Tip: All changes are tracked in the Gateway documentation, see the information in the last row of the documentation agreement.
For the latest 14.0 releases, see https://downloads.seppmail.com/extrelnotes/140/ERN14.0.html
For the latest 13.1 releases, see https://downloads.seppmail.com/extrelnotes/131/ERN13.1.html
IMPORTANT - Starting with release 14.1.0, every system will switch to multi-customer mode.
Normally the impact should be small and only be noticeable through some additional log entries, additional table columns in the Admin GUI, and the grouping of "per customer" data.
Although we have not observed any issues as a result of the change, changes in behaviour always carry a certain risk. For this reason, we recommend creating a backup before the update and, if necessary, creating a snapshot in virtual environments.
SEPPmail Gateway news via Statuspal As of July 2025, SEPPmail Secure E-Mail Gateway customers and partners can register for Statuspal messages under the link https://seppmail.statuspal.eu/#subscribe. Information about the Gateway is now also published here.
14.1.4 Bugfix Release
- Release Date: October 1st, 2025
- SEPPmail version: 14.1.4
- Author: Birgit Grossmann
This release will be the last release in the 14.1 branch and enable the update to version 15.0.
- 14.1.4 Bugfix Release
Admin
Switch to SEPPmail SAAS
In the Administration > Update section, information regarding the Cloud product can be opened via the button "Switch to SEPPmail SAAS".
Button for more information on SAAS
Bug in route.pl
- Internal Reference: 52168
- Issue Type: Bug
- Docs Link: none
An error in a script for setting routes via the console menu prevented users from setting routes correctly. This has been fixed now.
A while ago, it had been decided that if no new password has been set for the system support user, the system would create a random password. However, in case of new installations with network instabilities this could lead to problems.
Therefore the password is set back to the default "support" and the admin receives a warning in the Admin GUI and in the daily digest to please set a new password.
Snapshot Restore - text correction
- Internal Reference: 51880
- Issue Type: Maintenance
- Docs Link: none
There were copy-paste errors in the snapshot restore message, which spoke of deletion.
The message now correctly says, "If you really want to restore the snapshot, please press restore again."
Background tasks
pkill in kallallprocesses kills $PPID and $$
- Internal Reference: 51980
- Issue Type: Bug
- Docs Link: none
An error in a script, which was supposed to terminate all unnecessary processes when connecting to a cluster, also terminated the process for the cluster connection, resulting in inconsistent cluster configurations. This has been fixed now.
Documentation
Backup using scp - examples added
- Internal Reference: 52363
- Issue Type: Maintenance
- Docs Link: Backup examples
Two examples were added to the "backup using scp" documentation.
Licensing
Kronos Release
- Internal Reference: 49392
- Issue Type: Maintenance
- Docs Link: none
Our license and update server (called LUS) was replaced by the new Kronos at the end of September 2025. This may result in updates that cannot be received or licences that cannot be obtained in some circumstances, but based on our observations so far, this should only happen in isolated cases.
Logging
Long script names result in invalid newsyslog.conf files
- Internal Reference: 52204
- Issue Type: Bug
- Docs Link: none
An error in generating the log rotation configuration caused it to end with an error, which meant that the maillog log file was not indexed. This has been fixed now.
Defect DB Logging Mail Cache stops "Logs" page from loading
- Internal Reference: 51610
- Issue Type: Maintenance
- Docs Link: none
With DB-based logging, there used to be a problem whereby if the DB was defective, the entire log page could not be loaded, meaning that the user was unable to rebuild the DB. Now, the log page is displayed in the event of an error, but without any log entries. You can then switch to "Other Logs" and delete the maillog cache, which will generate a new DB.
MPKI
Link Net::SSLeay against OpenSSL
- Internal Reference: 51924
- Issue Type: Bug
- Docs Link: none
DigiCert has changed/adjusted its TLS encryption, and a Perl module we use, which previously used LibreSSL, is unable to cope with this. We have now changed this so that it uses OpenSSL, which resolves the issue.
Issues with fullnameregex default parameter
- Internal Reference: 51894
- Issue Type: Bug
- Docs Link: none
An error in the code meant that default values were not transferred to the domain-specific settings in the DigiCert MPKI Connector if the relevant fields were left blank (which is actually the default behaviour). This has been fixed.
GlobalSign MPKI and German Umlauts
- Internal Reference: 52138
- Issue Type: Bug
- Docs Link: none
There were once again problems with character encoding in the GlobalSign MPKI Connector, which we have fixed.
Network services
Add check_smtp to nrpe.conf
- Internal Reference: 52134
- Issue Type: Feature
- Docs Link: check_smtp
For the NRPE (Nagios Remote Plugin Executor), the new check command "check_smtp" has been added.
Rest API
- Internal Reference: 52393
- Issue Type: Maintenance
- Docs Link: none
Following last month's auth token rotation, an error occurred when querying GINA accounts via the RestAPI because the format of the auth token had changed. This has now been fixed and the REST output has been adjusted to
"authToken": {
"token": "9OTz6cC0y4JflZt57xxdLOgpI8KaLtUG",
"creationTime": "2025-09-30T12:34:40Z"
}
Rule engine
Verification of e25519 ARC seal fails
- Internal Reference: 52086
- Issue Type: Bug
- Docs Link: none
An incorrect handling of Ed25519 keys in the Perl module used for handling ARC signatures led to an exception and thus to the termination of the processing of an affected email. We have patched the module and notified the maintainer.
Remove MIME epilogue before adding S/MIME signature
- Internal Reference: 51998
- Issue Type: Maintenance
- Docs Link: none
Due to causing problems in MS Outlook, the MIME epilogue is removed before the S/MIME signing.
Technical background: In a MIME-structured email, the part that follows the MIME structure is called the epilogue. Its structure is not standardised, so it usually is ignored. Due to problems with MS Outlook, it is now completely removed before the signing.
Webmail (GINA)
Password reset not working if GINA user has no phone number set
- Internal Reference: 52023
- Issue Type: Bug
- Docs Link: none
An error in the GINA GUI meant that when a password reset was requested via text message, the telephone number was not transferred and therefore no text message could be sent. This has been fixed now.
Search for logged in GINA user jumps to profile settings if domain cert/key search is not activated
- Internal Reference: 52082
- Issue Type: Bug
- Docs Link: none
A bug in the GINA code caused logged-in users who wanted to search for key material and had domain certificate search disabled to be redirected to their profile settings. Users can now search for certificates again.
Add autocomplete=off for web.app
- Internal Reference: 52328
- Issue Type: Bug
- Docs Link: none
As part of this ticket, we have set autocomplete to off for the GINA GUI login for the email and password input fields in order to prevent automated filling or the collection of the data entered.
GINA in MS Edge on mobile phone
- Internal Reference: 52328
- Issue Type: Bug
- Docs Link: none
Due to technical changes in the Edge browser on iOS, the former solution with reloading CSS no longer works. For this reason, we have removed the reloading of CSS, adapted the information texts and kept them general, and the OK button now is always displayed.
SEPPmail.cloud UI Feedback
- Internal Reference: 52013
- Issue Type: Maintenance
- Docs Link: none
If a user registered with the GINA GUI and already existed in the user system, they would receive a message stating that the user had been successfully created, but with a red background. This led to confusion. This message is now green.
14.1.3 Bugfix Release
Admin
"Blocked Mails" Logs cannot be opened
- Internal Reference: 51117
- Issue Type: Bug
- Docs Link: none
Due to a typo, nothing was displayed in the Blocked Mails view. This has been fixed.
Wrong split regex for country codes
- Internal Reference: 51351
- Issue Type: Bug
- Docs Link: none
The regular expression used to split the country codes for an SSL certificate request was incorrect, thereby preventing the issuing of a new SSL certificate.
GUI: Only show Managed Domain Certificates when searching
- Internal Reference: 51247
- Issue Type: Bug
- Docs Link: none
There was an error in the filter for domain certificates, meaning that certificates not originating from the SEPPmail Managed Domain Service were also displayed in the search results. As we always assume that only one certificate per domain is available in the SEPPmail Managed Domain Service, we only ever display one certificate there. If two were found because the second had been added manually locally, the wrong certificate might have been displayed. This has now been corrected.
Tip: Manually imported domain certificates can be found under "S/MIME domain certificates".
Column title missing
- Internal Reference: 51208
- Issue Type: Bug
- Docs Link: none
The heading for the column "Encryption licences (used/limit)" was missing from the customer overview.
Clustering
Fix the "Is Current Maintenance Mode"
- Internal Reference: 50929
- Issue Type: Maintenance
- Docs Link: Cluster Setup
It is now possible to set the maintenance node directly in the Cluster menu.
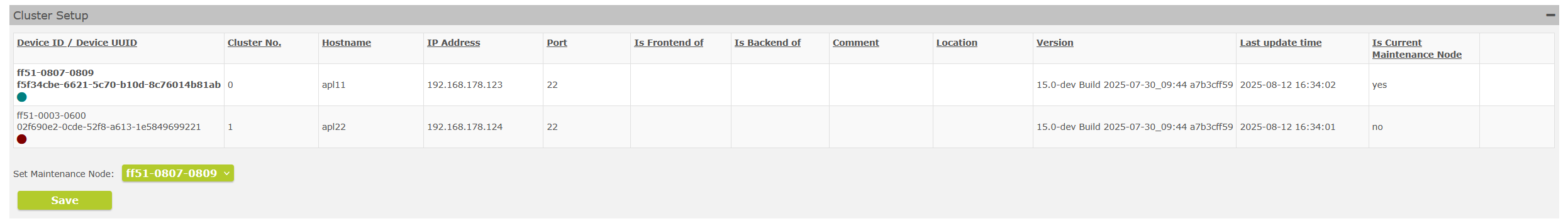
Selecting the maintenance node
Large files
- Internal Reference: 50929
- Issue Type: Maintenance
- Docs Link: none
We fixed an issue with bypass uploads where the size specifications for the uploaded file did not match the size of the uploaded file.
MPKI
Improvements of the SectigoEU MPKI Connector
- Internal Reference: 51263
- Issue Type: Bug
- Docs Link: none
Several small bugs were fixed in the SectigoEU MPKI connector.
SwissSign MPKI special characters - fix_double_utf8
- Internal Reference: 51272
- Issue Type: Bug
- Docs Link: none
A UTF8 encoding problem in the SwissSign MPKI Connector has been fixed.
DigiCert: Fullname Regex path incorrect
- Internal Reference: 51593
- Issue Type: Bug
- Docs Link: none
Due to the use of an incorrect file name, the regular expression used in the DigiCert MPKI Connector to split the full name into given name and surname was not found, and therefore the splitting did not work.
GlobalSign adaption CAB
- Internal Reference: 50929
- Issue Type: Maintenance
- Docs Link: none
An error in the GlobalSign MPKI Connector has been fixed. Even though the other party could easily have assembled the CommonName=GivenName Surname themselves from GivenName and Surname, the CommonName still has to be included in the request to GlobalSign. This has been implemented now.
Protection pack
Issuing a watchdog message when sanesecurity signature updates fail
If the option for the unofficial signatures for ClamAV is selected but the signatures cannot be loaded, a warning appears on the status page.
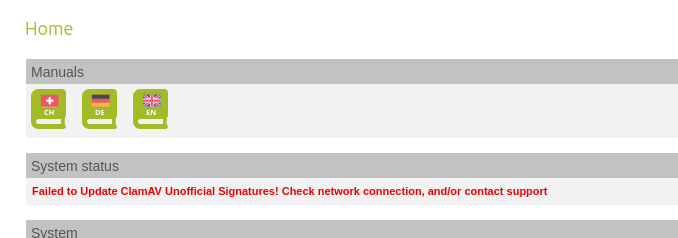
Warning if loading of Unofficial signatures for ClamAV fails
RestAPI
Attribute typo
- Internal Reference: 51266
- Issue Type: Bug
- Docs Link: none
Due to a typo in the attribute name, it was not possible to reset the password for a GINA account via the RestAPI. This is fixed now.
List of domains with managed S/MIME certs via API not working
- Internal Reference: 51436
- Issue Type: Bug
- Docs Link: none
The ticket fixes an error in the RestAPI where querying the certificates of the managed domains returned an empty list even though certificates were available.
Do not deactivate extended fields when managed domain is deleted
- Internal Reference: 51594
- Issue Type: Bug
- Docs Link: none
This ticket fixes a bug in the RestAPI where deleting a managed domain disabled all extended fields.
RestAPI General Maintenance
- Internal Reference: 51210
- Issue Type: Maintenance
- Docs Link: none
Several small bugs were fixed in the RestAPI.
Rule Engine
Fuglu: Mail with leading whitespace in from address
- Internal Reference: 51237
- Issue Type: Bug
- Docs Link: none
It could happen that email addresses were saved with a leading whitespace in the system. Since this was then classified as an invalid email address, no account was created for the address and the email was not processed. Now all whitespaces before and after the email address are removed before saving it in the system.
Interrupt Key Server Search
- Internal Reference: 50859
- Issue Type: Maintenance
- Docs Link: Key server
In the RuleEngine, we have the option of querying external LDAP servers for S/MIME certificates or PGP keys for encryption. For some customers, however, this query takes so long that it brings all email traffic to a standstill. For this reason, a timeout of five seconds has now been implemented.
Webmail (GINA)
GINA v1: Make Admin Email Field Mandatory
- Internal Reference: 50982
- Issue Type: Maintenance
- Docs Link: Admin Email
The "Admin Email" is now a mandatory field when creating a GINA domain.
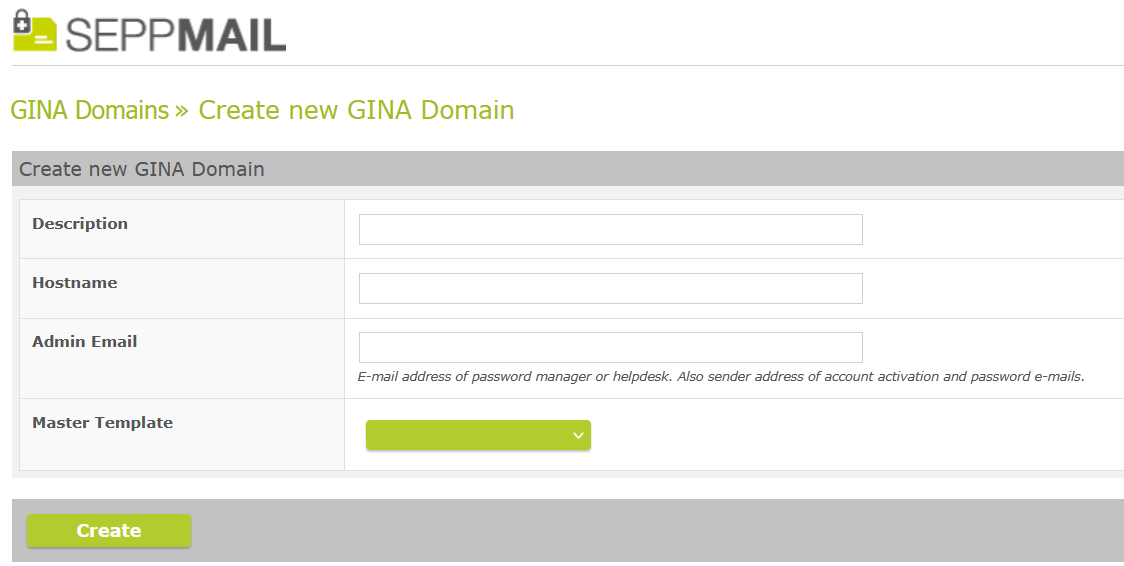
Entering the Admin Email
GINA: Reset Password via SMS: Allow for 3 SMS retries
- Internal Reference: 51101
- Issue Type: Maintenance
- Docs Link: Reset by SMS
In the past, a password reset by SMS could only be attempted once. Now it is possible to attempt the SMS reset three times. After that, the hotline needs to be contacted.
Authtoken rotation
In the past, the Authtokens of GINA Domains, used by the Outlook Addin, have not been rotated automatically. Now the two new settings "Authtoken rotation period" (time until a new token is created and distributed) and "Authtoken validity time" (time until the user needs to reauthenticate) have been implemented. Please see the documentation for a full explanation of these settings.
We recommend to update the Outlook AddIn to version 2.0.25 (otherwise the rotated tokens might not be received correctly).
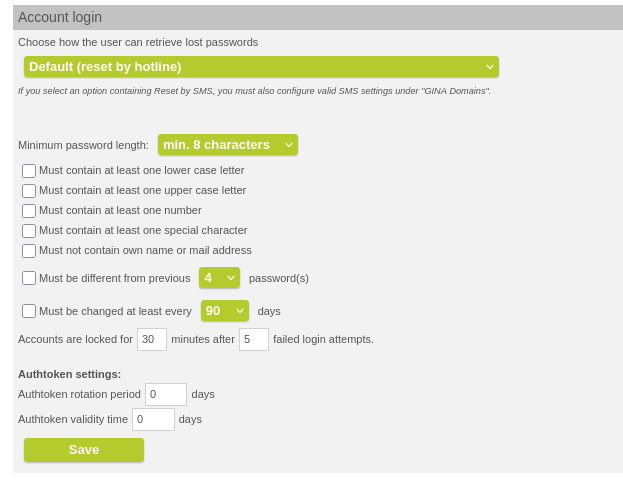
Authtoken settings
Add possibility for line breaks in SMS templates
- Internal Reference: 51432
- Issue Type: Feature
- Docs Link: Text in GINA
This ticket was caused by the problem that iOS devices separate passwords in their messenger with a hyphen to create a line break. This led to support cases because users did not know whether the hyphen was part of the password or not. Since we can only transfer plain text here, we cannot suppress a line break in the messenger. For this reason, we have added the option to insert a manual line break into the SMS text using a
tag in the language settings of the GINA domains. This allows you to start the password at the beginning of a new line, in the hope that the password is not longer than a whole line and thus prevent the line break.
br tags in text templates
14.1.2.1 Hotfix Release
System services
Race condition between clusterd and restartservices
- Internal Reference: 51148
- Issue Type: Bug
- Docs Link: none
There was a race condition between two services, which then terminated each other. This resulted in the watchdog no longer running because it assumed that one of the services was still running. This has been fixed now.
Webmail (GINA)
No searching for certificates on the GINA website
- Internal Reference: 47209
- Issue Type: Bug
- Docs Link: none
There was an issue with the anonymous certificate search. This has been fixed now.
14.1.2 Bugfix Release
IMPORTANT - Version 14.1.2 will most likely generate new Diffie-Hellman parameters after the update, which may take up to 20 (or more) minutes.
Admin
Add Check if swapctl fails to return swap partition values, resulting in div by 0
- Internal Reference: 50035
- Issue Type: Maintenance
- Docs Link: none
In the Admin GUI there was a problem in the update page if the system had no swap partition and we searched for its size. Now it is checked beforehand whether a swap partition exists.
Database
In the support menu of the console it is now possible to restore daily DB snapshots.
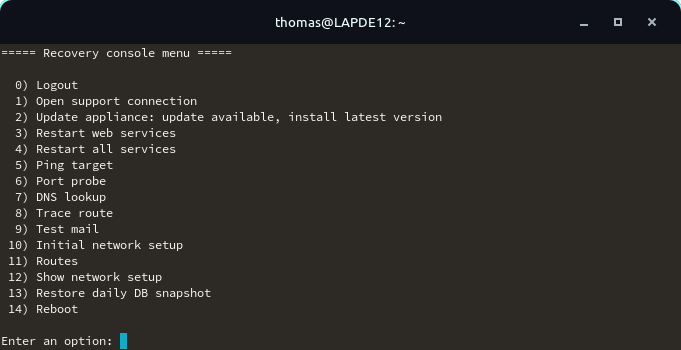
New option 13 for restoring DB snapshots
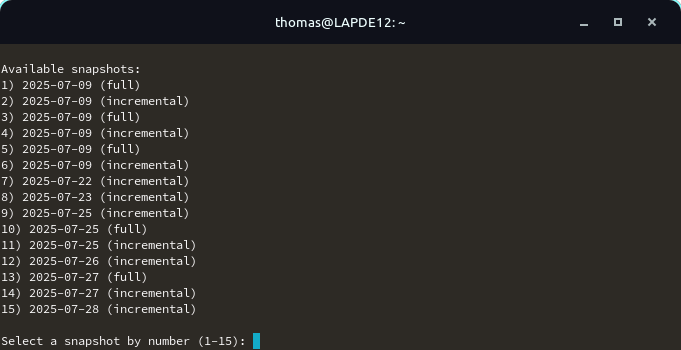
Selecting the snapshot for restoring
Large Files
file.app: fix session handling
- Internal Reference: 50400
- Issue Type: Maintenance
- Docs Link: none
Several potential vulnerabilities were found in file.app (which is used for the LFT-bypass upload). These have been fixed.
Logging
Newsyslog will not send HUP if command is specified
- Internal Reference: 50451
- Issue Type: Bug
- Docs Link: none
In the previous release, we had a bug that caused the syslog not to be notified to open a new mail log file after rotating the mail logs, and therefore no further logs were written for the RuleEngine.
This has now been fixed.
MPKI
Bug MPKI Digicert skip_approval
- Internal Reference: 50618
- Issue Type: Maintenance
- Docs Link: none
There was a problem with the DigiCert Connector with the skip_approval setting. In the course of the other DigiCert/CertCentral changes regarding given name, surname and pseudonym, this problem was also fixed.
Sectigo EU - new end point
- Internal Reference: 50904
- Issue Type: Maintenance
- Docs Link: none
Just like DigiCert, Sectigo now offers an endpoint in the EU, and we implemented the endpoint as the SectigoEU MPKI Connector.
Method not found in GlobalSign MPKI connector
- Internal Reference: 50421
- Issue Type: Bug
- Docs Link: none
In the GlobalSign MPKI Connector code, due to a copy-paste error, a function was introduced which was was not defined in the context. As a result, the GlobalSing connector no longer worked. Now everything is defined again.
pendingEntryDN incompletely set
- Internal Reference: 50809
- Issue Type: Bug
- Docs Link: none
When the RuleEngine initiates the issuance of an S/MIME certificate, we enter this in the database as ‘pending’ and the CfgServer periodically checks for new ‘pending’ entries and then creates the certificates.
Due to an adjustment in the SwissSign MOKI connector, the situation arose that this adjustment could not cope with the shortened information entered in the ‘pending’ entry and therefore no certificate was issued. This is fixed now.
Adjustement to the new DigiCert API
Like the other MPKI providers, DigiCert and DigiCert CertCentral now also require the specification of given name and surname or pseudonym. This has been implemented and the regular expression can be customised in the DigiCert/CertCentral settings in the Admin GUI.
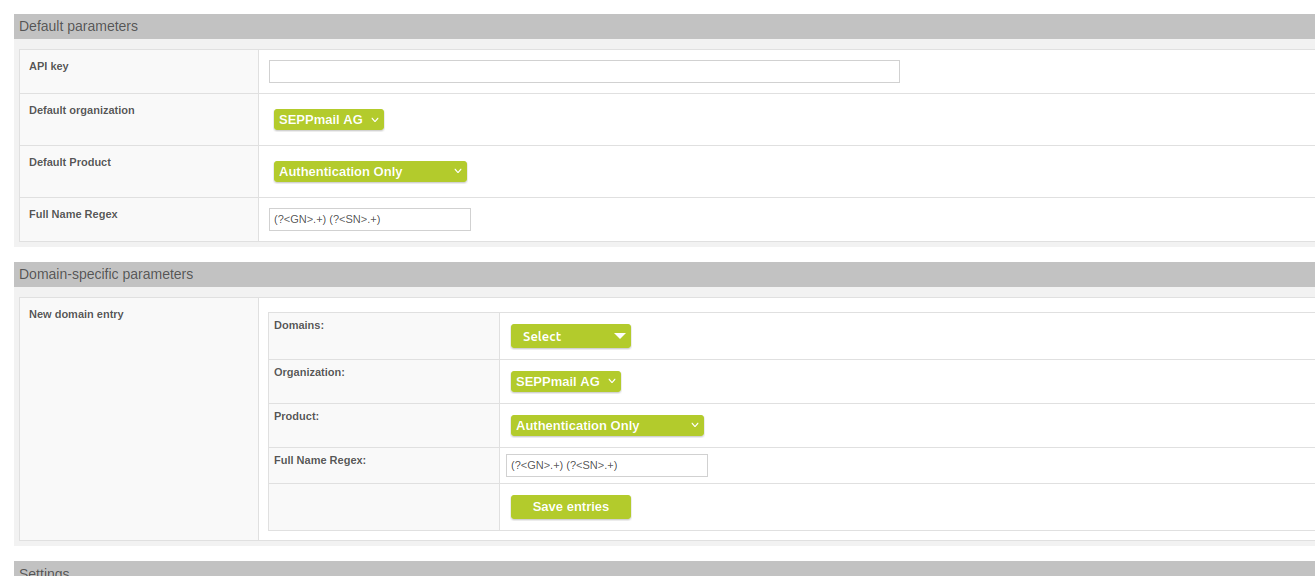
DigiCert / DigiCert CertCentral new field "Full Name Regex"
RestAPI
Exchange SSL Certificate
- Internal Reference: 49474
- Issue Type: Feature
- Docs Link: none
The following four new RestAPI end points are available:
/ssl
/ssl/transfer_to_cluster
/ssl/generate
/ssl/csr
These map the functionality of the SSL section of the Admin GUI.
Customer Import no longer working
- Internal Reference: 50645
- Issue Type: Bug
- Docs Link: none
Due to stricter schema validation, it was no longer possible to import customers via the RestAPI. This is now possible again.
Error in GINA configuration
- Internal Reference: 50621
- Issue Type: Bug
- Docs Link: none
When a GINA user's password was reset via the RestAPI, the password was saved incorrectly and this led to another registration when the GINA user logged in again.
The password is now correctly saved during the SMS password reset.
Rule Engine
Usage of content-type.name may lead to false positive script detection
- Internal Reference: 50245
- Issue Type: Bug
- Docs Link: none
A simplified evaluation of the file names of attachments in mails led to false-positive detection of scripts, even though they were images. We now evaluate the usual fields for the file names before we access the last option (which was currently causing the problem).
Triple wrapping fails if activated in an Encryption Policy
- Internal Reference: 47933
- Issue Type: Bug
- Docs Link: none
Triple wrapping is now also done in the encryption policies.
Webmail (GINA)
CWE-200 in GINA Portal of SEPPmail Appliance
- Internal Reference: 50199
- Issue Type: Maintenance
- Docs Link: none
A security check revealed that the login data in the GINA GUI could be restored from the cache and therefore someone could read the credentials of another user of the same browser. This has now been rectified by a redirect after login.
ZIP - problems with umlauts
- Internal Reference: 50359
- Issue Type: Bug
- Docs Link: none
In GINA there was a problem with ‘Download all as ZIP’ with file names containing UTF8 characters. This has been fixed now.
Problems with GINA templates after v14.1.0
- Internal Reference: 50263
- Issue Type: Bug
- Docs Link: none
An incorrect naming of placeholders led to texts for the password notification being included in places where they had no place. This has been fixed now.
Styles for GINA v1 mails not correctly replaced
- Internal Reference: 50294
- Issue Type: Bug
- Docs Link: none
A bug caused the CSS styles in GINA mail not to be replaced correctly. This has been fixed now.
14.1.1.2 Hotfix Release
Logging
Logrotation maybe not working because of missing PID file
- Internal Reference: 50299
- Issue Type: Bug
- Docs Link: none
There was a problem in the log rotation where the absence of a PID file caused an error. This has been fixed now.
Webmail (GINA)
LFMKey code creates too many Config::Client leading to too many LDAP connections
- Internal Reference: 50242
- Issue Type: Bug
- Docs Link: none
Since 14.1.0 SEPPmail has been using the so-called LFMKeys to encrypt cached GINA mails again. A bug in the code probably caused too many LFMKeys to be created on many systems in the past. This was not a problem as long as they were not used. But now they are being used. To decrypt a cached GINA mail, the LFMKeys are now retrieved. A bind was made to the LDAP for each LFMKey and stored in the LFMKey object. In the case of many LFMKeys, this resulted in too many connections to the LDAP and thus overloading it.
This has been fixed now.
14.1.1.1 Hotfix Release
GUI Alert regarding new update mechanism
For many customers, there is currently an alert in the SEPPmail Gateway GUI with the text "We are changing to a new update mechanism for SEPPmail appliances. Connection attempt to new server failed - please make sure this device is able to connect via port 22 to 94.130.170.135. (This message will vanish as soon as the successful connection has been made.)"
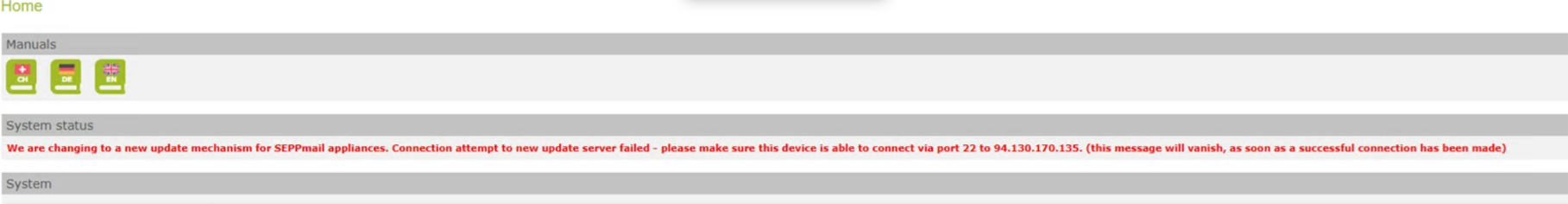
Explanation: SEPPmail is preparing the migration of the licence and update server (LuS) from Neuenhof in Switzerland to the new LuS called Kronos in the Hetzner data centre in Germany.
This is a Kronos connection test, which performs a simple ssh access from the respective SEPPmail Secure E-Mail Gateway via IP address to Kronos via IP.
As the corresponding Firewall rules are IP-based for most of our customers, this test is explicitly IP-based. The FQDN (targets update.seppmail.ch and support@seppmail.ch, see Setting up the firewall / router) will not be changed until the changeover date.
As soon as you open the access from your SEPPmail Secure E-Mail Gateway to the specified IP 94.130.170.135 via port 22 SSH, the message will disappear.
Admin
Clone Device does not restart or shutdown specific nodes
- Internal Reference: 50160
- Issue Type: Bug
- Docs Link: none
In the script which is used to clone a SEPPmail node, there was an error which prevented a clone process from starting. This works again now.
Cron
Missing newline at the end of the crontab prevents cron from running
- Internal Reference: 50158
- Issue Type: Bug
- Docs Link: none
A syntactic error in the root user's crontab (explicitly, a missing blank line at the end) meant that the crontab could not be installed and therefore no cronjob could run. This is fixed now.
14.1.1 Bugfix Release
Admin
SEPPmail SMS password reset complexity cannot be changed
- Internal Reference: 49986
- Issue Type: Bug
- Docs Link: none
There was a problem saving the password complexity in the GINA settings. It works again now.
User cannot be saved after changing the "Full name"
- Internal Reference: 49453
- Issue Type: Bug
- Docs Link: none
There was a problem when saving user changes for e.g. "Full name" in the Admin GUI, because the password was always checked and did not meet the required criteria, although the password was not changed at all.
This has been fixed now, and only if the password is changed, it will be checked.
Mail log access limited
- Internal Reference: 48723
- Issue Type: Bug
- Docs Link: none
A bug in the code had the result that users in the Admin GUI who were assigned to the readonly admin group could not adjust the filter settings of the mail log view. This has now been fixed.
Feature Request for message history: Show mails per GINA user and sender (LFT account)
It is now possible to display the list of sent and received GINA messages in the GINA user details.
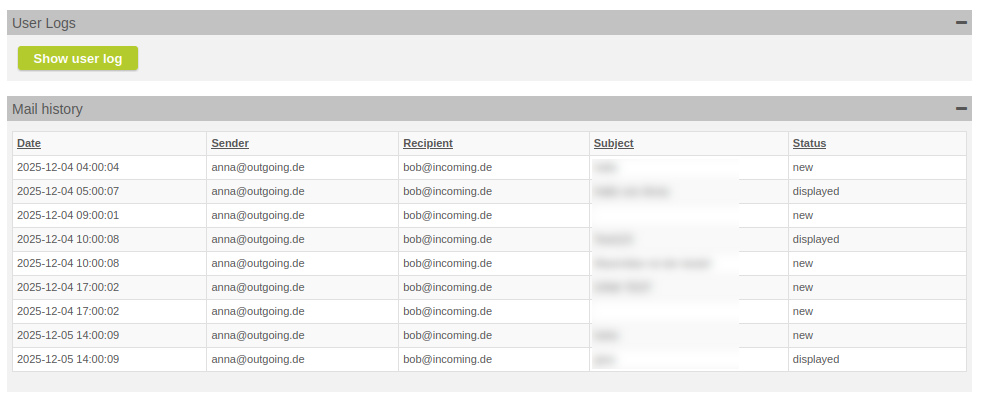
Show mail history of GINA user
Backup
Cluster Backup (sending only one backup file in a cluster configuration)
- Internal Reference: 44823
- Issue Type: Feature
- Docs Link: Cluster Setup
From version 14.1.1, only the cluster member defined as the maintenance node in the cluster sends the DB backup via E-mail. The other members send their system backup.
In the cluster setup overview, this information can be found in the new column "Is Current Maintenance Mode".
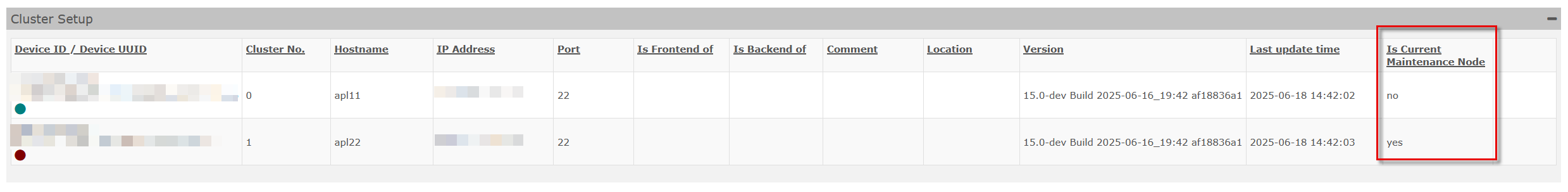
Column shows whether node "Is Current Maintenance Node"
CfgServer
Prevent double decode_base64 for additional credentials password
- Internal Reference: 49690
- Issue Type: Bug
- Docs Link: none
When generating the Postfix data for the additional smarthost credentials, there was a problem that the password data was double base64-decoded and therefore the password was no longer correct. This has been fixed now.
Logging
Bug re-report: MPKI Warning
- Internal Reference: 47371
- Issue Type: Bug
- Docs Link: none
A somewhat naive handling of the contents of the MPKI errors log file led to the daily digest always warning of MPKI connector errors, although it was only a message that the file had been rotated. This is now prevented and only actual MPKI errors are logged.
Database Logging: Possible Race Condition
- Internal Reference: 49708
- Issue Type: Maintenance
- Docs Link: none
There was a problem with DB-based logging where, when the DB was created, an interim rotation of the log files meant that data was not transferred to the DB. This is now taken into account.
MPKI
SEPPMail MPKI Swisssign - Pseudonym Handling needs space (blank)
- Internal Reference: 49764
- Issue Type: Bug
- Docs Link: none
With the pseudonym handling in the SwissSign MPKI connector, there was a problem that SwissSign requires a space after the "pseudo:". This is now added.
MPKI GlobalSign - givenName, surname, and pseudonym in CSR
As with SwissSign, there is now the option for GlobalSign to include a given name, surname or pseudonym via the field "Full Name Regex" when generating S/MIME certificates via the GlobalSign MPKI Connector.
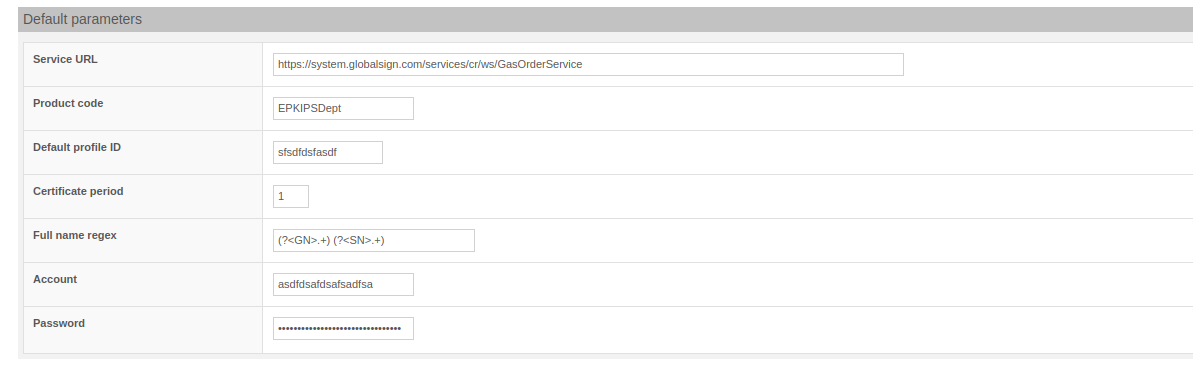
GlobalSign new field "Full Name Regex"
Multi-Tenancy
[default] and [none] customers do not exist. _process_multi_customer has a bug in Filter.
- Internal Reference: 50022
- Issue Type: Bug
- Docs Link: none
When automatically switching to the multi-customer system, there was an error so that the [default] and the [none] customer were not created automatically. This has been fixed now.
RuleEngine
Error message "Verify failed: error:80000009:system library::Bad file descriptor" when signing certificate is expired
- Internal Reference: 41455
- Issue Type: Maintenance
- Docs Link: none
There was the problem that in case of an S/MIME signature validation failure, no detailed information was offered in the RuleEngine log. This has been improved and more information should now be provided.
14.1.0 Feature Release
Admin
Add ability to copy a ruleset
A displayed ruleset can now be copied to the clipboard.
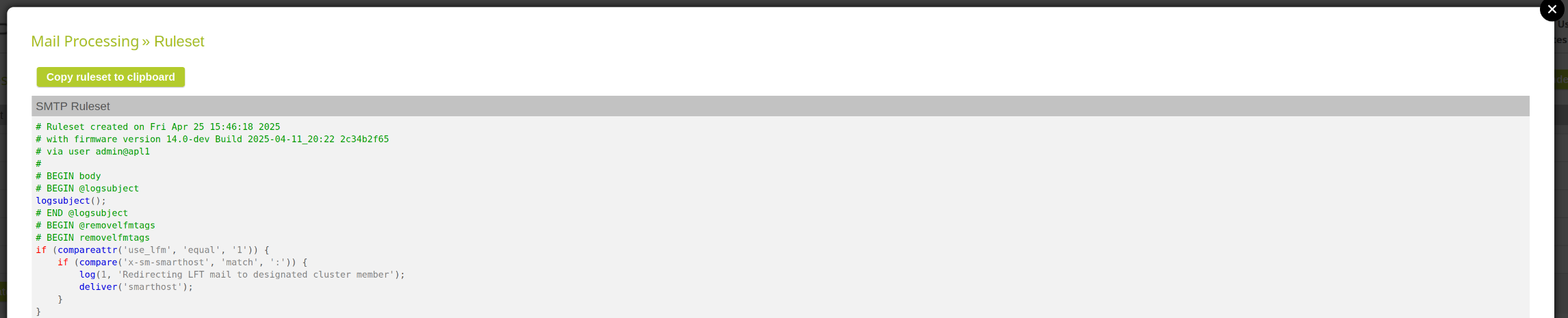
Copy ruleset to clipboard
Log-Copy Function
In the detailed view of log entries there is now a "Copy log to clipboard" button to copy all necessary data of the log entry. This is particularly helpful for the support, as customers sometimes do not provide enough information and so everything is ready with just one click.
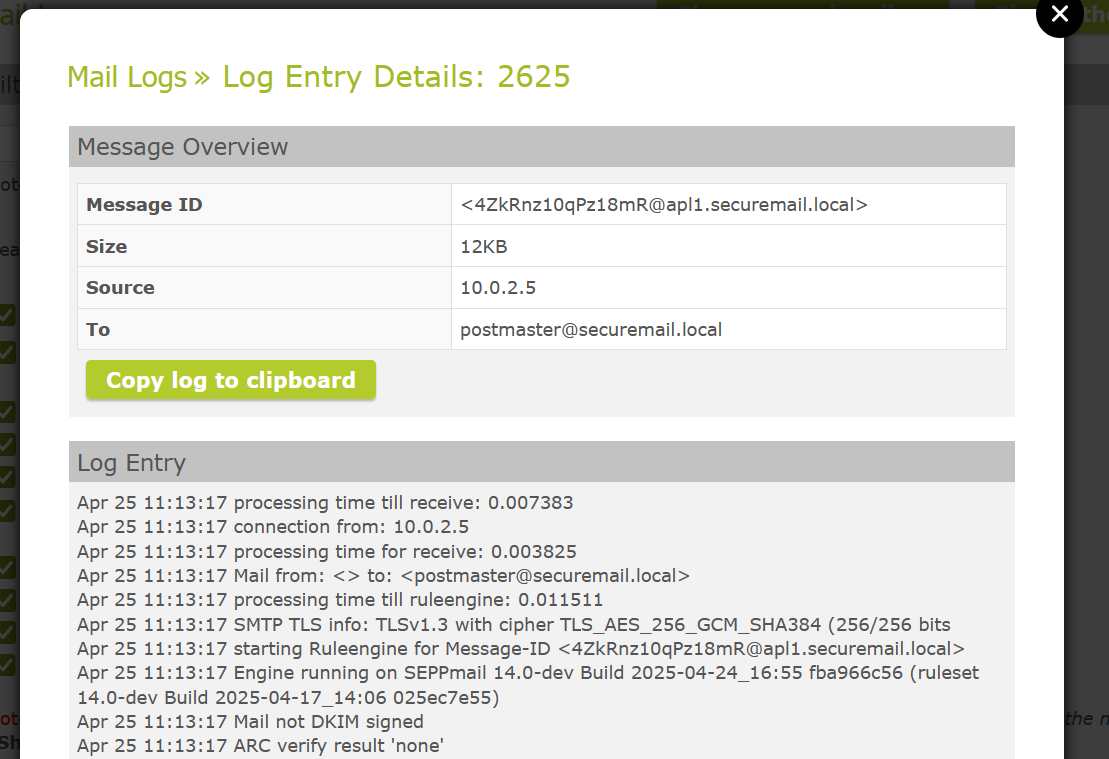
Copy log to clipboard
Add the ability to set the MTU in the initial network setup
- Internal Reference: 45891
- Issue Type: Feature
- Docs Link: none
When configuring the network settings via the console, you can now also specify the MTU as long as you are not using DHCP.
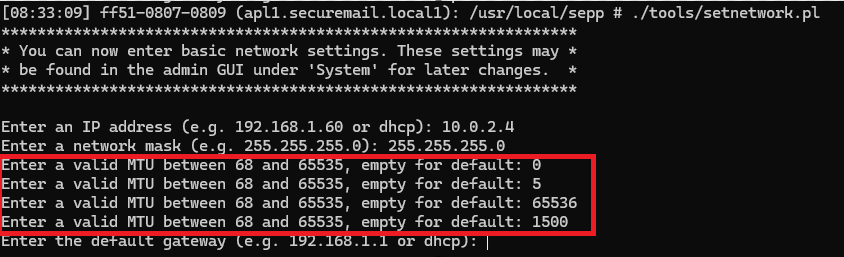
Option to specify the MTU in the console
"Verbose" Startup Modus
- Internal Reference: 22852
- Issue Type: Feature
- Docs Link: none
We have now made the startup much more verbose. Some customers, especially those with larger installations, found that the startup took a very long time without it being clear in the console what was actually being done (and whether anything was being done).
With the additional information, the state of the startup phase should be much more transparent.
Switch to RC Version
It is now possible to select the update channel in the Administration. Options are "Release", "RC" (release candidate, and "Dev" (development).
"Release" is the default. "RC" and "Dev" should only be used after consultation or at your own risk.
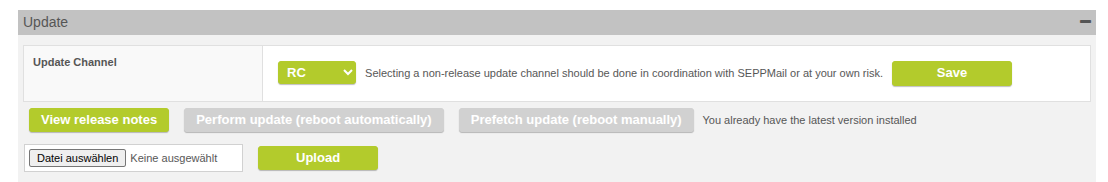
Select the update channel in the Administration
DB Migration Job
- Internal Reference: 48120
- Issue Type: Maintenance
- Docs Link: none
When switching from file-based logging to DB-based logging, the DB was not immediately generated in the background. This meant that if you switched to the log display in the Admin GUI, this process was triggered by the Admin GUI. It was not clear to the user whether and what was currently happening and after the normal Admin GUI timeout they also received an error message.
Now we trigger the generation of the DB directly after the changeover and in the Admin GUI you receive an information that the process is currently being carried out and might take some time.
SEPPmail Feature Postscreen - remove from Admin UI
- Internal Reference: 31498
- Issue Type: Maintenance
- Docs Link: none
We have removed the postscreen configuration from the Mail System page. It was never used even if it was activated.
CfgServer
Add CertCentral to CfgServer::get_mpki_data and make use of it
- Internal Reference: 36708
- Issue Type: Maintenance
- Docs Link: none
Since the DigiCert and CertCentral MPKI are basically the same and only differ in the URL (CertCentral for Europe because of GDPR, and DigiCert for the rest, that is the USA), we have standardized this and replaced various input fields with dropdown lists, so that you can only select things that are available for your setup. However, DigiCert and CertCentral can still be selected separately.
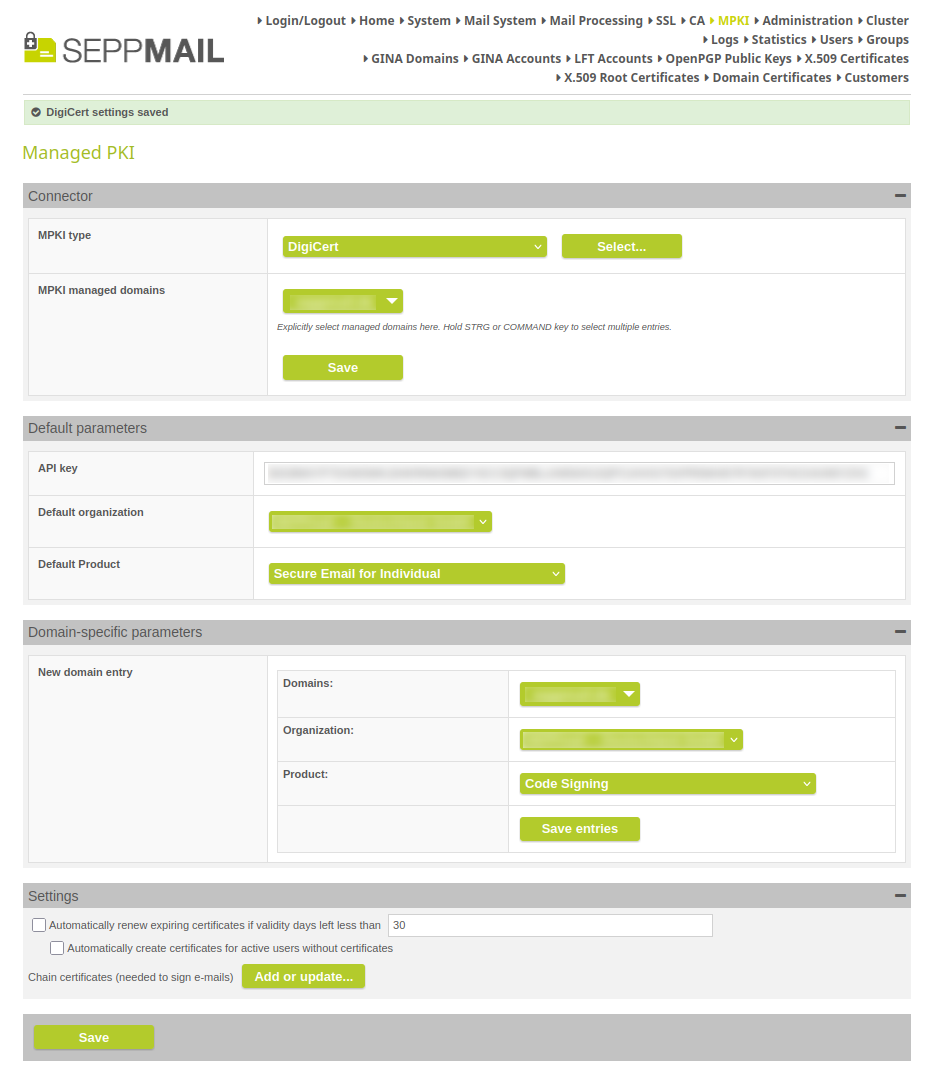
New standardized input design for MPKI entries
Cron
Set MAILTO
- Internal Reference: 48926
- Issue Type: Maintenance
- Docs Link: none
A customer experienced the behavior that they received mails from the cron of the SEPPmail Gateway. We have now set MAILTO="" in the rcrontab to prevent any notification via mail.
Large files
syncLFM should delete files on remote site if local files have been deleted and expireLFM should only cleanup local storage files if they belong to the processing system
- Internal Reference: 48991
- Issue Type: Bug
- Docs Link: none
A customer experienced the error that in a cluster for which LFM was configured and the local storage was used, expired LFM messages were not deleted correctly because one cluster member deleted files while another synchronized them back to it. As the reference to the file was deleted by the deletion process of one member, this file then remained in the local storage and this filled up as a result.
There is now a corresponding mechanism that prevents this kind of misbehavior.
Logging
shell_logging
- Internal Reference: 42570
- Issue Type: Bug
- Docs Link: none
All scripts now use a uniform logging mechanism to store their log output in a central location. This will help with all future troubleshooting and maintenance.
Provide meaningful log messages if or if not a policy is applied
- Internal Reference: 41613
- Issue Type: Maintenance
- Docs Link: none
Previously, the encryption policies never reported in the log if they were not executed because one of their preconditions was not met.
As some customers were not satisfied with the absence of all the log entries that would indicate that the policy had been executed, we now explicitly state in the log when a policy is not executed.
MPKI
Changes for SwissSign Certs
- Internal Reference: 46462
- Issue Type: Maintenance
- Docs Link: none
The Browser Forum has made new specifications for certificates and the certification authorities are now implementing them. This means that given name and surname must always be specified in the request or (permitted for certain products) the pseudonym attribute can be used.
We have implemented this with this ticket. However, as we do not store the first name and surname separately in the database, we have to split the full name using a regular expression. This is specified via Full name regex. By default, we assume the schema "Given Name Surname", so that the default regex would split this into gn="Given Name" sn="Surname".
Multi-Tenancy
Every SEPPmail system is now multi-tenant
- Internal Reference: 18825
- Issue Type: Feature
- Docs Link: none
In the code, it became increasingly confusing and complex to handle the multi-tenant and non-multi-tenant environment. Since it also makes no difference in terms of licenses, all SEPPmail systems turn into multi-tenant systems with version 14.1.
Normally the impact should be small and only be noticeable through some additional log entries, additional table columns in the Admin GUI, and the grouping of "per customer" data.
One noticeable thing is that under "GINA domains" the grace periods settings are currently set by the client. In a later release, these two settings will be removed.
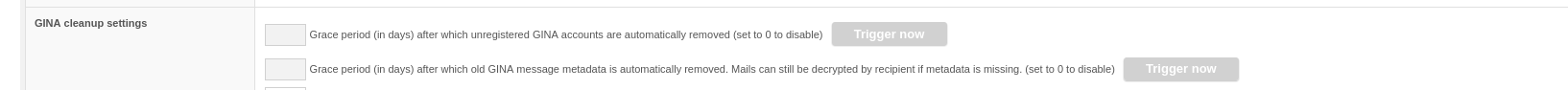
GINA Cleanup Settings currently with Grace Period fields
Although we have not observed any issues as a result of the change, changes in behaviour always carry a certain risk. For this reason, we recommend creating a backup before the update and, if necessary, creating a snapshot in virtual environments.
Pentest
Validate cert chain before importing it
For the import for X.509 Root Certificates we added a check of the Root CA Certificate Chain to see whether a certificate has expired. This includes a flag to import the certificate anyway.
Adjustments were also made for the import of X.509 Root Certificates via the REST API.
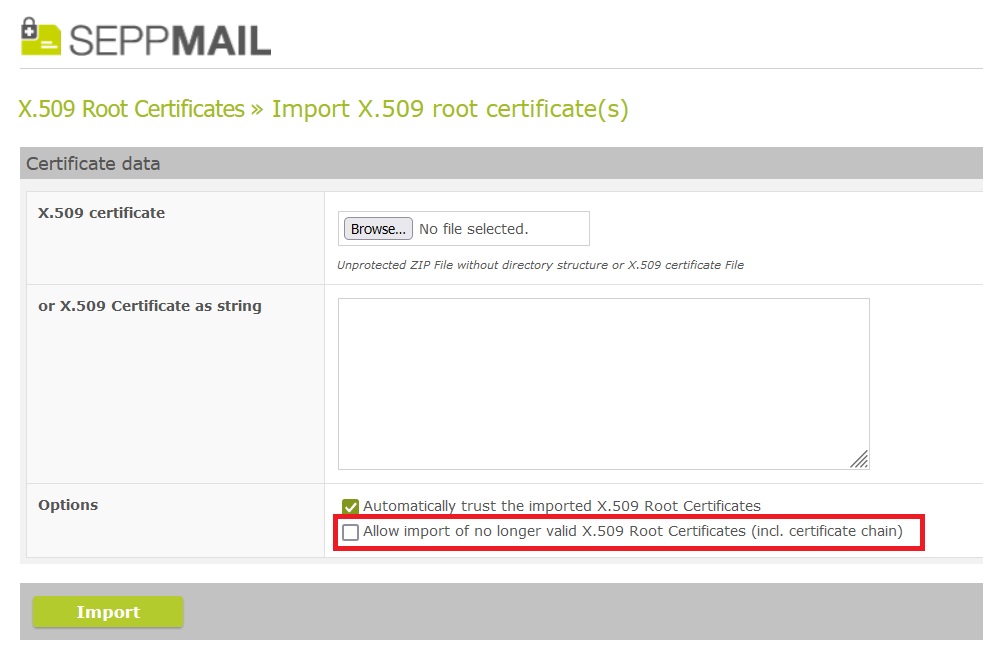
Allow import of no longer valid X.509 Root Certificates (incl. certificate chain)
REST API
Mail processing endpoint
- Internal Reference: 43779
- Issue Type: Feature
- Docs Link: none
The RestAPI now offers the endpoint "/mailprocessing/processmail".
You can use this to have a transferred mail processed by the RuleEngine and receive the processed mail(s) back together with the log and a list of the cryptographic procedures used.
GINA Domains
- Internal Reference: 19392
- Issue Type: Feature
- Docs Link: none
GINA domains can now be completely configured via the RestAPI. The missing items IDP, default recipients and languages have been added.
Mail Processing
- Internal Reference: 19395
- Issue Type: Feature
- Docs Link: none
You can now use the RestAPI to make all the settings that you can make in the Admin GUI under Mail Processing.
(Not to be confused with the /mailprocessing/processmail endpoint above, which can be used to have a mail processed by the RuleEngine.)
Partial Match Parameter for GINA Users
- Internal Reference: 45176
- Issue Type: Maintenance
- Docs Link: none
This is a small change to the "/webmail/user" endpoint of the RestAPI for the GET request. Previously, if you were looking for a user, you had to enter the exact email address or the full name.
Now it is possible to search for a partial match with the * wildcard character. If you are looking for all SEPPmail users, you could enter the mail address "*@seppmail.ch". The same applies to names and mobile numbers.
Statistics on SMS usage for GINA
The RestAPI now offers the endpoint "/webmail/user/smshistory".
This can be used to retrieve detailed information about the SMS sent per GINA user. In the seppmail.cloud, this is mainly important for billing. In the Admin GUI, you can specify a retention time so that entries older than the retention time are deleted from the SMS history. As always, empty or 0 means no deletion of the SMS history.
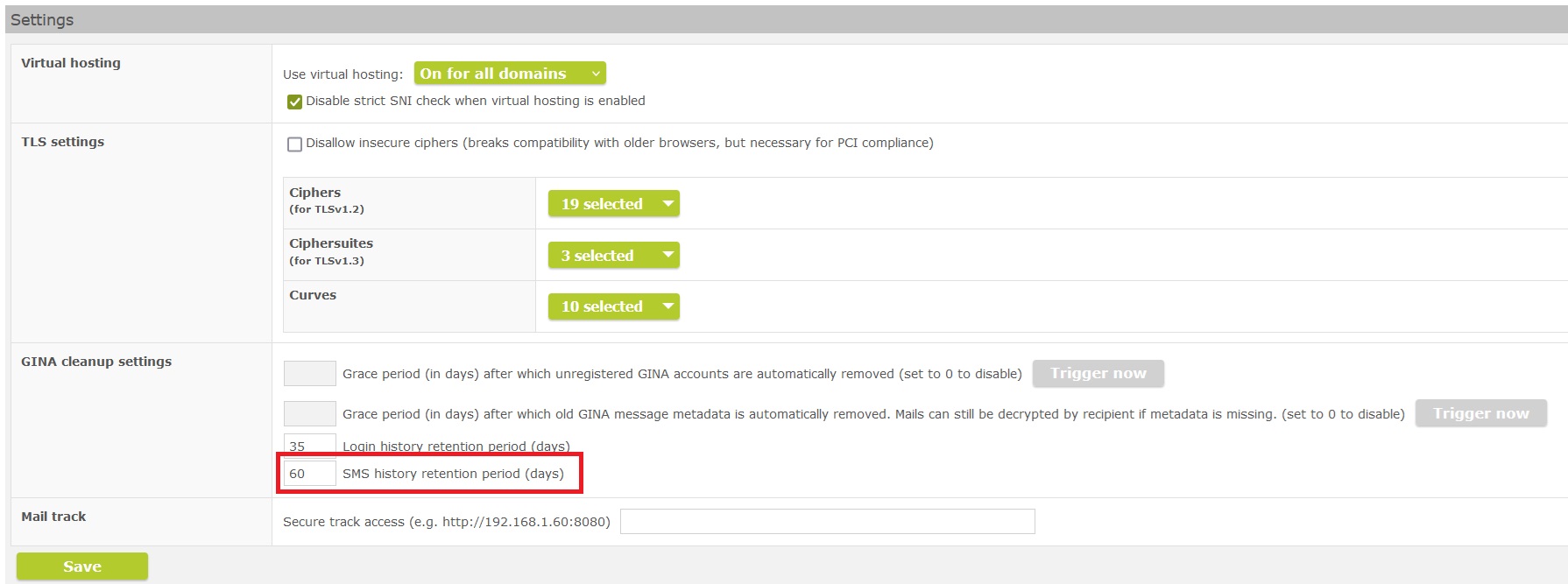
Set SMS history retention time in the GINA Cleanup Settings
Webmail (GINA)
UTF8 encoding for eCall SMS messages
- Internal Reference: 49327
- Issue Type: Bug
- Docs Link: none
Some SMS services want the messages to be sent in UTF-8, while others want them to be sent in ISO. The default of the SEPPmail Gateway is ISO. Since we do not impose any restrictions on the providers, it happens as in this case that a provider that we did not yet know uses UTF-8. We have now added eCall to the list of SMS providers and transfer the message to them in UTF-8.
Support multiple seppmailSymmkey per GINA account
- Internal Reference: 46558
- Issue Type: Feature
- Docs Link: none
With this issue, the option of storing several keys per GINA account is created. These keys are not displayed and cannot be changed or deleted etc. but are used exclusively in the background for the encryption and decryption of GINA messages.
However, if the GINA accounts of two customizers were to be combined, only one of the keys would have been used in the past, meaning that all GINA messages encrypted with the other key would never have been readable again. Thanks to the possibility of having several keys, this will no longer be a problem in future.
Sign Password Reset E-Mails
- Internal Reference: 42537
- Issue Type: Feature
- Docs Link: none
Password reset mails from GINA are now signed if key material is available.
Statistics on SMS usage for GINA
The RestAPI now offers the endpoint "/webmail/user/smshistory".
This can be used to retrieve detailed information about the SMS sent per GINA user. In the seppmail.cloud, this is mainly important for billing. In the Admin GUI, you can specify a retention time so that entries older than the retention time are deleted from the SMS history. As always, empty or 0 means no deletion of the SMS history.

Set SMS history retention time in the GINA Cleanup Settings
Use hard encryption for Cached Links to prevent SSL certificate mismatches
- Internal Reference: 48956
- Issue Type: Maintenance
- Docs Link: none
To encrypt the data for cache mode, we use a function that has two different modes.
The one activated for the cache mode until now used the local SSL key, i.e. the one for the Admin GUI etc., to generate a password for the cache mode encryption. This had the effect that this cache link could only be read on this system with this SSL key.
In a cluster where each cluster member may have its own SSL key, this could lead to a situation where only one of the systems could process the cache link correctly. On the other member, the cache link could not be opened.
For this reason, we have now switched to the second mode of the encryption function for the cache mode, which is called "hard". This mode uses keys that are stored in the database and are therefore available to all cluster members. Each GINA domain has its own keys, which can also be transferred during a migration. The keys are also regularly renewed.
--- end of document ---




















