of the mail templates. This has now been fixed.
There was a problem in the REST endpoint "/webmail/domain" which prevented the password reset recipient from being saved to "last sender". This has now been fixed.
In the customer overview, different values were displayed than were retrieved via the REST endpoint "/statistics/license". This has now been fixed.
Internally, SEPPmail allows the use of expired key material for domain encryption. However, the RestAPI ignored these certificates in "/info/encryption", which led to confusion for one customer as they thought that encryption was not possible after a Rest query.
The RestAPI now delivers the results as the RuleEngine would behave, namely that expired key material is okay for domain encryption.
With this solved issue, the RestAPI should have a lower memory consumption, as the work processes are regularly restarted and thus the occupied memory is released again.
Previously, the ARC seal was only validated if the DKIM signature was invalid. Due to this, cv=none (chain validation = none) was set as ARC seal setting when sending. However, as the affected mails had an ARC seal chain, this led to problems. Now we always validate and set the correct "cv=..." value accordingly.
With this issue a pentest finding was fixed. There was a possibility to execute specially named attachment code on the SEPPmail Gateway via the "Download as PDF" function in the GINA GUI.
With this issue an error was fixed that occurred when using UEP (unique email password) and an initial password length of 0. This forced the user to register without this being necessary or desired.
Release Date: April 1st, 2025
SEPPmail version: 14.0.5
Author: Birgit Grossmann
Under "Mail Processing" in the Miscellaneous section there is the item “Enable LDAP server on port 388, 387 and 635 to distribute collected S/MIME certificates to internal users”.
This so-called ldapproxy had an internal problem when processing the transferred filter string, especially when mail clients such as Thunderbird query it and send an LDAP request with every keystroke. Fixes were already applied in versions 14.0.3 and 14.0.4 but there still were problems. They are hopefully fixed now.
The columns for GINA user and Valid S/MIME certificates were not filled with the correct data in the customer overview page. This has now been fixed.
There was an error when filtering the displayed mails in the log if DB-based logging was used and a customer admin wanted to display the logs. The error resulted in the customer admin seeing no entries at all. This has now been fixed.
Previously, only the systems in a cluster with a database (normal cluster members or backend systems) could transfer CA and SSL certificates to the other cluster members. Now the frontends can also do this.
We have recently added tests to determine whether the local database is defective. However, there were situations in which the test never ended (which is also a sign of a defective database). Now we have added a timeout for the test. If the test runs into this timeout, then the database is also defective and is reported accordingly.
The file.app, with which the bypass LFT attachments are uploaded, completely loaded the attachments into memory for further processing. With large attachments, which is what LFT is intended for, the memory requirement eventually became so large that the file.app crashed. Now we stream the data directly to the hard drive without loading the data in memory.
Until now, the file.app, which is used to upload the bypass LFT attachments, was used as a CGI script. This meant that the script was reloaded each time it was called, which took a relatively long time. Now the file.app runs as a backend and is therefore more responsive.
SEPPmail is logging errors that occurred when generating certificates via the MPKI connector. This log file was not rotated correctly. This should be fixed now.
In the RestAPI there was a logic error in the function to determine the encryption methods for certain recipients, which resulted in HIN encryption no longer being checked. This has been fixed now.
In addition to the webmail fix below, we also added the option to specify the GINA domain in "webmail_keys_gen()" and "webmail_keys_avail()".
Previously, we opened the preview for an attachment in the GINA GUI via a link that contained the session ID. As some see this as a security risk, we now switched from a link with a GET request to a form POST request.
Furthermore, the alignment of the labels for the input fields in the GINA GUI has been improved.
When using Encryption Policies in conjunction with GINA encryption, there was the problem that although it was possible to specify which GINA domain was to be used for encryption, this GINA domain was not used to create the GINA users. This meant that different settings were used to create the users than the Encryption Policies should have used with their configured GINA domain.
Now the configured GINA domain is also used to create the users.
With this issue, a password reset error in the GINA GUI has been fixed.
When displaying the GINA GUI, there was a display error in the footer. Only half of it was displayed, so that you had to scroll even if this was not necessary for the window content. This is now adjusted dynamically.
If someone set ‘never’ as the expiry time for the cache mode in the GINA domain, the LFM partition was running full and no old messages were deleted when a new one was to be sent. With this correction, as many as necessary of the oldest cached mails are deleted until the new mails can be cached.
Previously, when downloading all attachments of a GINA message as a ZIP, all files were first packed and then the download was started as a ZIP file.
However, if there were a great number or large attachments, the creation of the ZIP sometimes took so long that the client timed out and was unable to download the ZIP.
Now the download is streamed directly as ZIP, so there is no longer any delay. The only disadvantage is that the size of the generated ZIP is not known in advance, which means that the end of the download process cannot be predicted.
Release Date: February 25th, 2025
SEPPmail version: 14.0.4
Author: Birgit Grossmann
Under "Mail Processing" in the Miscellaneous section there is the item “Enable LDAP server on port 388, 387 and 635 to distribute collected S/MIME certificates to internal users”.
This so-called ldapproxy had an internal problem when processing the transferred filter string, especially when mail clients such as Thunderbird query it and send an LDAP request with every keystroke. A first fix was already applied in version 14.0.3 but still had problems. This is finally fixed now.
Previously, when a possible update was displayed in the administration GUI, one could only see the new updates within an update channel, and with the last version of a channel one could then see the latest version of the next update channel. This way, if a customer was on e.g. version 14.0.2 for a long time, they would never be informed that a version 15 had been released.
From now on, the latest version in general is also displayed. The customer will therefore see both the latest update for their version, e.g. 14.0.x, and the generally latest update (e.g. 15.0.x).
When an appliance was removed from the cluster, the LDAP configuration was not regenerated on the remaining cluster members and so they still tried to sync with the removed member. Now the LDAP config is regenerated.
With the new DB-based log archive there was a problem that not all icons for all cryptographic actions that were applied to the mail were displayed in the log view. This is now fixed.
However, the user must first delete the archive cache and have it recreated.
With this issue, unnecessary log entries in the syslog about missing LFT functionality are prevented if no LFT is licensed at all.
Up to now PGP/MIME has never been detected directly, but always indirectly via the content of the individual MIME parts of the mail. Now the detection of PGP/MIME is carried out specifically.
Previously, the secrets for the RestAPI tokens were saved directly. From now on, they will be saved as SSH512. A direct consequence of this is that the secret can only be seen when it is generated, so it has to be memorized or copied securely at that point. The Admin GUI shows a corresponding warning.

Warning that the API secret is only visible before saving
In this issue, an exception in the RuleEngine is fixed that occurred when generating GINA mails with certain password settings.
The problem that was solved with the issue is that GPG does not always have the same output in its status outputs. This can even change from version to version. In this particular case, GPG outputs the status output in different sequences, depending on whether the mail part to be processed consists of binary data or text. SEPPmail previously assumed a fixed sequence. This is corrected now and any sequence will be processed.
There is now the additional option of specifying a URL (instead of a file) for the metadata XML in the SAML IDPs of the GINA domains. This has been included because the imported XML for one customer was no longer up-to-date at some point, but they were not informed by Microsoft that it had been updated.
If an URL is entered, the XML is pulled and validated in the background. If everything is correct, it is imported. A cron job is then run once a day to update the XML.
In the file field, a note is displayed that a metadata XML URL exists.
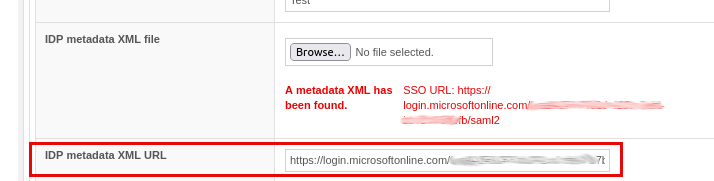
New field "IDP metadata XML URL"
With this issue, improvements for the beta version of GINAv2 were implemented.
The problem here was that if the cache mode in GINA was activated, it was no longer possible to change the text for plain LFT because it was no longer saved. This is fixed now.
This is an additional fix to a bugfix in version 14.0.3. With it, the checks regarding the existence of GINA accounts should now run without error.
With this issue, two non-critical pentest findings were fixed.
Release Date: January 28th, 2025
SEPPmail version: 14.0.3
Author: Birgit Grossmann
Under "Mail Processing" in the Miscellaneous section there is the item “Enable LDAP server on port 388, 387 and 635 to distribute collected S/MIME certificates to internal users”.
This so-called ldapproxy had an internal problem when processing the transferred filter string, especially when mail clients such as Thunderbird query it and send an LDAP request with every keystroke. This is fixed now.
Since version 14, OpenBSD no longer allows to change the domain name under "System" if the system is already running and a domain name is already set in the system. The system has to be rebooted. Appropriate notes have been added in the Admin GUI.
When creating a new managed domain, an error occurred that certain system extended fields could not be found because no domain was specified. In principle that was as intended, but customers were irritated by the error messages. This no longer happens.
When generating the daily digest mail, there was a problem in connection with the statistics graphics. If at least one of these could not be generated, the code used /dev/null as the source for the image attachment and - when cleaning up the mail at the end - /dev/null was then consistently deleted. Since we send output to /dev/null in many places and /dev/null was thus recreated with restricted rights, some processes could no longer write to /dev/null and terminated with errors. Now /dev/null is no longer deleted and there are no more problems in this regard.
Recently, the number of defective databases has increased. For this reason, we have implemented checks to detect defective databases. This is communicated to the admin via a watchdog message. We also prevent the creation of backups and daily snapshots so that the last valid backup remains on the system and gives the support team the opportunity to restore it.
When generating the user statistics for the daily digest, there was a problem that the emails were not “escaped” for the search filter, which caused the creation of the daily digest to stop completely and no daily digest was sent. Now we escape the mail addresses and the filter strings are fixed.
A bug in the code of the CertCentral MPKI Connector Settings prevented the deletion of domain-specific settings. This has now been fixed.
In two places, the wrong temporary directory was used to store data temporarily. This could result in the data not being removed later, as the system did not search for data to be removed at these locations. This is fixed now.
There was a problem in the code that the last mail header was not processed correctly when the mail was initially parsed, and therefore could not be evaluated later. All headers are captured now again.
Under "Mailsystem" there is the setting option “Exchange Online Relaying”. There was a bug whereby mails from any domain coming from ExO were allowed through if both the sender and recipient domains were not managed. This has now been fixed. Mails from ExO that are recognized as external are no longer relayed.
There were problems with the decryption of PGP mails. These were caused by the switch to the latest GPG. This sends more information via the status socket than the old version and so SEPPmail received commands that it didn't know (yet) and that do not always arrive. We have corrected this for the time being for the CS03 error case.
In the code for generating the GINA mails, the Rule Engine checks whether the initial password mail has already been sent and the code uses this information to decide whether a valid GINA account exists or not. The case that the default password length is 0, that means no password is required for the login and therefore no initial password mail is sent, was not taken into account. From now this will be taken into account.
The web.app (the old GINA) logs to its log file with the help of syslog. Previously, when this file was full and rotated, the web.app was restarted and this led to the problem with customers as a very large LFT upload in the GINA GUI might abort. Since the web.app uses syslog, it is no longer necessary to restart the web.app.
Previously, if you were in the GINA GUI and wanted to download the attachments of a mail summarized in a ZIP file, the attachments were downloaded one after the other from the S3 storage (if this was used). This leads to possible timeout problems if a large number of attachments are attached to the mail. The download now takes place in parallel and is therefore much faster.
Previously, when replying using the reply-all function in the GINA GUI, either a GINA account had to exist for each recipient or the recipient had to have an S/MIME certificate or a PGP key so that the reply to these recipients would be encrypted. Previously, it was not taken into account that domain encryption (S/MIME or PGP) was also possible or that a TLS domain was configured. This is now taken into account and the reply-all also works for recipients who only use domain encryption or are reached via a TLS domain setting.
Release Date: December 7th, 2024
SEPPmail version: 14.0.2.2
Author: Birgit Grossmann
With the primary use of OpenSSL in the code we have also run into a few issues. Primarily, the creation of CSRs in the MPKI connectors was no longer possible, nor was the import of p7b formatted certificates. This has been fixed now.
With 14.0.2.1, we have made a correction to ensure that only certificates that can also be used for encryption can be downloaded from the GINA portal. An error crept in here, which then completely prevented the download of the certificate found. This has been fixed now.
Release Date: November 29th, 2024
SEPPmail version: 14.0.2.1
Author: Birgit Grossmann
So far the SEPPmail Gateway has been using a fixed number of threads for the LDAP. According to the documentation, their number should be 4 or 8 times the number of CPU cores, which ensures maximum read performance. A higher value could slow down the LDAP and a lower value might not reach its full potential. We now use 4*CPUs, as there are other services running on the system that require resources.
(The effects of this bug were only relevant in the SEPPmail cloud.) When using an S3 storage for the LFT attachments, there was an error when determining the size of the attachments that we stored on the S3. As a result, we were unable to write certain data to the LDAP, which was later used both for the quota and for calculating the storage space used per user. This has now been fixed.
Since the Gateway version 14, SEPPmail is using OpenBSD 7.5. Since this version the list of MIB files has changed, which we did not take into account and therefore not all files were copied into the Gateway image. The list is now complete again and snmp should work as before.
Apparently LibreSSL has had a problem processing some X.509 certificates since Gateway version 14.0.Specifically, the error seems to be that LibreSSL cannot (or does not want to) parse the date format of the validity periods. For this reason, we have now switched to favouring OpenSSL, which hopefully does not have this problem.
In the last release, we overlooked a code point that needed to be adjusted. This resulted in GINA domains that do not use virtual hosting and are therefore accessed via a corresponding path of the default GINA domain always referring to the new GINAV2 in the Apache configuration. As this is not usually configured there, an error occured and users could no longer access the GINA interface. This is fixed now.
Release Date: November 26th, 2024
SEPPmail version: 14.0.2
Author: Birgit Grossmann
Due to an internal error, under certain circumstances it was not possible to create additional extended fields . The error has been fixed.
The keyserver that makes the public certificates of the local users publicly accessible was somewhat fuzzy in the way the filter string for the LDAP request was processed. This has now been improved and a usable mail address is searched for.
Due to an incorrect script, a customer_backup was created every 15 minutes. As the SendBackup script sent all customer backups to be found, some customers received up to 4*24 customer backups per day. The correct script is now called at the appropriate point, and this also prevents the excessive sending of customer backups.
When importing a backup, there is the option "Keep current system setting instead of restoring them from the backup". This should actually prevent system settings from being adopted from the backup, but it only does so to a limited extent. If nothing was configured for a setting in the current system setting, then the value from the backup was adopted.
Two things have now changed. Firstly, the option is now called "Keep current network related system setting instead of restoring them from the backup" and includes the system settings Comment, IP Addresses, IP ALIAS Addresses, Name, Routing, DNS, SNMP Daemon, NRPE Daemon, Zabbix Agent, SMTP Loadbalancer. On the other hand, empty values are no longer overwritten.
A customer had several certificates in their CA list whose ASN.1 structure was not correct and LibreSSL therefore had problems using them. When SEPPmail creates the internal CA files, we now prevent non-parseable certificates from ending up in the files.
There was an error in the script that establishes and monitors the connection between cluster members, which caused it to re-establish the connections over and over again.
This has been fixed so that connections are not repeatedly terminated and reestablished. Also, the error code for a faulty bypass LFT message is now 555 (instead of 431).
Attachments with special characters, in the specific case with French special characters, caused an error when decoding the charset in UTF8. This has been fixed now.
api.app, the backend for the new GINA, is now only started if one of the GINA domains is actually using it. Otherwise, the api.app backend will not be started.
Some security experts are of the opinion that it should not be visible which software is used as an HTTP server in the GINA backend. As the server header is always sent and we cannot remove it completely without customising our own software, we now set the value to a 16-character random string for each call.
Users who were created in the GINA GUI using the "self-registration" function did not have a registrationDate set and were therefore listed as "unregistered" in the Admin GUI. This has been fixed.
In the GINA GUI it was no longer possible to change the language via the language dropdown. This has been fixed.
Due to an error, the mobile number had been made a mandatory field, although the user had not configured this. This has been corrected and now works again as configured in the Admin GUI.
In the SEPPmail Gateway, you can set whether the user certificates can be used for decrypting incoming emails or for signing.
In the GINA interface, you can search for user certificates that are intended for encryption. Consequently, only certificates that can later be used for decryption in the SEPPmail Gateway should be displayed in the search. Previously, this was not taken into account. Now it is.
Changes in 14.0.1 caused the entry of the security question and answer to always be mandatory, even if they were not required and no input fields were displayed for them. These errors from 14.0.1 have been fixed.
Webmail (GINA) has the option to send the reset password to the last sender who sent a GINA Mail to a GINA user. The determination of the last sender was incorrect and therefore it was possible that another person received the password reset mail.
Release Date: October 29th, 2024
SEPPmail version: 14.0.1
Author: Birgit Grossmann
The new DB-based logging had a bug, so that that it was no longer possible to view the log details of individual mails. This has been fixed and works now.
With 14.0.0.1, SEPPmail had a hotfix release for the first time. As the code at the point that calls the DB migration and therefore makes the DB changes for the new version was not familiar with the Hotfix number, the system did not migrate the DB in cluster environments and therefore the necessary changes were not made. This later led to problems in various places where these changes were required. We now handle the hotfix number correctly, and with the update to 14.0.1 a migrate_db will be executed again anyway.
As part of the certification process, SEPPmail had to restrict the access rights for the mailgraph.app. This generates the statistics graphics for both the Admin GUI and the daily digest. This restriction meant that statistics graphics were not displayed. This has been corrected and the graphics are now available again.
Fixed with #43906 "Fix privileges for /tmp/mailgraph so conf.app is allowed to write images" above.
The automatic dispatch of the customer backup did not work. The error has been corrected and now it works again.
The problem with the authorisations in the mailgraph.app also affected the automatic sending of the daily digest via cron job. Fixed with #43906 "Fix privileges for /tmp/mailgraph so conf.app is allowed to write images" above.
Until now, SEPPmail forgot to correctly include uploaded LFT attachments when calculating the LFT quota via bypass upload. This is done now.
In satellite operation, the backend system had problems transferring the mails fetched from the satellite system via fetchmail to the local Postfix, which rejected these mails. The Postfix configuration has now been adjusted so that fetchmail can deliver the mails again.
In the daily digest you now receive a summary of the failed attempts to obtain certificates using the configured MPKI Connector (with an error message about what went wrong).
In Mail Processing > Keyserver, a new checkbox "Verify CA is trusted" has been added.
When this is checked, then any S/MIME certificate that is downloaded from the keyserver will be checked against the root CAs, to see if the root is complete, trusted and present.
The option is disabled for PGP certificates.
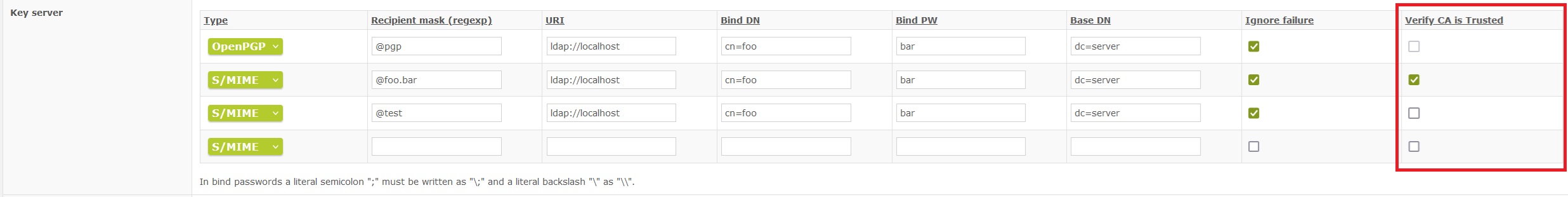
New checkbox "Verify CA is trusted"
Due to two different timestamp formats, there was a problem processing the login history and therefore the GINA Accounts menu did not load. This has been fixed.
Due to a bug the download of the public domain certificates was not possible. This has been fixed now.
A bug prevented the download of public user keys in the GINA GUI. This has been fixed now.
When self-registering in the GINA portal, it was previously possible to leave the email field blank. This meant that you simply returned to the login screen and the previous entries were discarded. Now the necessary input fields are marked as required and therefore the ‘next’ button only works when all necessary fields have been filled in.
In the confirmation dialogue of the GINA registration, the field for the SMS pin was displayed and requested, even if the telephone number did not have to be entered. This has been corrected and the SMS pin is only requested if this is intended.
Release Date: September 24th, 2024
SEPPmail version: 14.0.0
Author: Birgit Grossmann
To prevent the accidential triggering of an appliance update, a confirmation code has to be entered from now on.
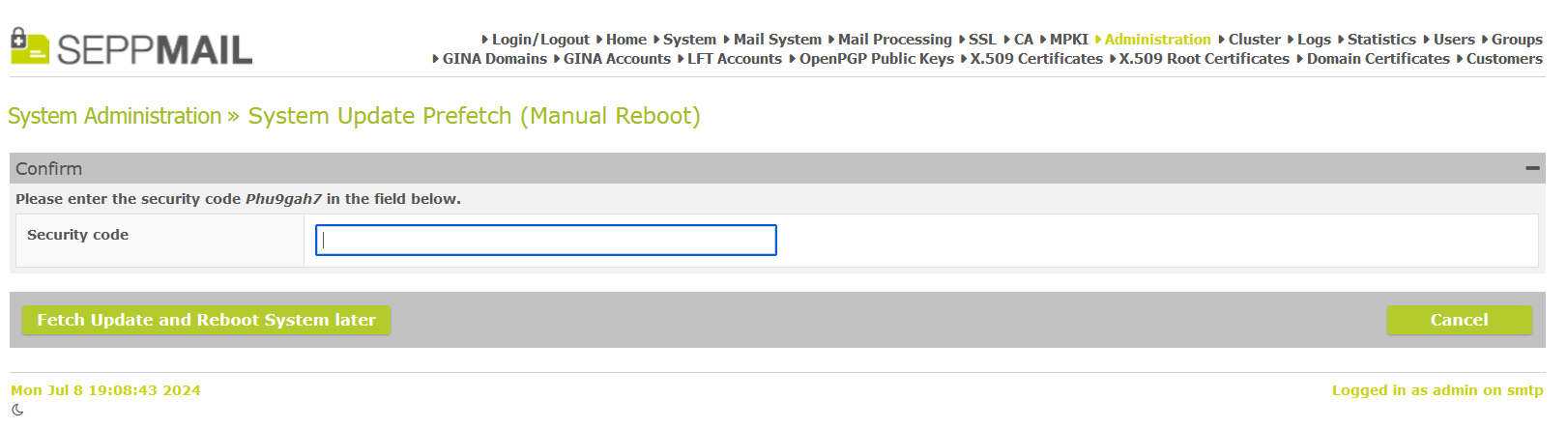
Confirmation code for system update prefetch
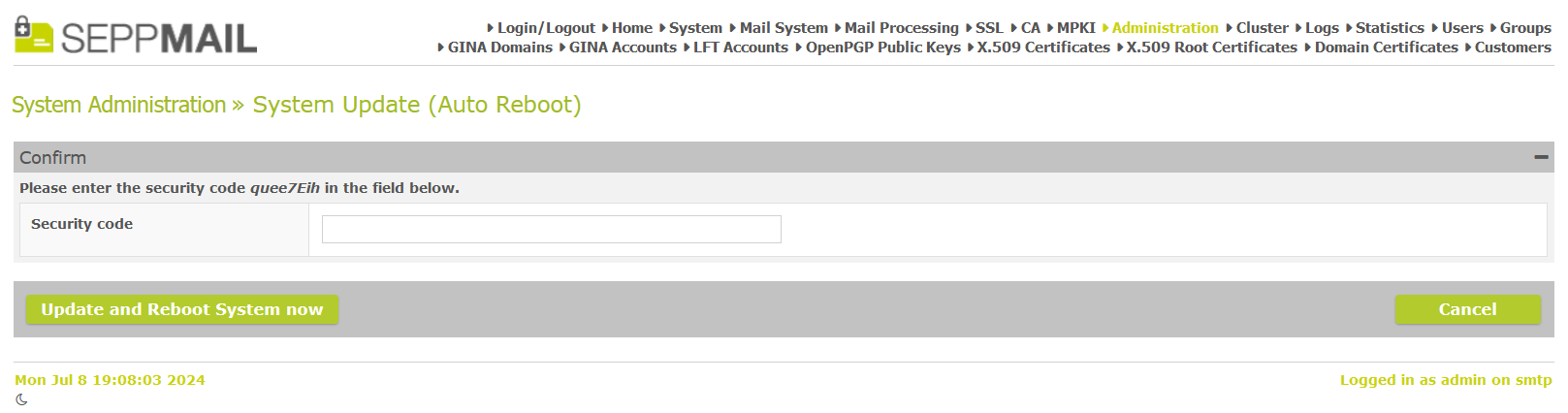
Confirmation code for system update
As of version 14, SEPPmail writes something to the audit log for almost all actions in the Admin GUI. Previously, this was only the case for a few actions.
As of version 14, you can no longer access the mailgraph.app if you have not previously logged in to the Admin GUI. The mailgraph.app is used to create statistics graphics and was previously accessible from anywhere and from anyone without any security.
Backup mails are now given a message ID.
Under System >> Advanced View there is now a System Settings section in which you can set the password of the system user "support". This is a user of the operating system (not an LDAP user).
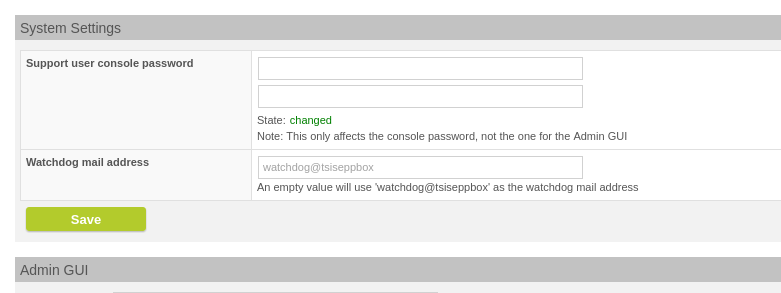
Set a Support user console password
In principle, you now have the option of downloading the private key after generating a new SSL certificate. This option is only available once after generation and then no longer.
Previously, if you had generated a CSR for an SSL certificate, which was then signed by an external CA, you could only import the signed certificate in text form. Now you can a) also upload the certificate as a file and b) import it all as PKCS7 aka P7B.
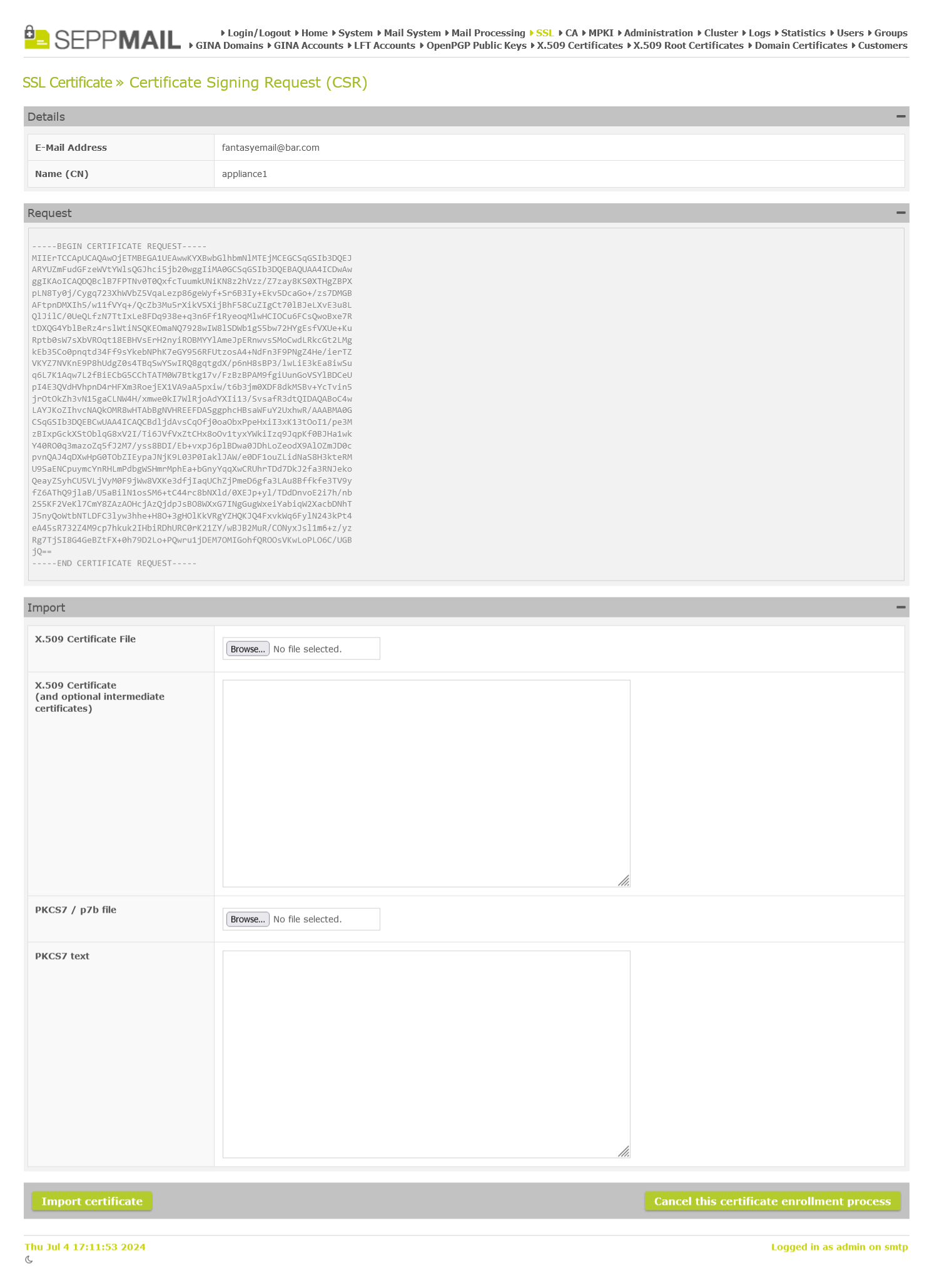
P7B Import from CSR
The list of GINA accounts can now be filtered according to the account status. Possible statuses are "all", "enabled", "locked by admin" and "locked temporarily".

Filter GINA accounts by account status
In the so-called console menu, it is now possible to display, add and delete routes for the system.
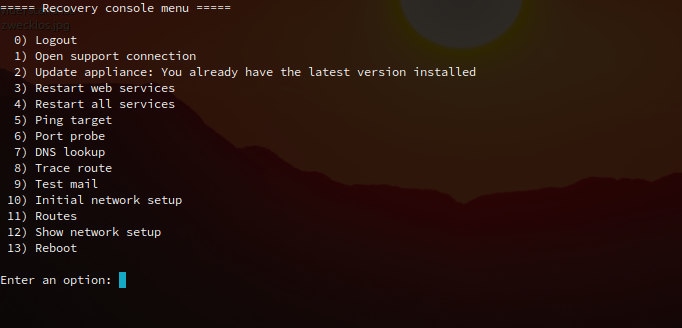
Recovery console menu - new option "11) Routes"
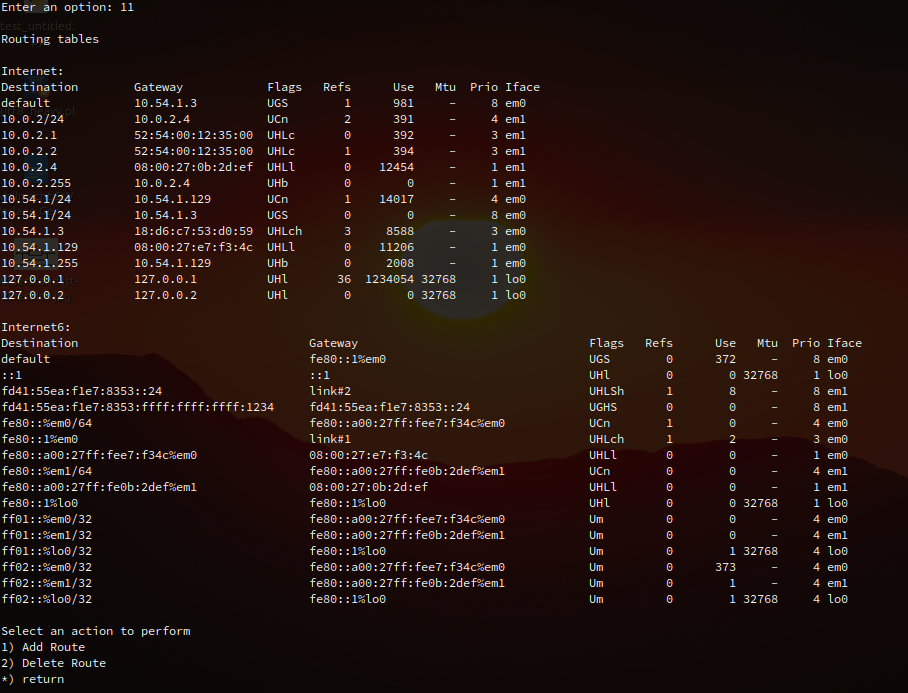
Edit routing in the console menu
As of version 14, bash is the default shell. As a result, every command entered in a bash shell is now also written to the audit log.
The Close button X in the pop-up was missing. This is fixed now.
From version 14, a snapshot of the database is created every night, but only if the system has an LFT partition. The restriction that an LFT license is required to mount an LFT hard drive no longer applies. The new backup is done on all systems with a database. The snapshots can then be restored under Administration >> Backup >> Restore. A full snapshot is always taken on Sundays, and incremental snapshots are taken on the other days. The snapshots of the last 14 days are kept.
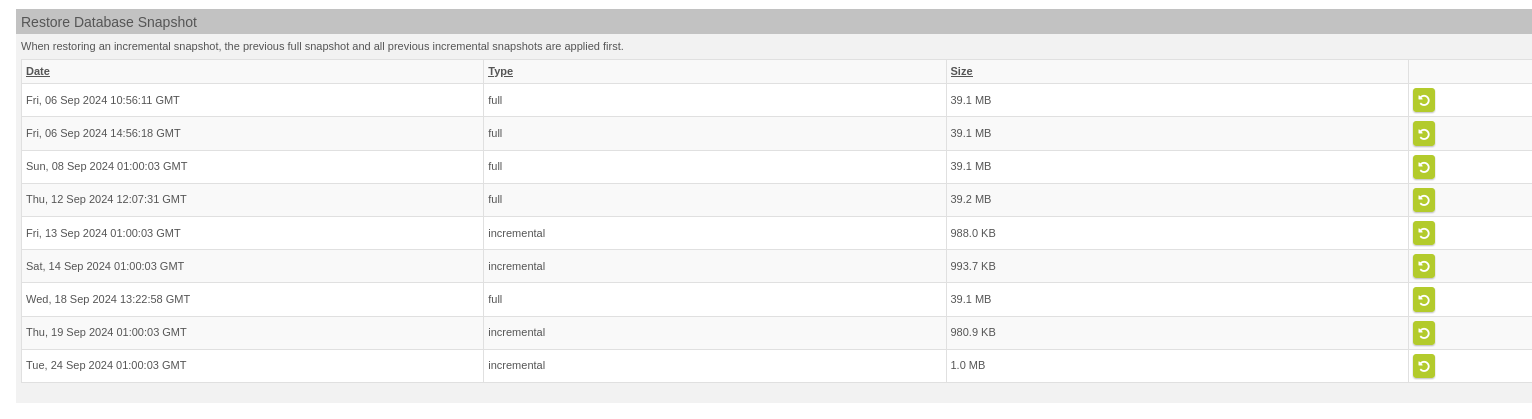
Restore database snapshot
If someone changes the IP address of the appliance, it is checked for the cluster whether one of the cluster members is already using this new IP address. If so, the IP is not allowed to be used.
The RestAPI can now also be used to query detailed statistics on the amount of memory used for LFT.
The appliance can now use S3 storage for LFT and cache mode. An LFT partition is still required for LFT.
The global settings are made under "GINA Domains".
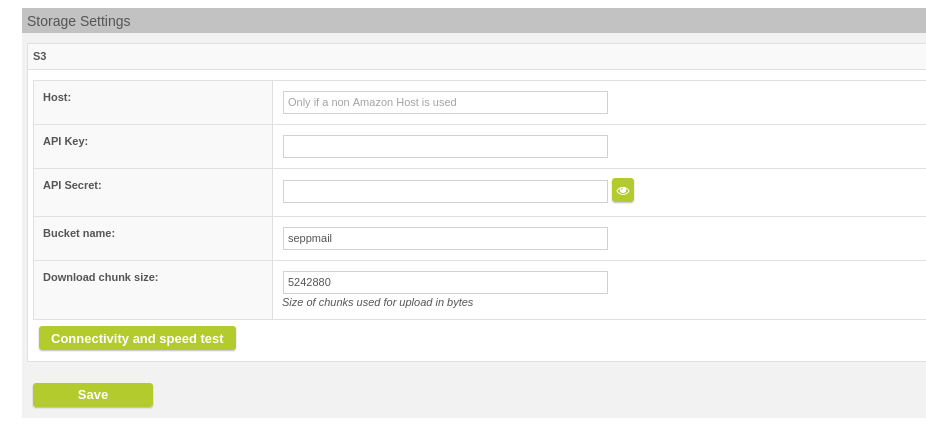
GINA Domains >> Storage Settings
For each GINA domain, there is then the option to use the global S3 storage configuration or another configuration.
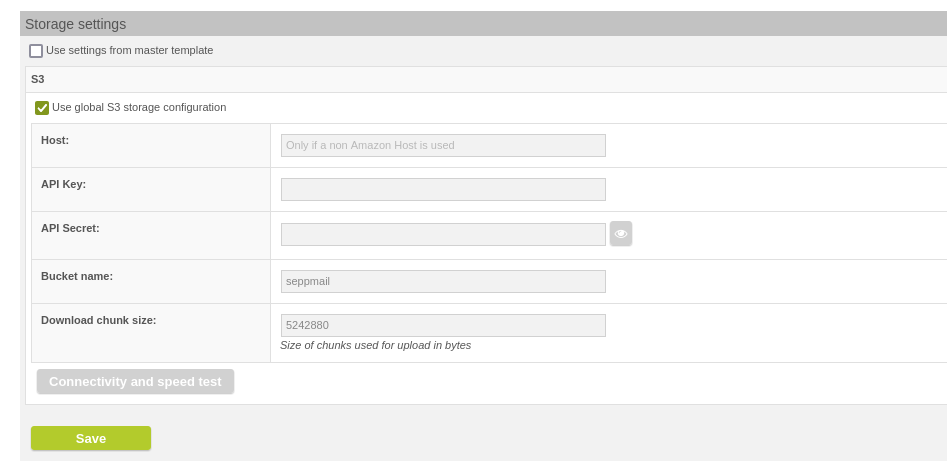
Per GINA Domain >> Storage Settings
With version 14, quotas can be set for LFT. Options:
The feature is based internally on extended fields, so-called "System Extended Fields".
The basic configuration is carried out in Mail Processing.
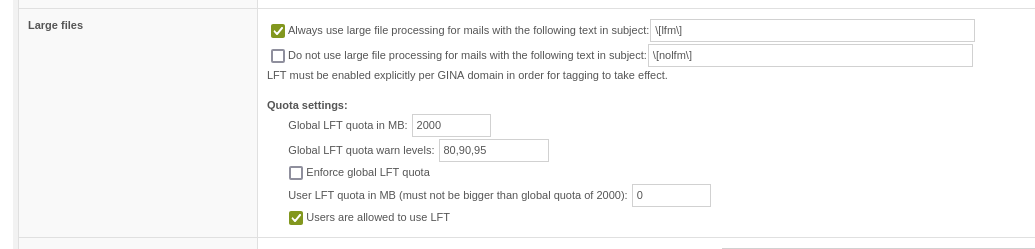
LFT Quota in Mail Processing > Large Files
This is followed by the setting for the customer. This can overwrite the global setting.
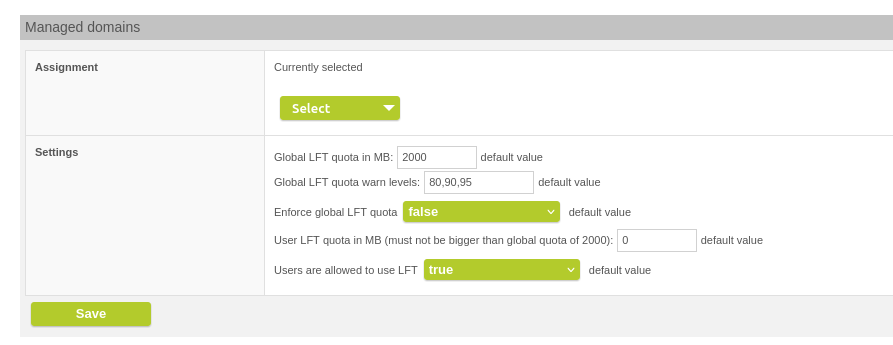
LFT Quota Customer Setting via Customers >> Edit customer > Settings
Then the setting in the managed domain: it inherits the customer's settings and overwrites them as well.
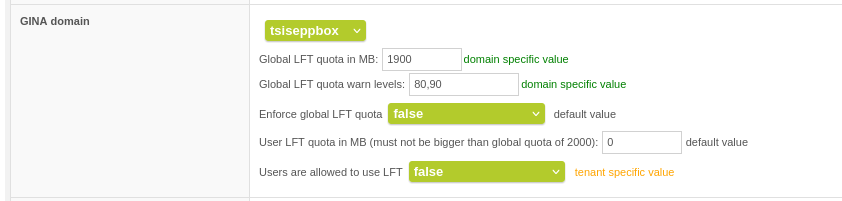
LFT Quota in Managed Domain via Mail System >> Edit managed domain
The mail processing groups of the managed domains then inherit and can overwrite the settings of the managed domains.
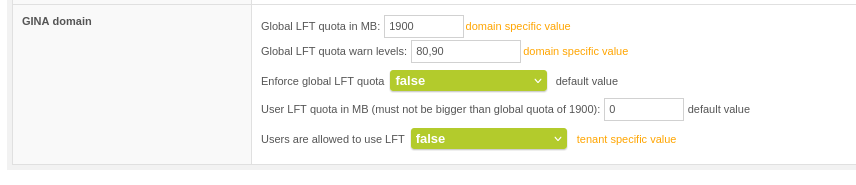
LFT Quota in Mail Processing Groups via Mail System >> Edit managed domain >> Edit mailprocessing groups
The user settings are more limited.
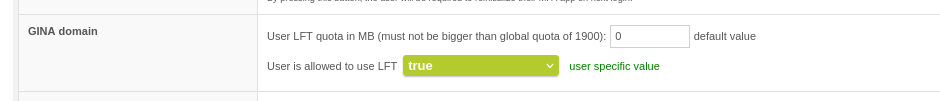
LFT Quota User Settings via Users >> User
We have changed a few things in the display of the system log and also added the display of the CfgServer log.
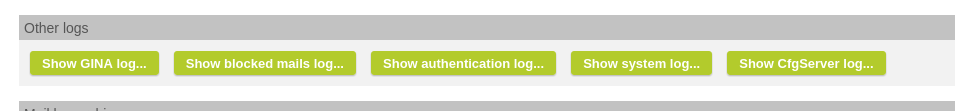
CfgServer log now available in Logs >> Other Logs
The syslog, audit log and CfgServer log can now be filtered properly, including by date and limiting the number of results.
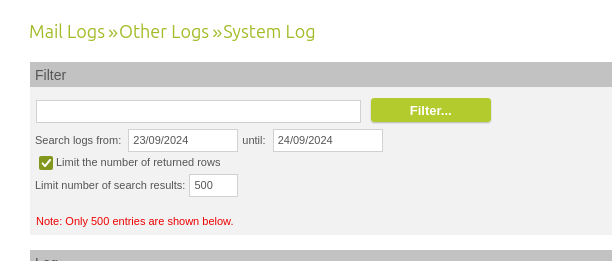
Log filtering - new options
It is now possible to switch between the log archive types "File" (maillog index files generated from the maillog files, default) or "DB" for the faster database approach, where maillog index files have been written to a database. Note that when switching from "File" to "DB", the memory requirement on the log partition increases by a factor of 3.5, see the note in the documentation.
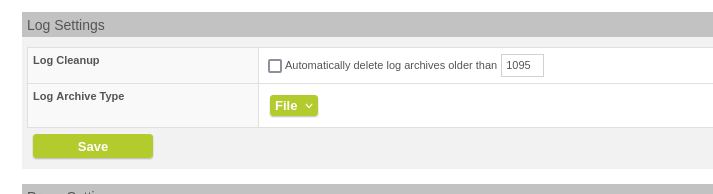
Set the log archive type
In the DB case, it is possible to page through the log data.
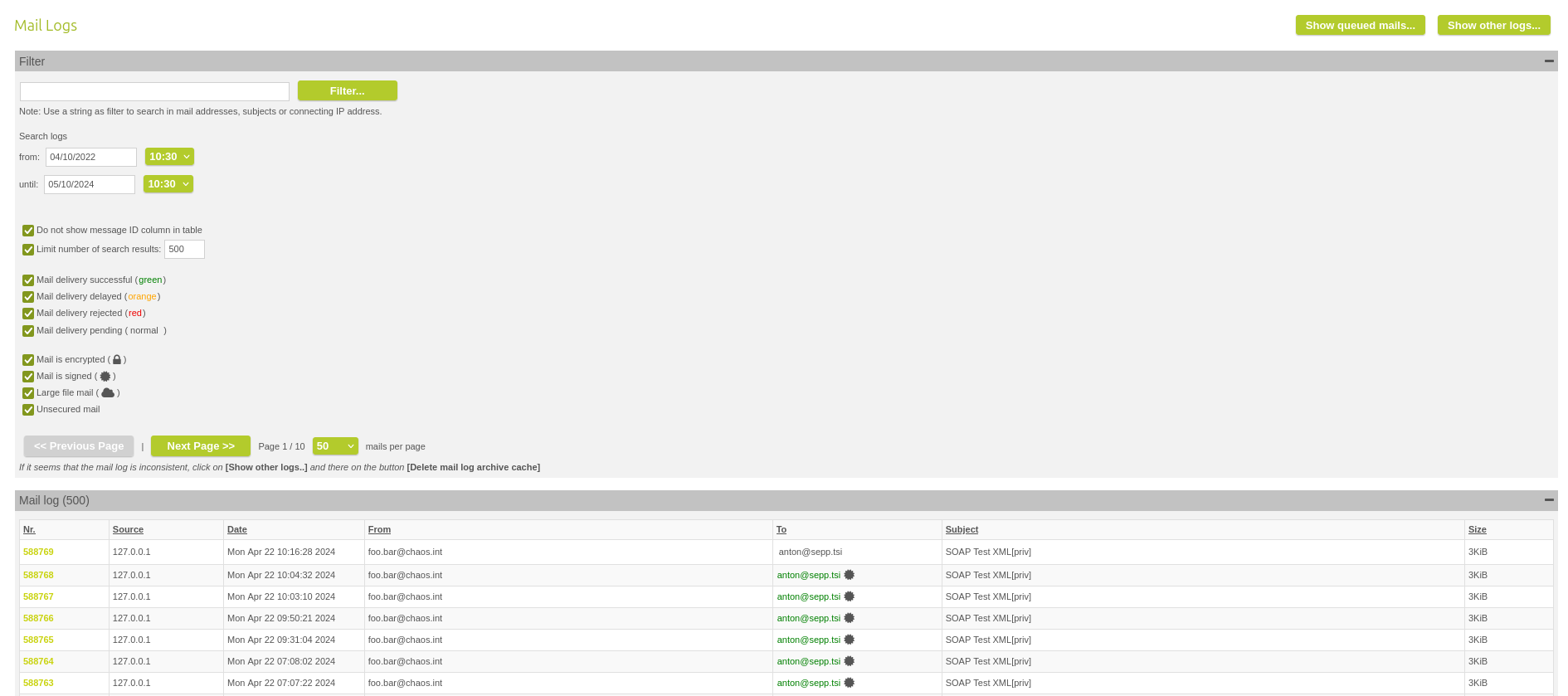
Page through maillog if DB is used
For preempt mode, you can now specify the error code returned by the RuleEngine in the Admin GUI under System Administration >> Maintenance >> Mail Processing.
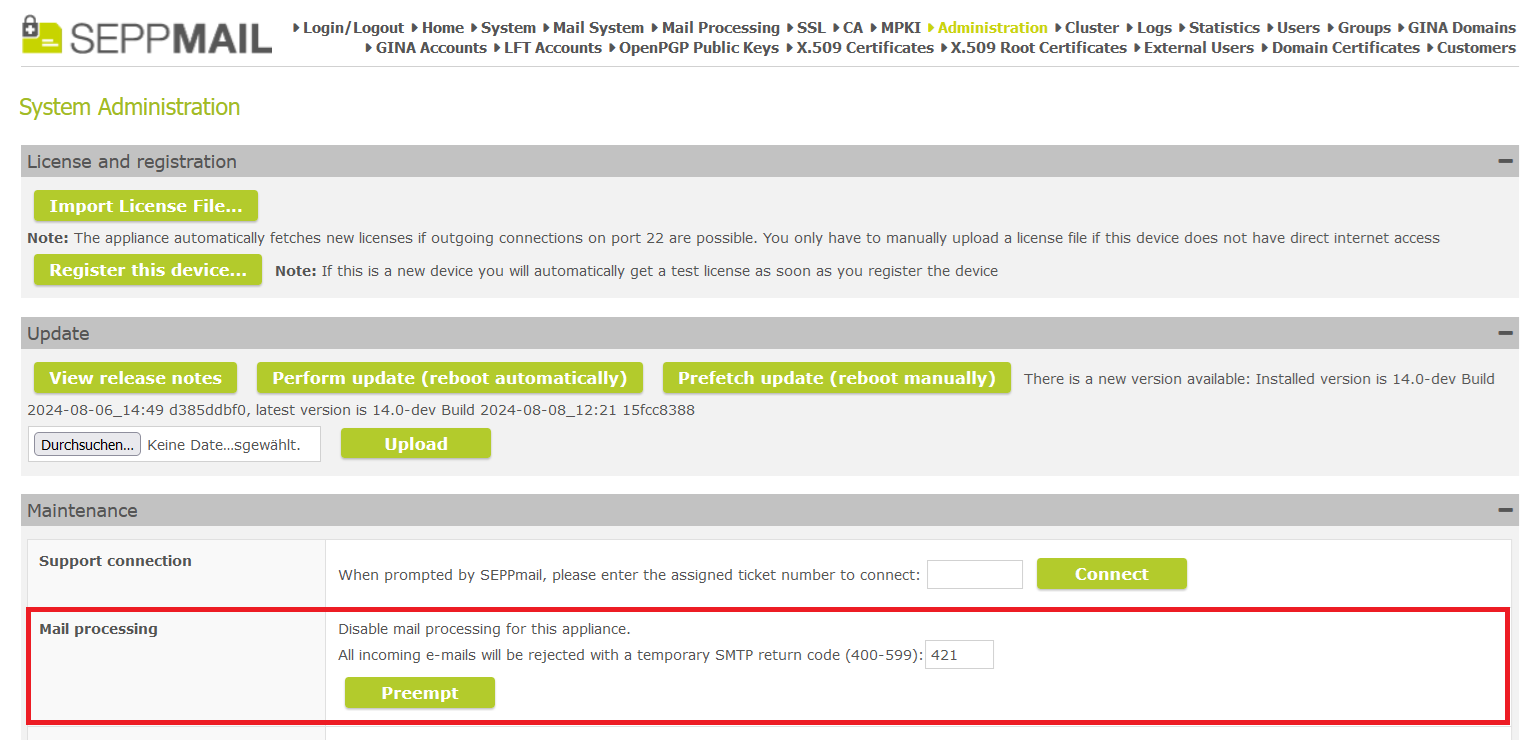
Define temporary SMTP return code
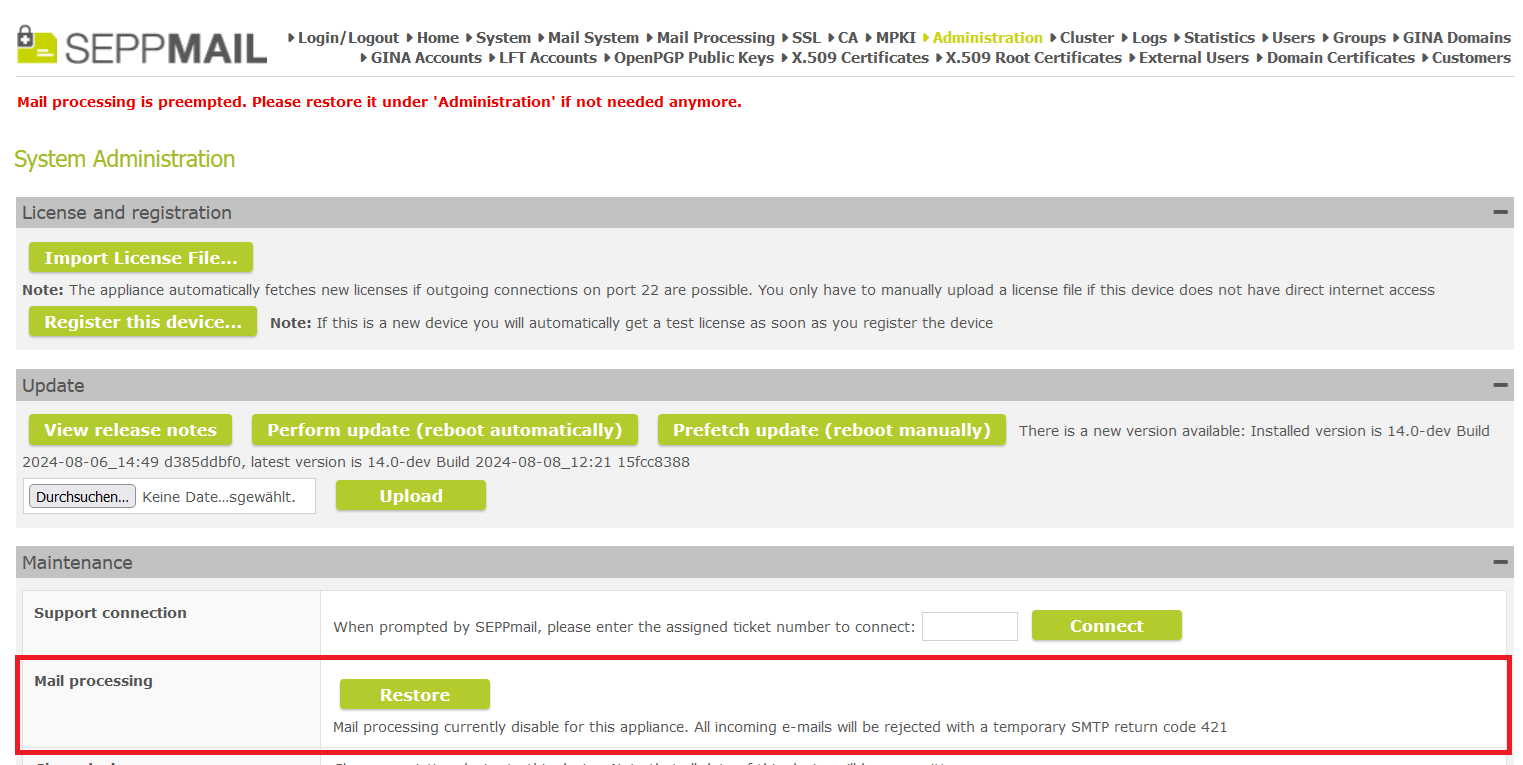
Restore Mail Processing
From version 14 on, OpenBSD 7.5 is used as the operating system.
In the daily report there is a CSV with statistical data of the domains. We have now added information on when the last domain certificate expires to this data, for normal S/MIME certificates, IME certificates and PGP domain keys.
Under Mail System >> Manual blocklisting / welcomelisting, you can now specify a validity period.
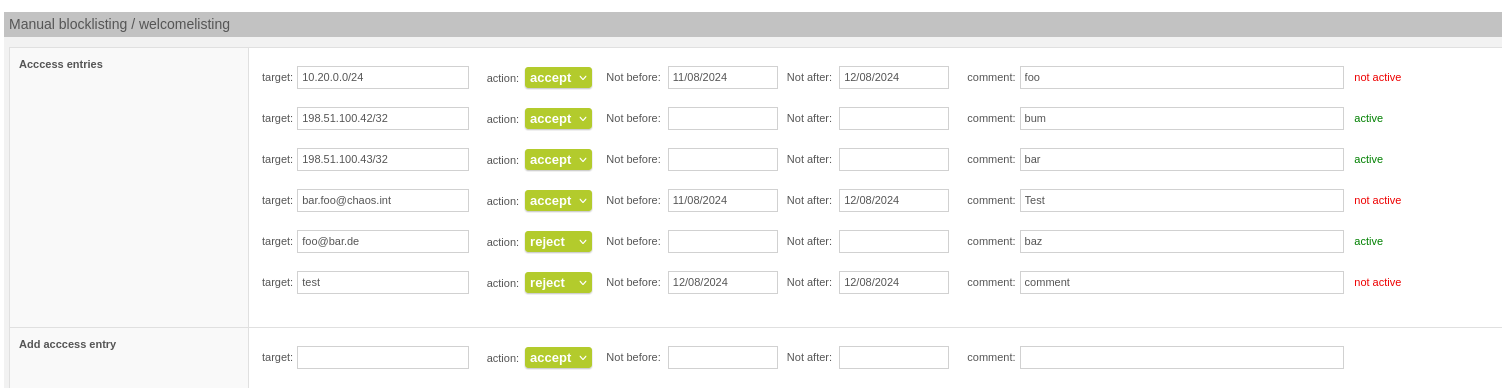
Manual blocklisting / welcomelisting with validity period
It is now possible to use the RestAPI to read, add, modify and delete the root CA certificates, which can be found under "X.509 Root Certificates".
It is now possible to use the RestAPI to customise all settings under "System".
This freeze was caused by re-indexing the maillog archive. The problem here was that the grep command of OpenBSD was very slow. We have adjusted this and now the re-indexing runs about 60 times faster.
Under System >> Advanced view there is now a System Settings section in which you can configure the sender address with which the watchdog sends its mails.
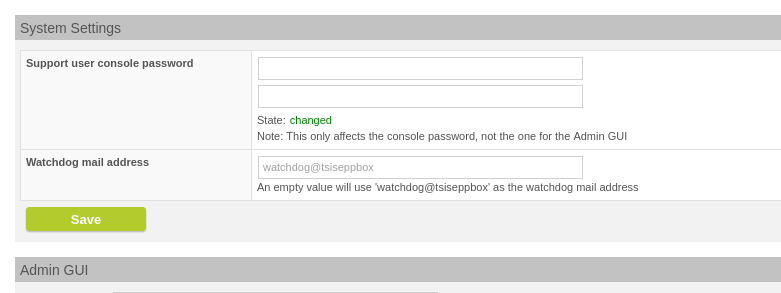
Configure the watchdog mail address (as sender)
With version 14, bootstrap was updated to 5.3.3 and jquery to 3.7.1.
We have added a few email headers which make it easier to distinguish (and possibly filter) the GINA-generated mails. The new headers are:
Previously, the time of the last successful login was always logged, but not the time of the last failed login attempt. From now on, this will be logged and displayed in the Admin GUI.
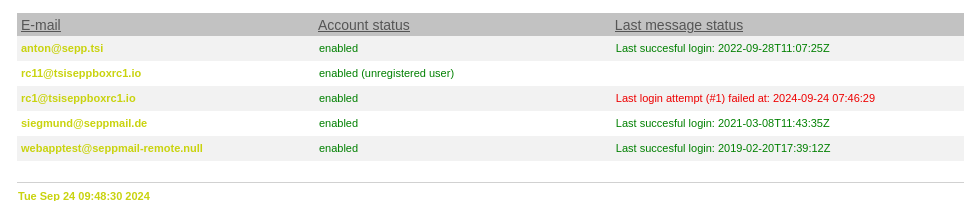
Failed login attempts
Furthermore, in the general GINA domain settings in the GINA cleanup settings, you can set how long the login attempts are saved.
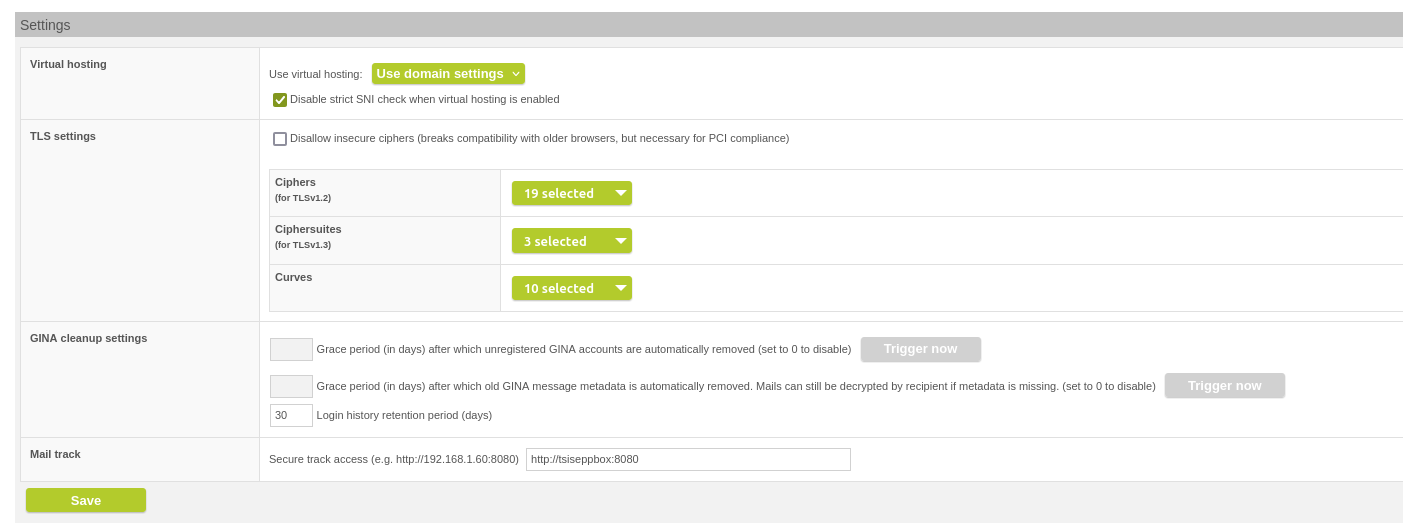
Retention period for logins
It is now possible to configure whether or not the "copy to myself" checkbox is displayed in the GINA GUI when writing a GINA mail.
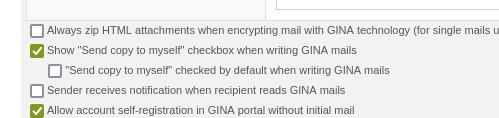
Option for showing the "copy to myself" checkbox
Previously there was the problem that either both domain certificates and key material of local users were allowed for unregistered users - or neither. It was not possible, as the configuration in the Admin GUI suggested, to configure the domain certificate download independently of the user certificates. This works now.
--- end of document ---