Tip: All changes are tracked in the Gateway documentation, see the information in the last row of the documentation agreement.
For the latest 14.1 releases, see https://downloads.seppmail.com/extrelnotes/141/ERN14.1.html
For the latest 14.0 releases, see https://downloads.seppmail.com/extrelnotes/140/ERN14.0.html
For the latest 13.1 releases, see https://downloads.seppmail.com/extrelnotes/131/ERN13.1.html
SEPPmail Gateway news via Statuspal As of July 2025, SEPPmail Secure E-Mail Gateway customers and partners can register for Statuspal messages under the link https://seppmail.statuspal.eu/#subscribe. Information about the Gateway is now also published here.
Release Date: January 27th, 2026
SEPPmail version: 15.0.2
Author: Birgit Grossmann
Previously, there was a problem when saving the TLS settings under "GINA Domains" if the option "Disallow insecure ciphers (breaks compatibility with older browsers, but necessary for PCI compliance)" was activated and ciphers were selected that were not permitted for this mode in the multi-select. This resulted in an error message stating that some of the selected ciphers were not permitted for PCI. Now, the unauthorised ciphers are simply ignored and removed from the selection, allowing to save without any problems.
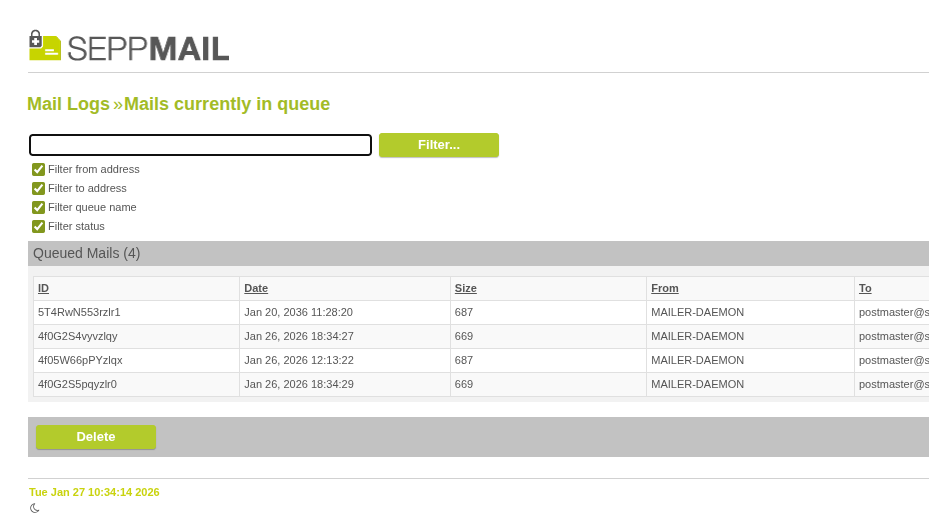
Under Logs > "Mails currently in queue", you can now filter by From, To, Queue name and Status.

Filters for "Mails currently in queue"
Until now, frontend systems have not cleaned up/deleted the cached emails in GINA Cache mode. As a result, the local directory continued to grow. Starting with version 15.0.2, the local cache will also be cleaned up on frontend systems.
There was an error in the restore script for the daily snapshots in the event of a full snapshot restore. This has been fixed now.
When sending the daily backup and daily digest, we have not previously set the envelope sender for sending. This led to problems, especially in ExO environments. We now set the envelope sender to the postmaster (which must of course be configured).
Until now, we have not explicitly set the key usage of the CA certificate when creating the local CA. However, this causes problems for communication partners who must communicate in a BSI-compliant manner, as setting the keyUsage is a prerequisite here. Starting with version 15.0.2, the key usage for newly issued CAs will be set to "keyCertSign, cRLSign".
Only SwissSign Gold products require a first and last name, this has been adjusted now in the SwissSign MPKI Connector.
There was a problem in the REST API with targeted access to the key material of specified users or domains. If the user or domain was not found, all data was returned. Now we return an error message stating that the user or domain does not exist.
When setting customer settings in the REST API, there was a problem in that it was not possible to set empty values for maximumEncryptionLicenses and maximumLFTLicenses, but only positive integers. This meant that it was not possible to allow the customer an unlimited number of licences, but only a fixed number. Now it is possible to leave the value empty again and thus remove the licence limit.
A security-critical change in 15.0.1 caused incorrect processing, mainly when decrypting HIN-encrypted emails, because reprocessing the headers caused the rule set to select the wrong path for the next rules and marked decrypted emails as "encryption failed". This has been fixed now.
In a change in 15.0.1, which introduced more compliant parsing of email addresses, there was an error whereby we MIME-decoded email addresses and then parsed them. This is incorrect and led to "invalid email address" error messages. This has been fixed now.
Previously, when logging the size of the email, the size of attachments uploaded via bypass upload was not included. These are the attachments uploaded by the Outlook add-in for LFT. This is now logged.
Every change to the headers of an email is now logged - deleting, adding, replacing. This means that the customer can always see in the log when which headers were set. (Only the transfer of headers from decrypted emails is not yet logged.)
In the code for renewing S/MIME certificates issued by the local CA, there was an error that prevented automatic renewal if the MPKI connector was not also configured for the domain in question. We have now removed this dependency and the renewal of local certificates is working again.
There were some wrong translations in the GINA GUI, mostly in French. These are fixed now.
We used to have a mechanism to determine whether we were on a mobile device in a proper browser or just in an HTML viewer. However, this mechanism is no longer reliable, so we have removed it. But since all old GINA emails from before the removal still rely on one of the removed files, we have added it back, and the old GINA messages should now be readable again without any problems.
In version 15.0.0, we added logging of the X-Forwarded-For header for GINA. We now log this header for all web accesses.
During a penetration test, it was noticed that forms could be embedded in GINA emails. Form tags in HTML are now removed using "defang" when displayed in the GINA GUI.
In the GINA account detail views, "floating" was displayed for the time zone under "Account info". Now the time zone as configured under "System" is used.
We had the problem that when a large number of entries for the GINA cache mode were stored on an S3, the time required to retrieve and display a cached email was very high. However, since S3 only allows prefix searches, we had to change the naming of the cache entries so that access can now take place much faster.
Texts were added twice in GINA mail creation. This has been fixed now.
Release Date: January 6th, 2026
SEPPmail version: 15.0.1
Author: Birgit Grossmann
We no longer issue a warning about the absence of an LFT disc on hardware systems.
If you previously used the master template settings for the extended settings in the settings of a GINA domain and deactivated this for a domain-specific setting, you could save invalid settings that later led to malfunctions. This is no longer possible.
With older Nutanix installations, there is a problem with the vioscsi driver, which leads to very long boot times. For this reason, it is actually possible to disable the vioscsi driver under Nutanix. The problem was that if someone switched to Nutanix from another platform, they previously could not disable the vioscsi driver beforehand. This is now possible.
As there were repeated UTF-8 encoding problems with SMS messaging, we have added a new option "Use UTF encoding" that allows to define whether data should be transferred as UTF-8 or not.
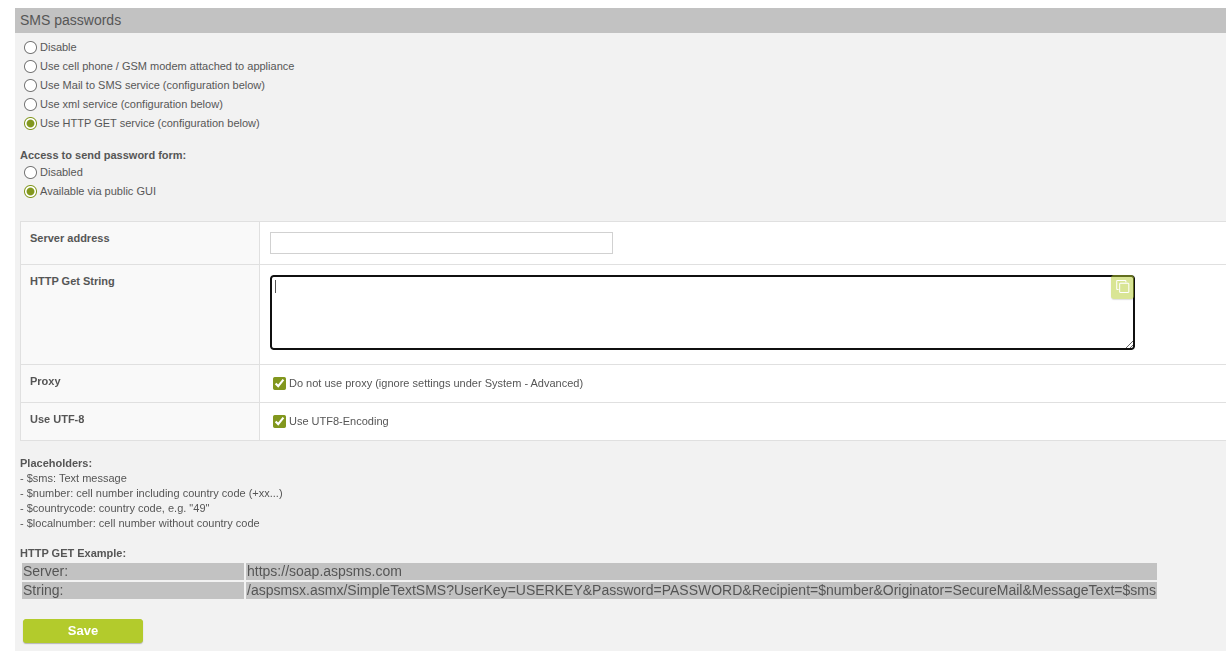
Use UTF encoding
Mainly in Azure environments, there was the problem that after about 10 minutes, the support connections were no longer usable, even though the connection was still visible on the SEPPmail side. We have now adjusted the parameters for the SSH connection so that it is automatically tested and kept open by the appliance.
There are two cron jobs that renew or revoke certificates when necessary. Previously, these wrote to the syslog without any recognisable affiliation. Now, the log entries for these jobs have the corresponding prefixes ‘Autorenew’ and ‘Autorevoke’, making them easy to filter.
In the code that detects on a frontend system that the backend is no longer accessible and switches to another configured backend, there was an error that prevented the desired behaviour. This has now been fixed and works as intended.
There was an error when manually importing a licence. This is fixed now.
Previously, the SMTPd.pl process, which receives emails from Postfix, passed them to the RuleEngine and then forwarded them, writing its error and debug output to /tmp. This meant that important information for error analysis was sometimes lost during a restart. Now the process writes to /var/log/SMTP.err, which is persistent.
The mail log is rotated at least once a day. This allows file-based logging to be filtered by day.
In the rare case that there were no emails in the mail log, DB-based logging incorrectly assumed that there was an error. Now, a corresponding message is displayed indicating that there are no entries.
When processing the mail log and adding this data to the database in DB-based logging, there were rare instances where the file used to prevent the same process from being called at the same time (i.e. a lock file) was not deleted after termination. This prevented the process from ever running again (until the next reboot). Now the file is deleted cleanly.
To enable DB-based logging, we have now incorporated a test to check in advance whether there is sufficient disk space available. If not, DB-based logging will be prevented from being activated.
There were problems with the CN when issuing domain certificates using the SwissSign MPKI Connector. The CN of a certificate may only be a maximum of 64 characters long. Some domains are so long that this limit is exceeded. We are now trying to shorten them and if that does not help, we will refer you to SwissSign support.
In version 15.0.0, the automatic revocation of certificates for inactive users was introduced. However, as some customers wish to retain these certificates, we have now made this configurable under "Users" > "Advanced Settings" with the option "Automatically revoke certificates of inactive users".
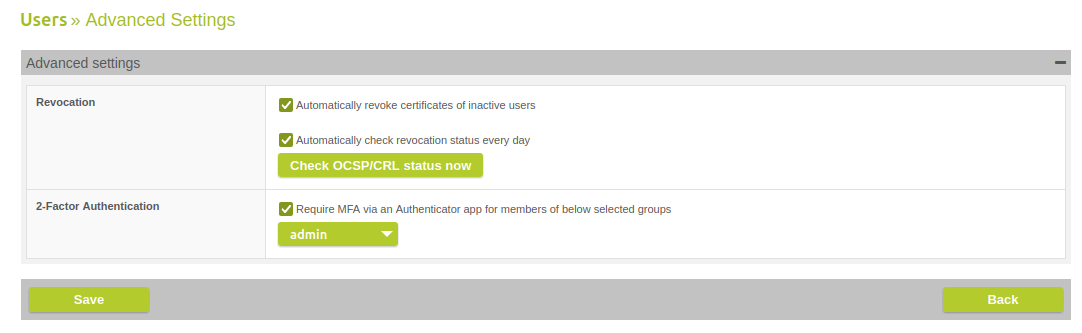
Automatically revoke certificates of inactive users
There was/is a problem with umlauts using the Harica MPKI Connector. This is likely a problem on Harica's side, but until they resolve it, we implemented the setting "Umlaut Transliteration" to transliterate special characters and umlauts to avoid non-ASCII characters.
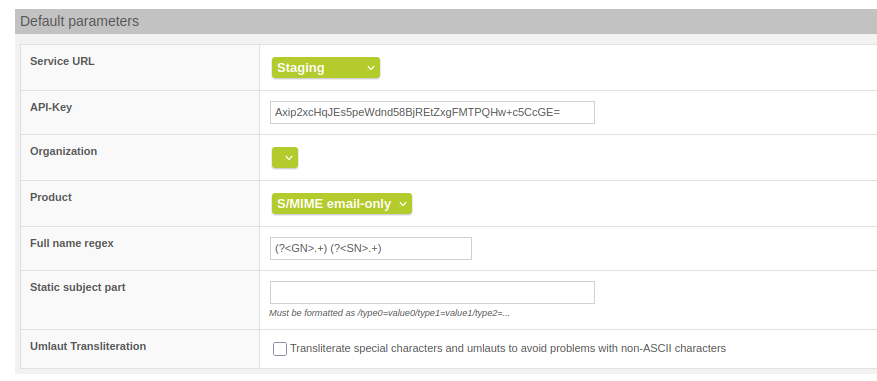
Transliterate special characters and umlauts to avoid non-ASCII characters
In the Nagios tests of local services, the static telnet test was previously used to check whether Postfix was still working. However, this led to errors. For this reason, we now use the designated smtp test.
Previously, authentication via the submission port was only considered sufficient for outgoing emails. Now this is also the case for internal emails.
When displaying the generated Ruleset in the Admin GUI, there was a problem whereby certain parts of if-else if-else branches were displayed incorrectly, especially when the conditions were negated. Internally, however, the Ruleset was correct; only the display was incorrect, and this has been fixed now.
With the ticket, a special treatment for the Incamail test mail address mta@check.incamail.ch has been added in the Ruleset. Otherwise, an attempt would be made to process an email to mta@check.
We received a very comprehensive security review (thank you to Andris Suter-Dörig working under the supervision of Matteo Scarlata and Prof. Kenny Paterson from the Applied Cryptography Research Group at ETH Zurich). This ticket closes the critical vulnerabilities and some of those classified as high.
Further vulnerabilities will be closed in upcoming releases.
Previously, we only allowed the import of pure RSA or EV X.509 certificates. Flavours such as RASSSA-PSS were rejected. Now we allow any type of RSA and EC.
It was recognised as problematic when both the password and the account to be used are specified in a text message ("for %s"). For this reason, we have adjusted the pwsend_smstext text so that it no longer contains the account. If customers have already made adjustments themselves in these translations, they must take action and check their texts.
For caching GINA messages on external S3 storage, we now omit the determination of free space on the S3, as this information is not available for S3. This greatly speeds up the processing of GINA emails in cache mode, especially when there are already a large number of emails in the cache.
The company logo is now also displayed in pwsend.app, the web application that sends the GINA password via text message.
With this ticket, we have fixed a bug that prevented the login history of GINA accounts from being cleared.
Release Date: November 4th, 2025
SEPPmail version: 15.0
Author: Birgit Grossmann
The "Save and apply all" button in the Advanced System Settings did not ensure that the changes were actually saved and applied. This has been fixed now.
Under "Managed Domains" it is now possible to regenerate DKIM and ARC keys. In addition, the Master ARC key can also be regenerated under "Mail System".
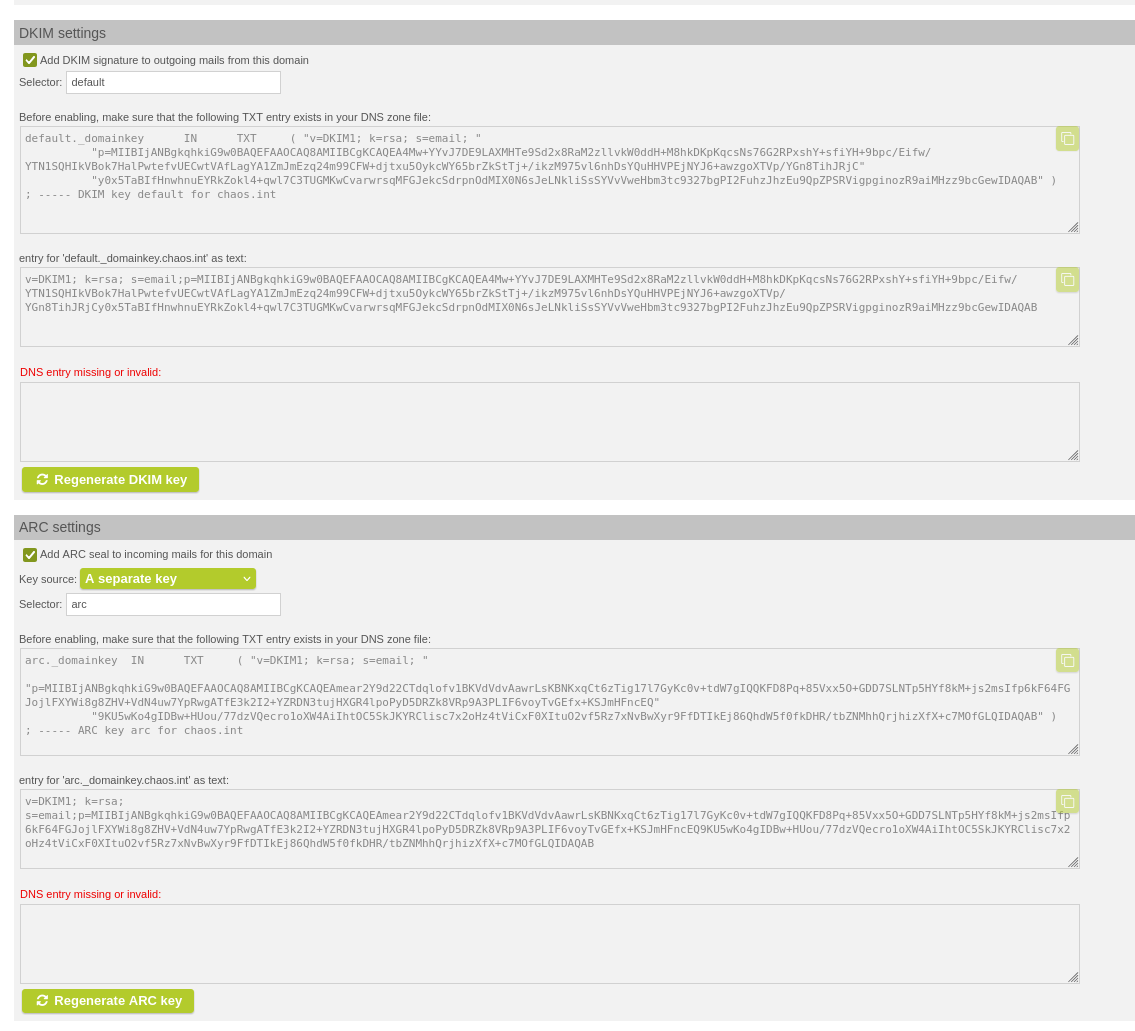
Regenerate DKIM Key
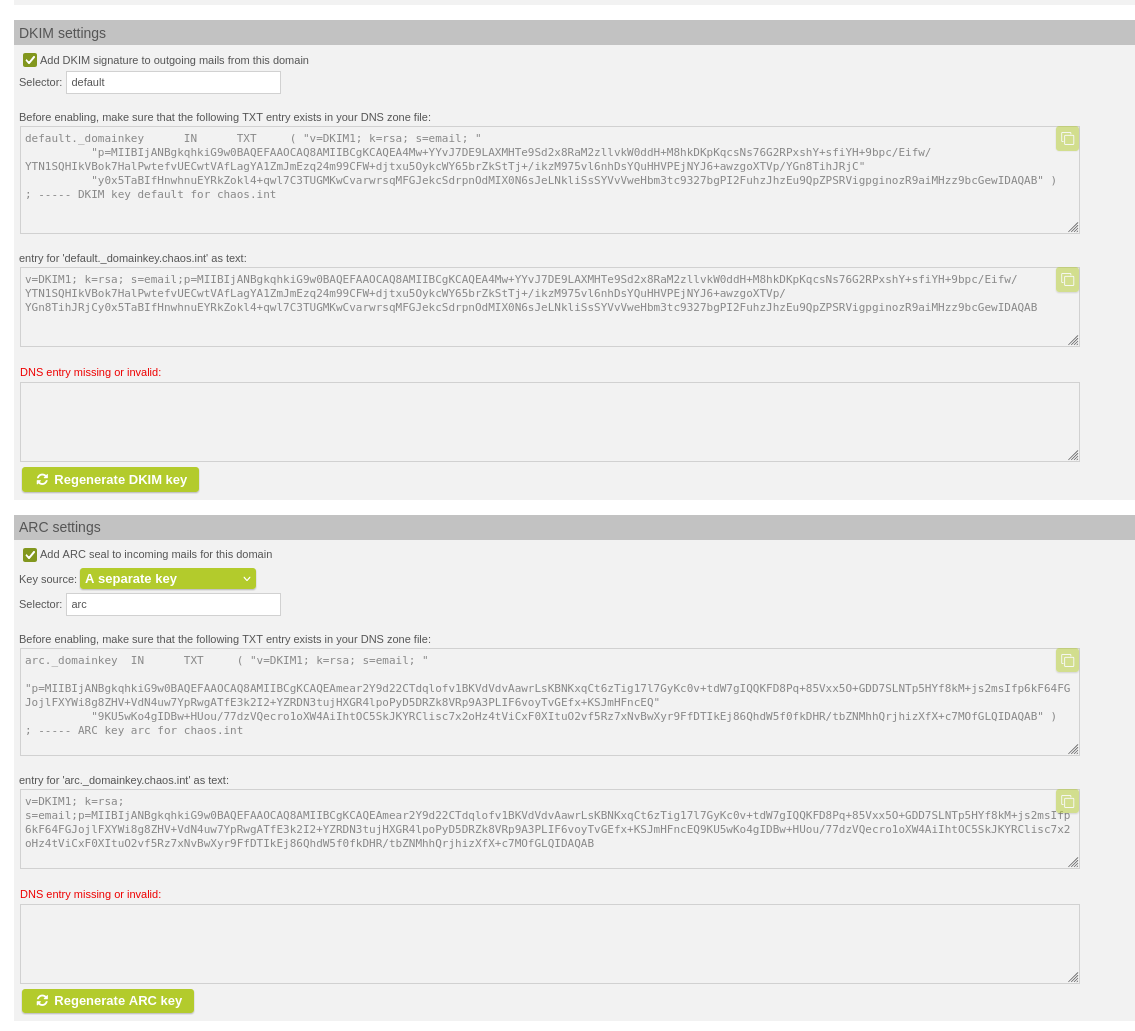
Regenerate ARC Key
When the SEPPmail Gateway performs its revocation checks for root CA certificates, it sets the status to "untrusted" if the CA certificate has been revoked.
The file.app, which we use to bypass the upload of LFT attachments, has not previously returned any error messages when an upload was unsuccessful. As a result, users were never able to tell whether the upload had been successful or not. From version 15.0.0 onwards, we have error codes with meaningful error descriptions.
The X-Forwarded-For IP address is now logged in the Apache access log for the GINA GUI. This also gives us information about whether there is a proxy in front of the system that sets the HTTP header.
By default, the setting for "Verify recipient addresses using SMTP lookups" under "Mail System" is now inactive (not checked). The setting is therefore deactivated for new installations.
Under "Mail System", you can disable client certificate verification in the submission port settings. This also means that Postfix no longer transmits the list of subjects of the root CA certificates, which causes problems in some Exchange installations because the list is too large.
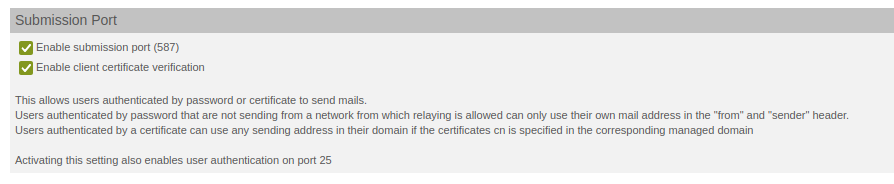
Enable or disable client certificate verification
For SwissSign MPKI, the specification of GivenName and Surname is only necessary for Gold products. Both values are therefore only required for Gold products, and a corresponding error message is displayed if the two values cannot be determined for the Gold products.
SEPPmail Gateway now offers a REST connection to the PKI of SwissSign.
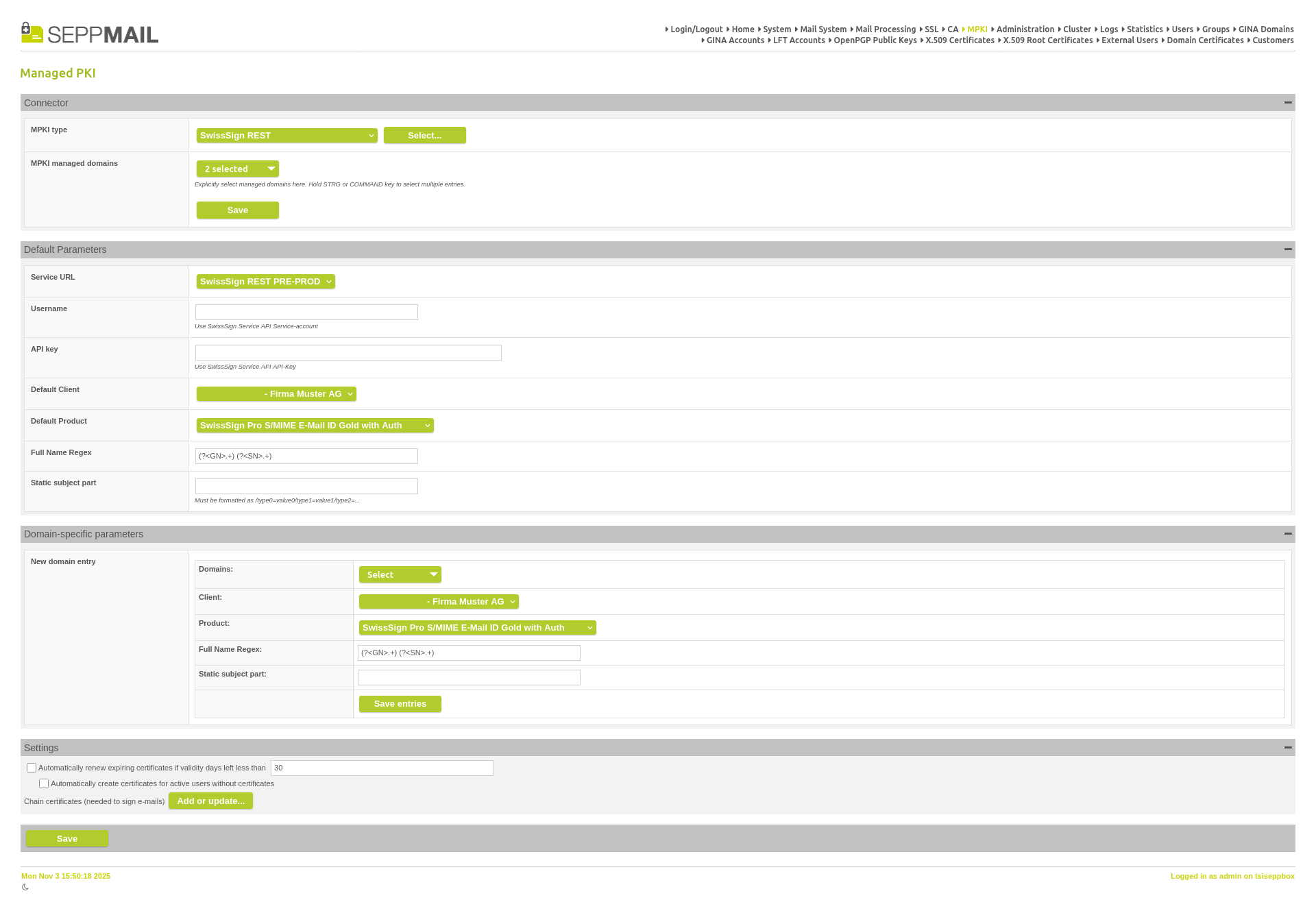
New SwissSign REST MPKI connector
The new Harica MPKI connector replaces the no longer functional DFN connector.
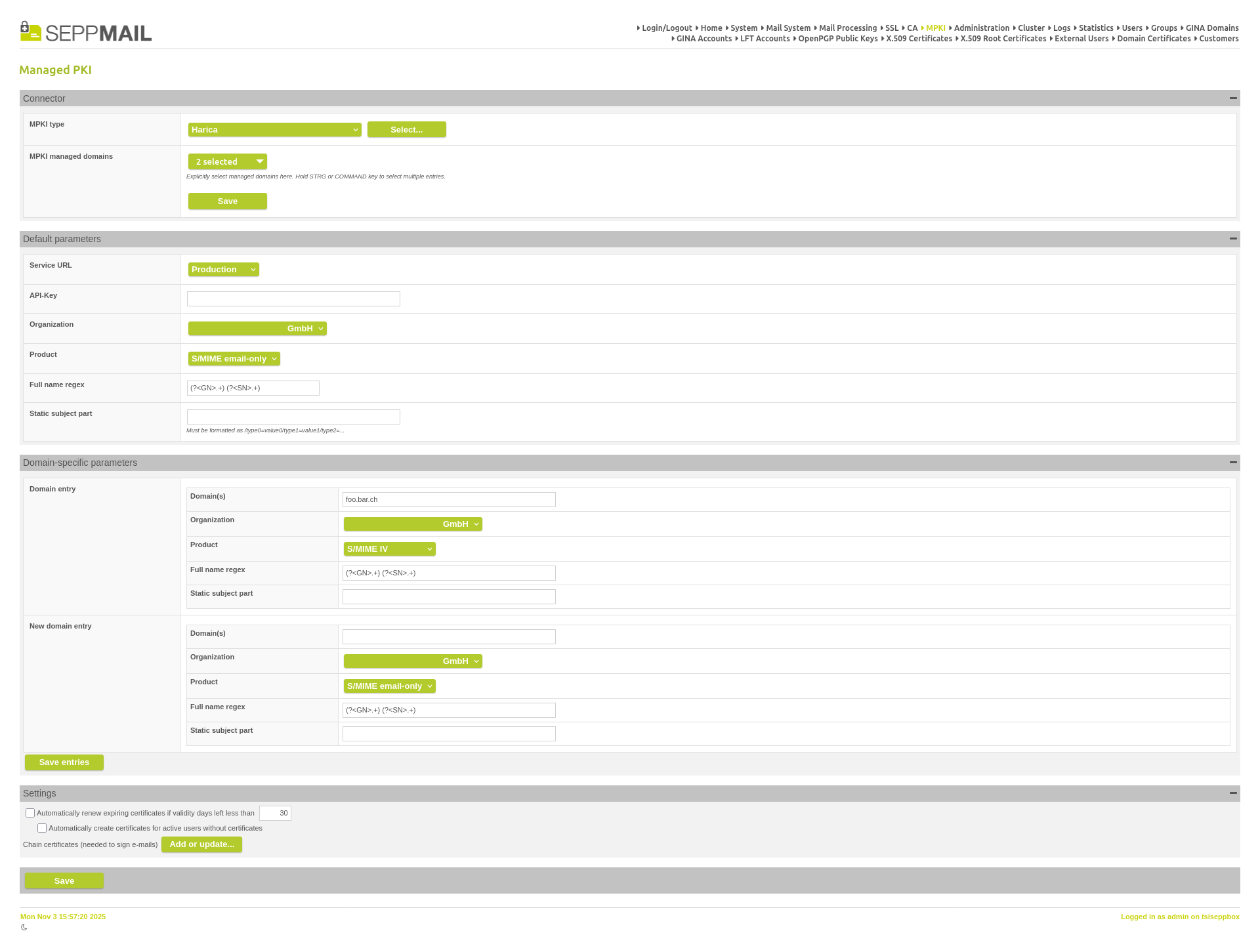
New Harica MPKI connector
If the classic SwissSign MPKI Connector is used (not the new SwissSign Rest MPK Connector), it can now be used to issue domain certificates for managed domains.
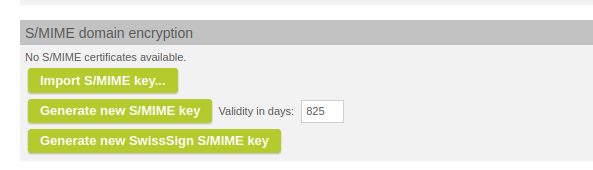
Generate new SwissSign S/MIME Key
If a user's licence is revoked, either manually or after 3 months of inactivity, their S/MIME certificates will be revoked from version 15.0.0 onwards.
Previously, there was a problem that if a customer was exported from one appliance and then imported onto another appliance, deleting the customer on the original appliance would revoke all certificates belonging to the customer's users. This would also render all user certificates imported onto the new appliance useless. Now, when deleting a customer, you can choose whether or not to revoke the certificates or the users. Revocation is disabled by default.
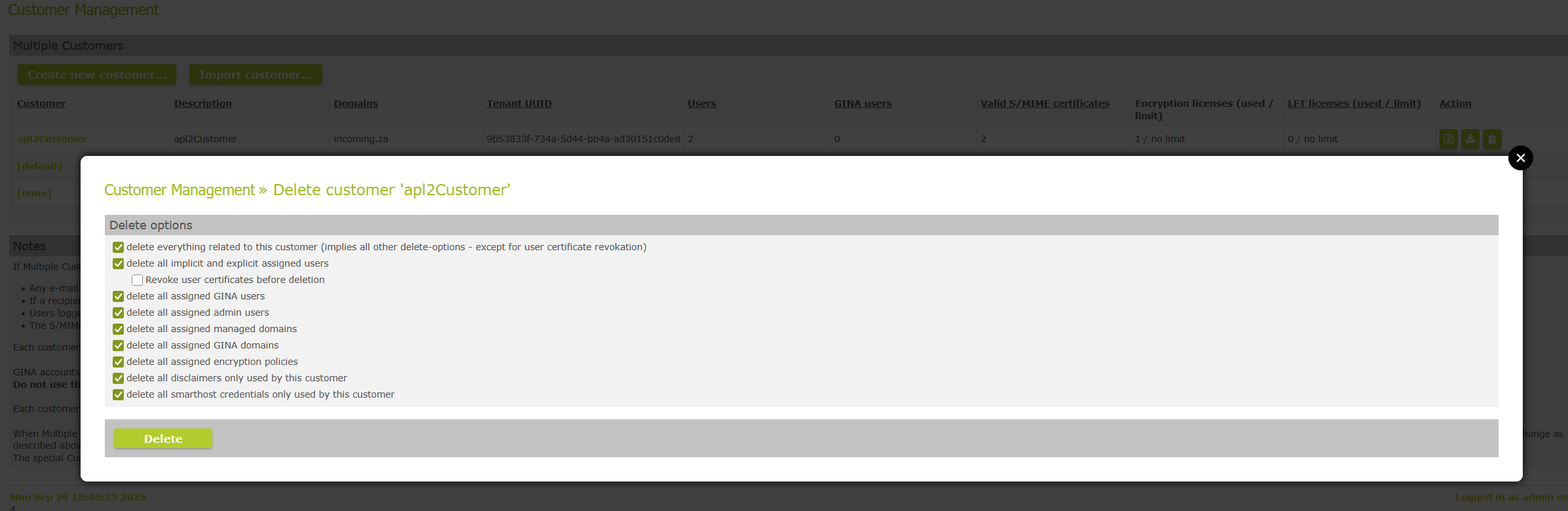
Revoke user certificates before deletion
There was a discrepancy between the number of licensed users in the customer overview and the customer detail view. This has been fixed now.
Previously, the use of managed domains was not comprehensively searched for when they were deleted. This meant that some components retained the already deleted managed domains in their data. These references are now correctly cleared up.
It is now possible to manage encryption policies via the RestAPI.
Backups from non-multi-customer appliances (extension .bak) can now be imported as a new customer.
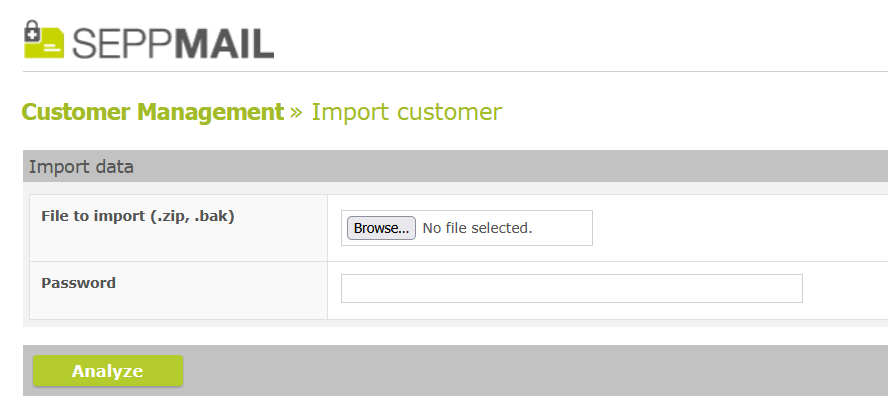
Import customer from Backup file
Our internal CMS module, which handles encryption, decryption and signatures, has so far been very complicated and memory-intensive. We are now using a more elegant approach, which reduces memory consumption considerably and is a little faster.
Previously, some headers were only written to the email via the RuleSet. This meant that these headers were not present in a self-written RuleSet, which in turn could lead to problems in the M365 environment, as the connectors created by our PowerShell module expect certain headers. These headers are now added directly by the RuleEngine functions.
There are two new functions for the RuleEngine that allow you to turn an email into an LFT message or revert an LFT message to an email. The functions are called make_lft and revert_lft, have no arguments, and return a corresponding value depending on success or failure, so that they can also be used in if conditions.
The new RuleEngine function getusetattr( “ATTRIBUTE_NAME”, “VARIABLE_NAME” ) is available. It has two required parameters: one is the user attribute to be queried and the other is the variable to which the value should be written. The function returns true if it was successful, so it can also be used in IF conditions.
An error in the code meant that changes to the language settings of a GINA domain, i.e. the texts used in the language, were not applied. This has been fixed now.
When GINA user authentication against the appliance's internal database was enabled, failed login attempts were not logged, meaning that users were never locked out after reaching the maximum number of unsuccessful login attempts. This has been fixed now.
The option "Certificate login" in the GINA settings has been removed.
--- end of document ---